Microsoft AZ-500 - Microsoft Azure Security Technologies
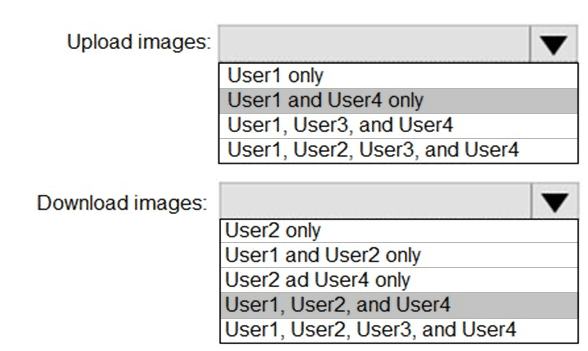
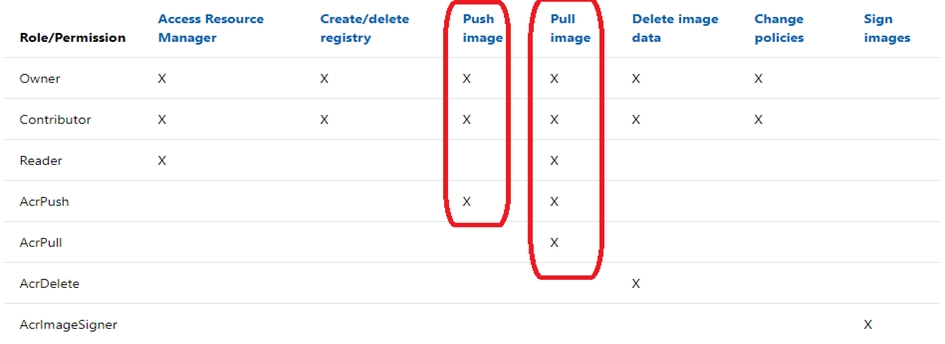
You have an Azure Container Registry named Registry1.
You add role assignment for Registry1 as shown in the following table.
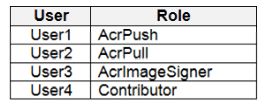
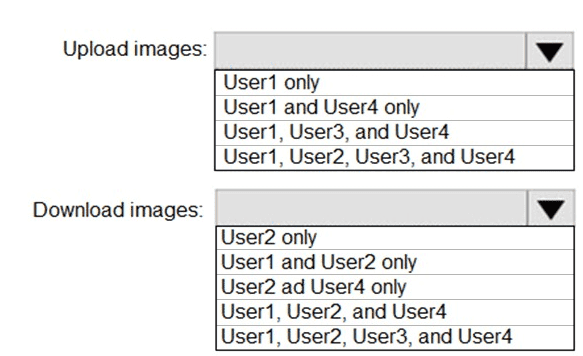
Which users can upload images to Registry1 and download images from Registry1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
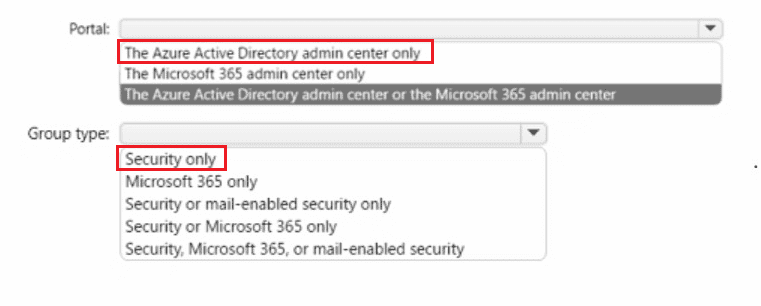
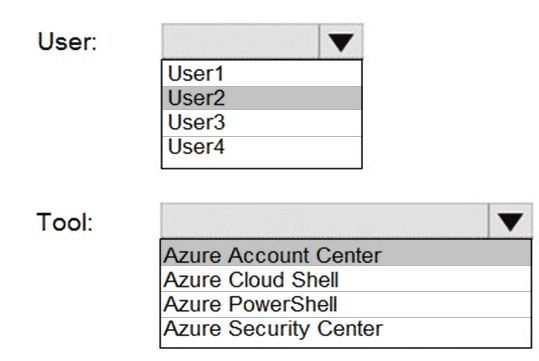
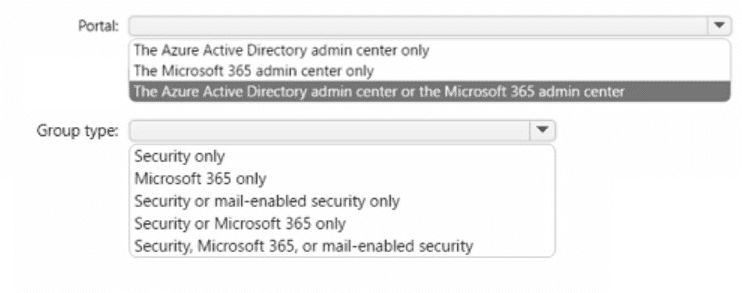
You have an Azure AD tenant named contoso.com that has Azure AD Premium P1 licenses.
You need to create a group named Group1 that will be assigned the Global reader role.
Which portal should you use to create Group1 and which type of group should you create? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point
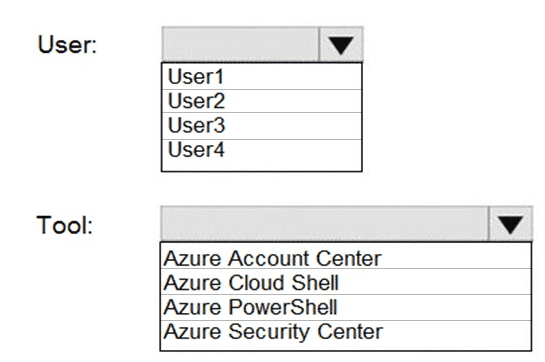
Your company has an Azure subscription named Subscription1 that contains the users shown in the following table.
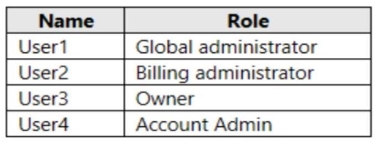
The company is sold to a new owner.
The company needs to transfer ownership of Subscription1.
Which user can transfer the ownership and which tool should the user use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have two Azure subscriptions named Sub1 and Sub2 that contain the virtual networks shown in the following table.
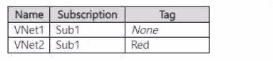
You have an Azure Virtual Network Manager instance named AVNM1 that has the following configurations:
* Management scope: Sub1
* Network groups:
* NetGrp1: Static membership that includes VNet1
* NetGrp2: Dynamic membership that has the following criteria: Tags that contain Red
* Security admin rule collection: SARule1
* Deployed to all Azure regions

You create two new virtual networks as shown in the following table.
Which virtual networks will have SARule1 applied?
You have an Azure subscription that contains the resources shown in the following table.
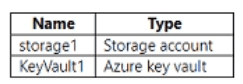
You need to configure storage1 to regenerate keys automatically every 90 days. Which cmdlet should you run?
You are testing an Azure Kubernetes Service (AKS) cluster. The cluster is configured as shown in the exhibit. (Click the Exhibit tab.)
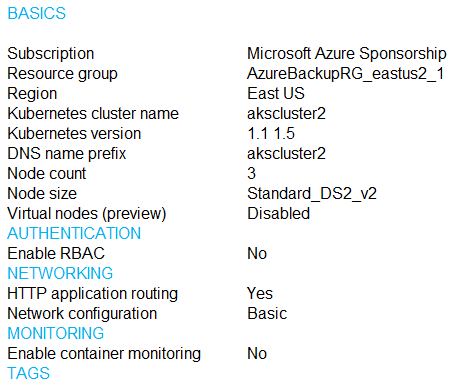
You plan to deploy the cluster to production. You disable HTTP application routing.
You need to implement application routing that will provide reverse proxy and TLS termination for AKS services by using a single IP address.
What should you do?
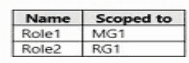
You have a management group named MG1 that contains an Azure subscription and a resource group named RG1. RG1 contains a virtual machine named VM1. You have the custom Azure roles shown in the following table.
The permissions for Role1 are shown in the following role definition file.
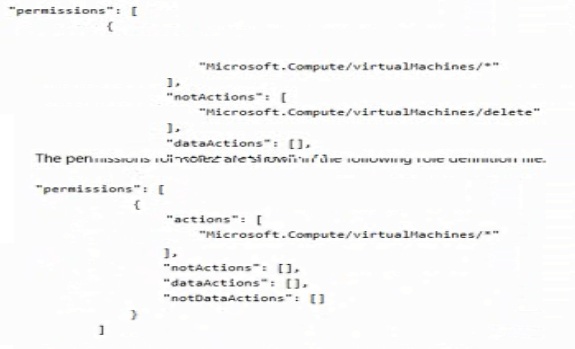
You assign the roles to the users shown in the following table.
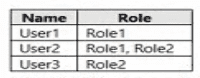
For each of the following statements, select Yes if the statement is true. Otherwise, select No
NOTE: Each correct selection is worth one point.
You have an Azure Storage account named storage1 that has a container named container1. You need to prevent the blobs in container1 from being modified. What should you do?
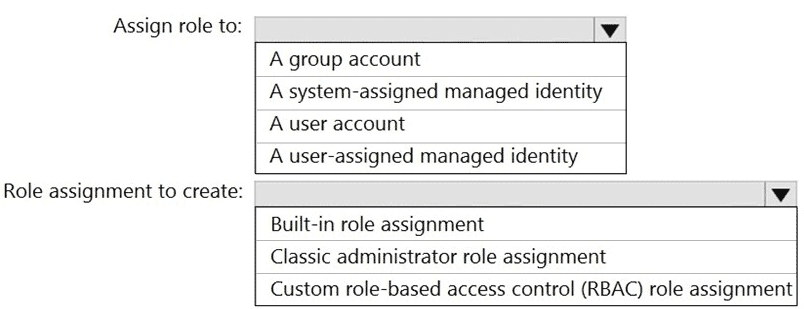
You plan to implement an Azure function named Function1 that will create new storage accounts for containerized application instances.
You need to grant Function1 the minimum required privileges to create the storage accounts. The solution must minimize administrative effort.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have an Azure subscription that uses Microsoft Defender for Cloud.
You have an Amazon Web Service (AWS) account named AWS1 that is connected to defender for Cloud.
You need to ensure that AWS foundational Security Best Practices. The solution must minimize administrate effort.
What should do you in Defender for Cloud?