Microsoft AZ-500 - Microsoft Azure Security Technologies
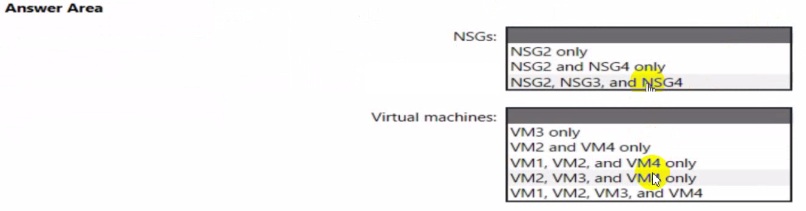
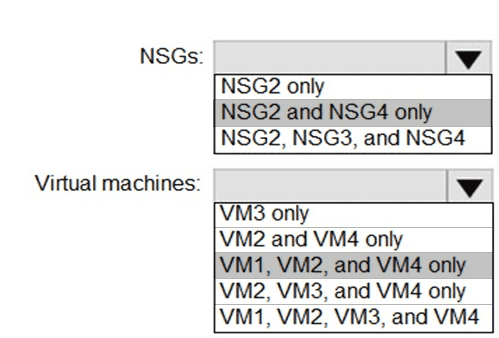
You implement the planned changes for ASG1 and ASG2.
In which NSGs can you use ASG1. and the network interfaces of which virtual machines can you assign to ASG2?
You need to meet the technical requirements for the finance department users.
Which CAPolicy1 settings should you modify?
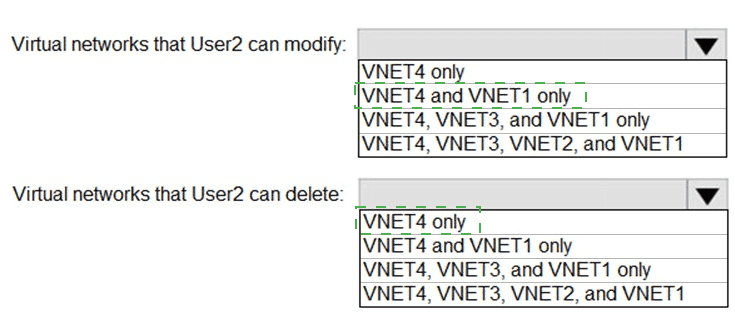
You need to encrypt storage1 to meet the technical requirements. Which key vaults can you use?
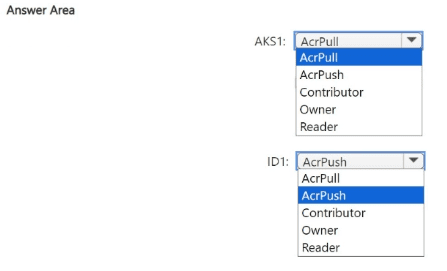
You need to configure the AKS1 and ID1 managed identities to meet the technical requirements. The solution must follow the principle of least privilege.
Which role should you assign to each identity? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
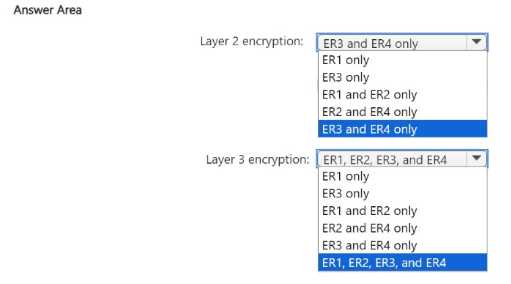
You need to recommend an encryption solution for the planned ExpressRoute implementation. The solution must meet the technical requirements.
Which ExpressRoute circuit should you recommend for each type of encryption? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to implement the planned change for SQLdb1.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
You need to implement the planned change for WAF1.
The solution must minimize administrative effort
What should you do?
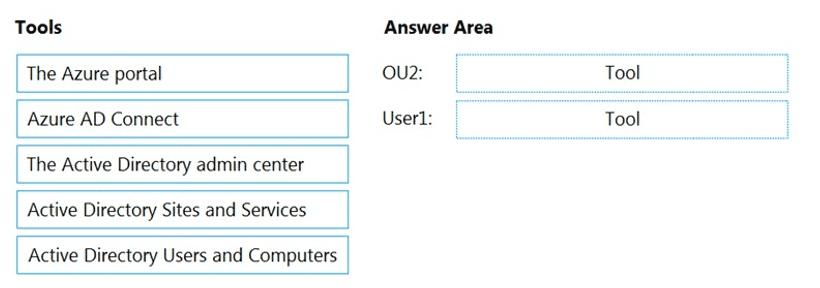
You need to perform the planned changes for OU2 and User1.
Which tools should you use? To answer, drag the appropriate tools to the correct resources. Each tool may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
You need to implement the planned change for VM1 to access storage1.
The solution must meet the technical requirements.
What should you do first?
You implement the planned changes for the key vaults.
To which key vaults can you restore AKV1 backups?



 Graphical user interface, text, application, chat or text message Description automatically generated
Graphical user interface, text, application, chat or text message Description automatically generated


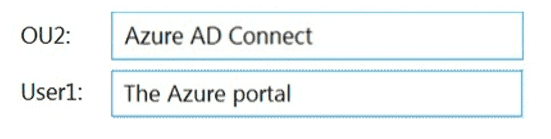 Table Description automatically generated
Table Description automatically generated