Nokia 4A0-C01 - Nokia NRS II Composite Exam
Which of the following about Fast Reroute node protection tunnels is FALSE?
Which of the following statements is FALSE regarding 6VPE?
Click on the exhibit.

An LDP tunnel is established on R1-R2-R4-R6 because the link between routers R3 and R6 is down. With the LDP-IGP Sync feature enabled, what happens immediately after the link is restored?
Which of the following about IS-IS Traffic Engineering on an Alcatel-Lucent 7750 SR is FALSE?
Which of the following statements best describes a route target?
Epipe services do no consume any MAC resources because MAC learning is disabled.
Click on the exhibit.
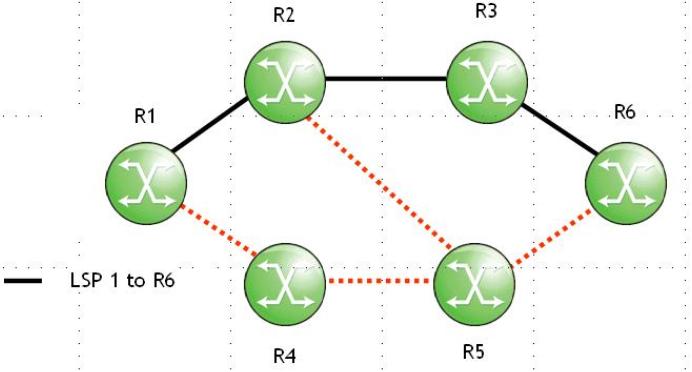
When router R1 forwards a PATH message to router R2, which of the following about the PATH message's IP header is TRUE?
What is a key benefit of a VPLS service?
What can the sdp-ping command be used for? (Choose 2)
Which of the following most accurately describes the default behavior of a VPLS regarding the handling of a tagged frame at the ingress of SAP 1/1/1:100?
Which of the following about Fast Reroute link protection tunnels is FALSE?
Which LSA type is used for OSPF-TE?
Which of the following statements best describes the flooding of traffic on a PE when traffic is received on a SAP?
Which of the following commands is used in an RSVP signaled MPLS tunnel to validate the path MTU based on signaling across the LSP?
Which of the following defines a SAP that will select frames with an outer tag of '4' and ignore any inner lag on a Q-in-Q encapsulated port?



