VMware 5V0-41.21 - VMware NSX-T Data Center 3.1 Security
An administrator has configured a new firewall rule but needs to change the Applied-To parameter. Which two are valid options that the administrator can configure? (Choose two.)
Which two are used to define dynamic groups for an NSX Distributed Firewall? (Choose two.)
Which two statements are true about NSX Intelligence? (Choose two.)
Refer to the exhibit.
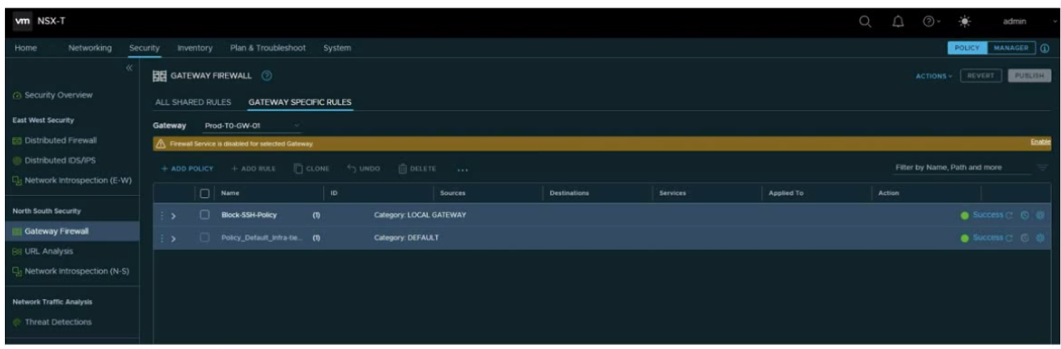
An administrator configured a firewall rule on their Edge Gateway to allow access to web servers.
What is missing in the Gateway Firewall policy to have the firewall rule applied?
Refer to the exhibit.
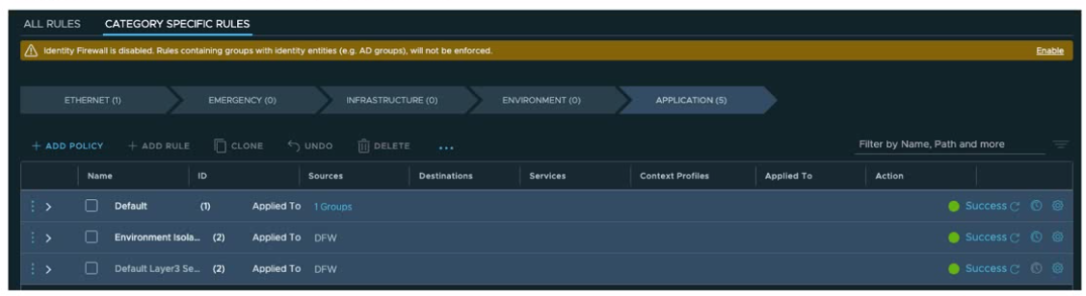
An administrator needs to configure a security policy with a firewall rule allowing a group of applications to retrieve the correct time from an NTP server. Which is the category to configure this security policy and firewall rule?
An NSX administrator has been tasked with deploying a NSX Edge Virtual machine through an ISO image.
Which virtual network interface card (vNIC) type must be selected while creating the NSX Edge VM allow participation in overlay and VLAN transport zones?
Which of the following describes the main concept of Zero-Trust Networks for network connected devices?
A security administrator is verifying why users are blocked from sports sites but are able to access gambling websites from the corporate network. What needs to be updated In nsx-T to block the gambling websites?
Which esxcli command lists the firewall configuration on ESXi hosts?
A Security Administrator needs to update their NSX Distributed IDS/IPS policy to detect new attacks with critical CVSS scoring that leads to credential theft from targeted systems.
Which actions should you take?



