Android AND-802 - Android Security Essentials
You must use permissions to prevent unauthorized access to your application data.
The Logcat window in Android Studio displays system messages, such as when a garbage collection occurs, and messages that you added to your app with the Log class. It displays messages in real time and keeps a history so that you can view older messages.
Content providers can help an application manage access to data stored by it or by other apps. They also provide a way to share data with other apps.
Any Android application can protect itself by declaring permissions that can be accessed by other applications. This can be achieved using the
The following image includes a code of permission group. Where this code will be written in the Android app?

Android stores cache files in the filesystem and sandboxes along with the application. Cache files are created under directory ……………………………………..
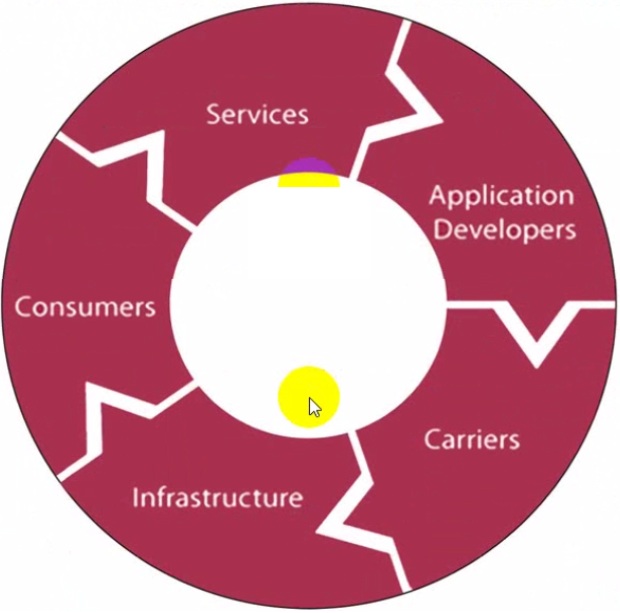
The following image includes some components which you must be aware of to learn about the complexity of the security issue and the fact that software developers can only deal with security issues within their own applications. These components belong to ………………….
A permission group is the concept of creating a group of all similar types of permissions, which will be presented together to the user during the installation time for approval.
The tag of a manifest file is a declaration for the whole application and each application component is declared in a sub-tag inside it.
Permissions required for an application to perform its operations are called application level permissions. Which are the types of application level permissions a developer can use? (Select two)



