Cisco 600-660 - Implementing Cisco Application Centric Infrastructure - Advanced (600-660 DCACIA)
What is a design implication for Cisco ACI using an application-centric approach?
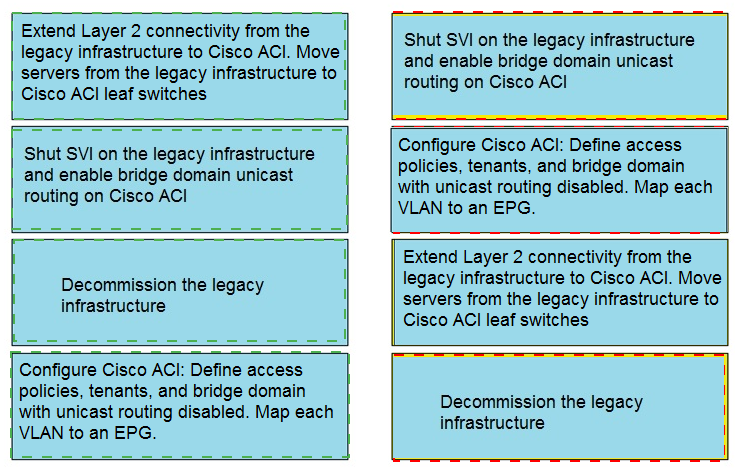
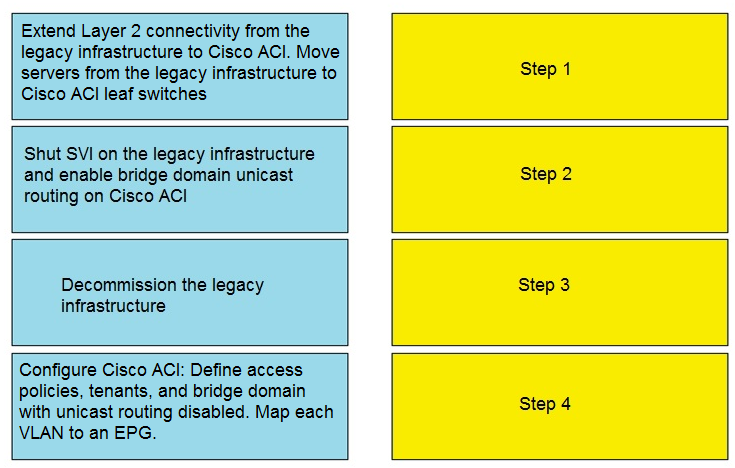
An engineer must migrate servers from a legacy data center infrastructure to a Cisco ACI fabric. Drag and drop the steps from the left into the order that they must be completed on the right to ensure the least amount of downtime.
Where are STP BPDUs flooded in Cisco ACI fabric?
Refer to the exhibit.
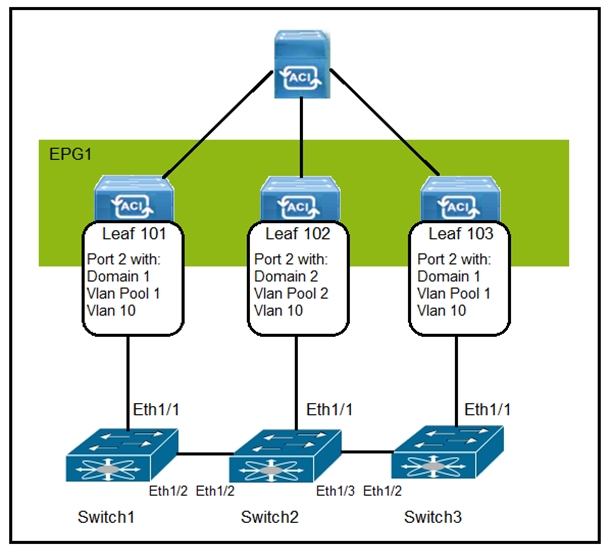
How are the STP BPDUs forwarded over Cisco ACI fabric?
An engineer must limit local and remote endpoint learning to the bridge domain subnet. Which action should be taken inside the Cisco APIC?
Which two actions are the Cisco best practices to configure NIC teaming load balancing for Cisco UCS B- Series blades that are connected to the Cisco ACI leaf switches? (Choose two.)
What does the VXLAN source port add to the overlay packet forwarding when it uses the hash of Layer 2, Layer 3, and Layer 4 headers of the inner packet?
An organization migrates its virtualized servers from a legacy environment to Cisco ACI. VM1 is incorrectly attached to PortGroup IT|3TierApp|Web.
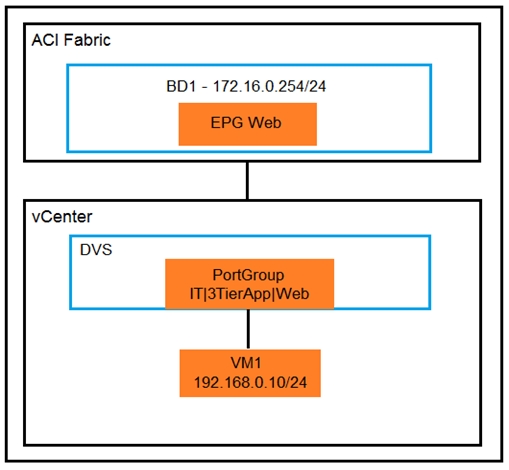
Which action limits IP address learning in BD1?
An engineer designers a Cisco ACI Multi-Pod solution that requires a pair of active-standby firewalls in different pods for external connectivity. How should the firewalls be implemented?
An engineer configures a new Cisco ACI Multi-Pod setup. Which action should be taken for fabric discovery to be successful for the nodes in Pod 2?