Microsoft AZ-500 - Microsoft Azure Security Technologies
You need to delegate a user to implement the planned change for Defender for Cloud.
The solution must follow the principle of least privilege.
Which user should you choose?
You have an Azure Active Directory (Azure AD) tenant that contains the users shown in the following table.
From Azure AD Privileged Identity Management (PIM), you configure the settings for the Security Administrator role as shown in the following exhibit.
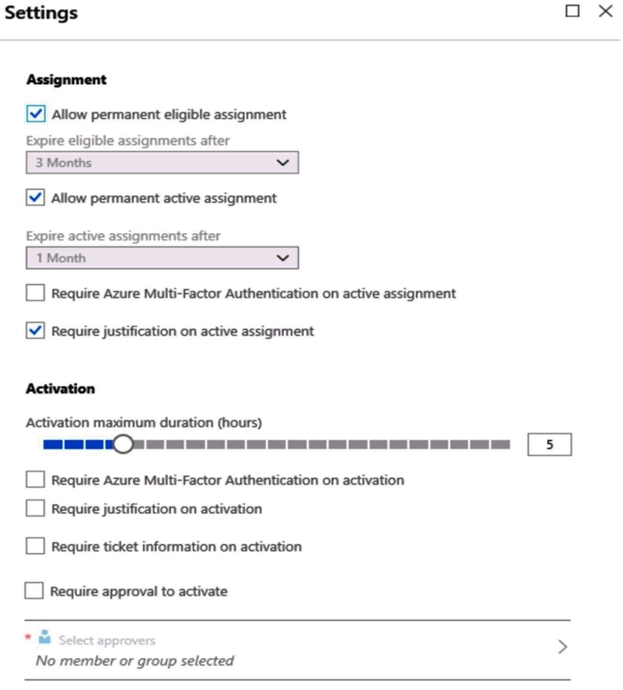
From PIM, you assign the Security Administrator role to the following groups:
Group1: Active assignment type, permanently assigned
Group2: Eligible assignment type, permanently eligible
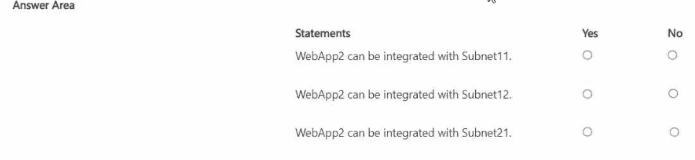
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

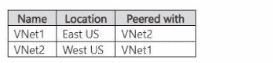
You have an Azure subscription that contains the virtual networks shown in the following table.
The subscription contains the subnets shown in the following table.
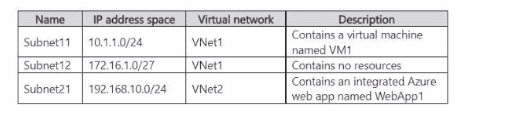
You plan to create an Azure web app named WebApp2 that will have the following configurations:
• Region: East US
• VNet integration: Enabled
• Scale out; Autoscale to up to 10 instances
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
You have an Azure subscription that contains the resources shown in the following table.
You need to configure AFW1 to only allow traffic from VM1 to storage accounts in the West US Azure region. The solution must minimize administrative effort.
What should you configure?
You are collecting events from Azure virtual machines to an Azure Log Analytics workspace.
You plan to create alerts based on the collected events
You need to identify which Azure services can be used to create the alerts.
Which two services should you identify? Each correct answer presents a complete solution
NOTE: Each correct selection is worth one point.
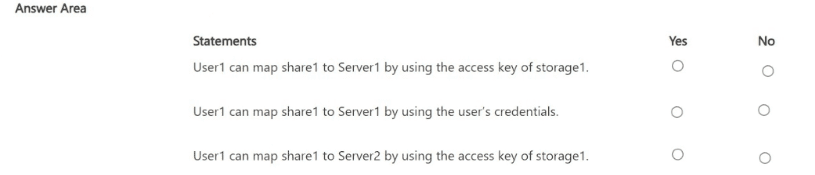
You have a hybrid Microsoft Entra tenant named contoso.com that contains a user named Uset1 and the servers shown in the following table.
The tenant is linked to an Azure subscription that contains a storage account named storage1. The storage1 account contains a file share named shares1.
User1 is assigned the Storage File Data SMB Share Contributor role for storages1.
The Security protocol settings for the file shares of storage1 are configured as shown in the following exhibit.
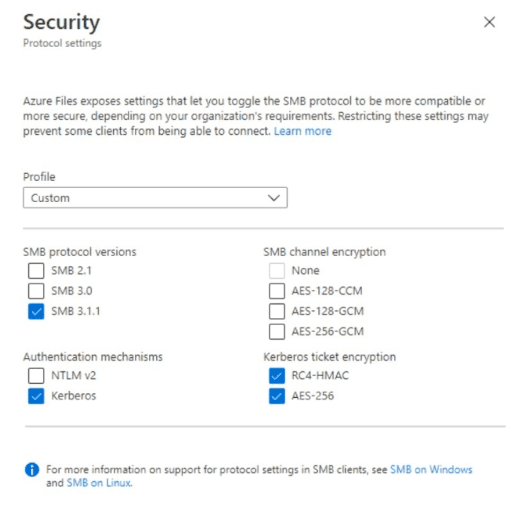
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE; Each correct selection is worth one point.
You have an Azure subscription that contains an Azure Data Lake Storage Gen2 account named storage1. You deploy an Azure Synapse Analytics workspace named synapsews1 to a managed virtual network. You need to enable access from synapsews1 to storage1. What should you configure?
You have an Azure Sentinel workspace that has an Azure Active Directory (Azure AD) data connector.
You are threat hunting suspicious traffic from a specific IP address.
You need to annotate an intermediate event stored in the workspace and be able to reference the IP address when navigating through the investigation graph.
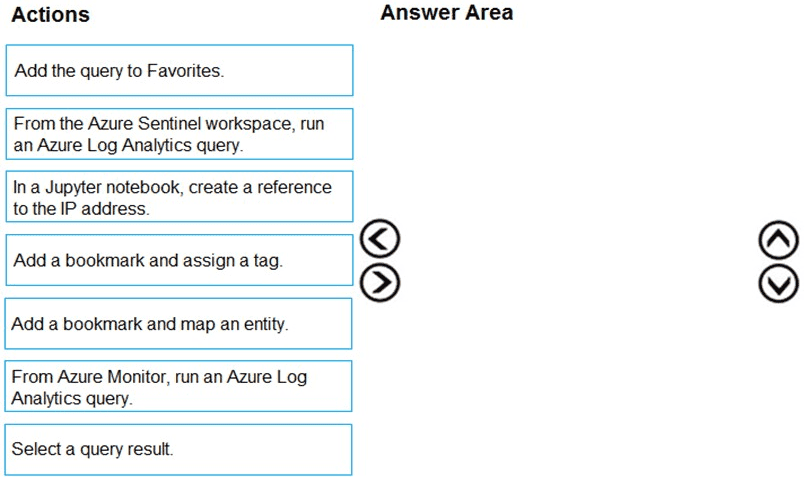
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
You have an Azure subscription named Sub1 that contains an Azure Log Analytics workspace named LAW1.
You have 100 on-premises servers that run Windows Server 2012 R2 and Windows Server 2016. The servers connect to LAW1. LAW1 is configured to collect security-related performance counters from the connected servers.
You need to configure alerts based on the data collected by LAW1. The solution must meet the following requirements:
Alert rules must support dimensions.
The time it takes to generate an alert must be minimized.
Alert notifications must be generated only once when the alert is generated and once when the alert is
resolved.
Which signal type should you use when you create the alert rules?
You have an Azure subscription named Sub1 that has Security defaults disabled. The subscription contains the following users:
• Five users that have owner permissions for Sub1.
• Ten users that have owner permissions for Azure resources.
None of the users have multi-factor authentication (MFA) enabled.
Sub1 has the secure score as shown in the Secure Score exhibit. (Click the Secure Score tab.)
You plan to enable MFA for the following users:
• Five users that have owner permissions for Sub1.
• Five users that have owner permissions for Azure resources.
By how many points will the secure score increase after you perform the planned changes?








