Client Redirect is a Snowflake feature designed to support business continuity and disaster recovery in multi-account, multi-region architectures. When configured, it allows client applications to automatically connect to a secondary Snowflake account if the primary account becomes unavailable. This secondary account must be part of a configured failover group and promoted to act as the primary during a failover event.
The correct behavior of Client Redirect is to redirect client connections transparently to another Snowflake account—typically in a different region—where replicated data and objects are available and the account is acting as the primary (Answer D). This minimizes downtime and avoids the need for manual connection string updates across applications.
The feature does not simply provide alternate login URLs, nor does it dynamically route queries across multiple active accounts. It also does not automatically select the “closest†region; redirection follows the configured failover topology. For SnowPro Architect candidates, this question emphasizes understanding Snowflake’s native disaster recovery mechanisms and how Client Redirect integrates with failover groups.
=========
QUESTION NO: 47 [Security and Access Management]
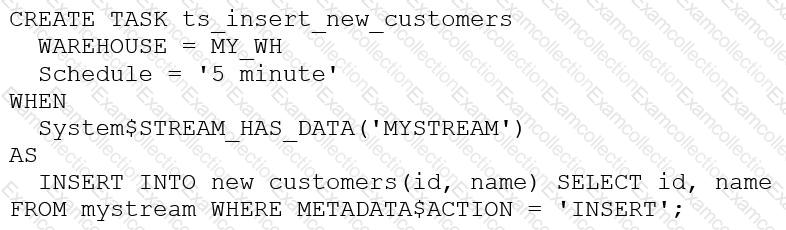
A call center processes sensitive PII and PHI data. Requirements:
Object owners and privileged roles must see sensitive columns.
Pre-tokenized data must be de-tokenized at query time.What should be used? (Select TWO).
A. Object tagging
B. Materialized views
C. External tokenization
D. Dynamic Data Masking
E. Role-Based Access Control (RBAC)
Answer: D, E
Dynamic Data Masking is a Snowflake security feature that conditionally masks or reveals column values at query time based on the executing role (Answer D). This allows privileged users (such as object owners or compliance roles) to see clear-text PII/PHI, while other users see masked or tokenized values. Because masking is evaluated at query time, it supports de-tokenization logic when the role is authorized.
Role-Based Access Control (RBAC) underpins this behavior by defining which roles are privileged and allowed to view unmasked data (Answer E). Masking policies are evaluated in the context of the active role, making RBAC essential for enforcing correct access.
Object tagging alone does not enforce access control. Materialized views duplicate data and do not support dynamic de-tokenization logic. External tokenization is not required when Snowflake masking policies can handle conditional reveal. This question tests SnowPro Architect knowledge of advanced column-level security and privacy controls.
=========
QUESTION NO: 48
(Skipped — no Question 48 in the original set)
=========
QUESTION NO: 49 [Snowflake Data Engineering]
A table contacts_data contains a VARIANT column with nested JSON data.
Which queries correctly retrieve the first name value "Snow"? (Select TWO).
A. SELECT o[customer][name][first]::STRING FROM contacts_data;
B. SELECT o['customer']['name']['first']::STRING FROM contacts_data;
C. SELECT o:['customer']:['name']:['first']::STRING FROM contacts_data;
D. SELECT o:Customer.Name.First::STRING FROM contacts_data;
E. SELECT o:customer.name.first::STRING FROM contacts_data;
Answer: B, E
Snowflake supports multiple syntaxes for accessing elements in VARIANT columns. Bracket notation with quoted keys is valid for object traversal, making option B correct. Dot notation with colon syntax is also valid and commonly used for readability, as shown in option E.
Option A is invalid because unquoted identifiers inside brackets are interpreted as column names, not JSON keys. Option C contains incorrect syntax combining brackets and colons. Option D is invalid because JSON key names are case-sensitive unless quoted, and the provided structure uses lowercase keys.
Understanding VARIANT traversal syntax is a core SnowPro Architect skill for semi-structured data handling and transformation.
=========
QUESTION NO: 50 [Cost Control and Resource Management]
An Architect is evaluating compute and storage costs related to performance optimization techniques.
Which Snowflake performance optimizations have storage costs associated with them? (Select THREE).
A. Rekeying
B. Materialized views
C. Clustering a table
D. Query Acceleration Service
E. Search Optimization Service
F. Multi-cluster virtual warehouse
Answer: B, C, E
Some Snowflake performance features require additional storage to maintain auxiliary data structures. Materialized views store precomputed query results and therefore consume storage (Answer B). Clustering a table can increase storage usage due to additional micro-partitions created during reclustering operations (Answer C).
Search Optimization Service builds and maintains search access paths that persist as additional metadata structures, incurring storage costs (Answer E). In contrast, Query Acceleration Service and multi-cluster warehouses affect compute usage only. Rekeying is a security operation and does not create separate storage structures.
This question tests SnowPro Architect understanding of cost tradeoffs between compute and storage when selecting optimization techniques.