Microsoft AZ-801 - Configuring Windows Server Hybrid Advanced Services
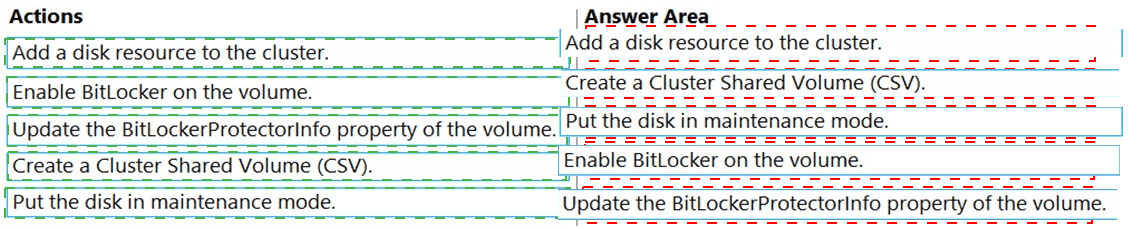
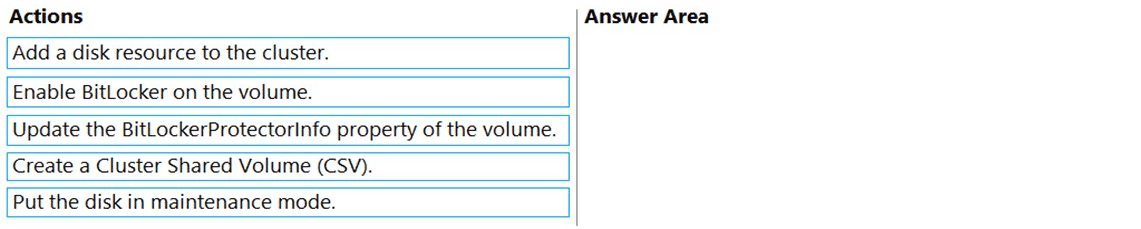
You are planning the implementation of Cluster2 to support the on-premises migration plan.
You need to ensure that the disks on Cluster2 meet the security requirements.
In which order should you perform the actions? To answer, move all actions from the list of actions to the answer area and arrange them in the correct order.
You are planning the deployment of Microsoft Sentinel.
Which type of Microsoft Sentinel data connector should you use to meet the security requirements?
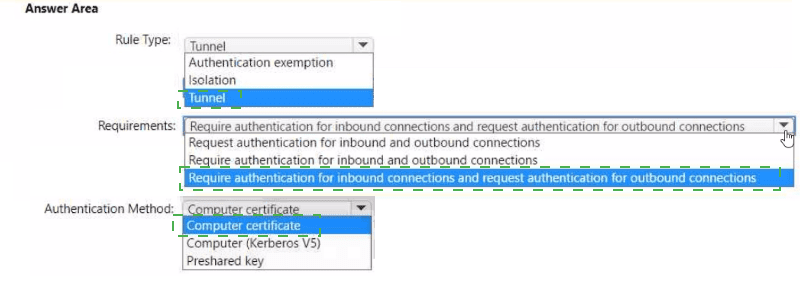
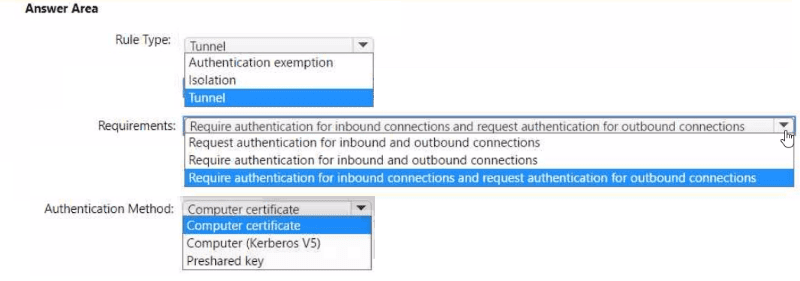
Your network contains an Active Directory Domain Services (AD DS) domain named contoso.com. The domain contains an organizational unit (OU) named 0U1.0U1 contains servers that run sensitive workloads.
You plan to add connection security rules that meet the following requirements:
• The servers in OU 1 must only accept connections from domain-joined
• The servers in OU 1 must only be able to communicate with domain-joined
You create a Group Policy Object (GPO) named GP01 and link GP01 to contoso.com.
You need to configure a connection security rule in GP01 by using Windows Defender Firewall with Advanced Security.
How should you configure the rule? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You deploy Azure Migrate to an on-premises network.
You have an on-premises physical server named Server1 that runs Windows Server and has the following configuration.
Operating system disk 600 GB
Data disic 3 TB
NIC Teaming: Enabled
Mobility service: installed
Windows Firewall: Enabled
Microsoft Defender Antivirus: Enabled
You need to ensure that you can use Azure Migrate to migrate Server1.
Solution: You disable Microsoft Defender Antivirus on Server1.
Does this meet the goal?
You deploy Azure Migrate to an on-premises network.
You have an on-premises physical server named Server1 that runs Windows Server and has the following configurations:
• Operating system disk; 600 GB
• Data disk: 3 TB
• NIC Teaming: Enabled
• Mobility service: Installed
• Windows Defender Firewall: Enabled
• Microsoft Defender Antivirus: Enabled
You need to ensure that you can use Azure Migrate to migrate Server1.
Solution: You disable Windows Defender Firewall on Server 1.
Does this meet the goal?
You have an Azure subscription. The subscription contains a virtual machine named Serve1 that run Windows Server.
You create a new Log Analytics workspace named Workspace1. You need to collect performance metrics for Server! by using Azure Monitor. What should you do next?
You have two servers named Server 1 and Server2 that run Windows Server. You perform the following actions:
• On Server1, you create an Application Control policy named Policy! that contains a rule to allow all the executables in a folder named D:\Folder1.
• You add a rule to Policy1 to trust a folder named \\Server2\FolderZ
• You deploy Policy1.
You need to verify that Policy1 is applied to Server1. Which Event Viewer log should you review?
You have a server named Served that runs Windows Server. You install a custom app named App1 that is accessed by using TCP port 52310. Users report that they cannot access App1. You confirm that App1 is running on Server1.
You need to ensure that the users can access App1. The solution must only provide access to App1 on Server1. What should you do in Windows Defender Firewall with Advanced Security?
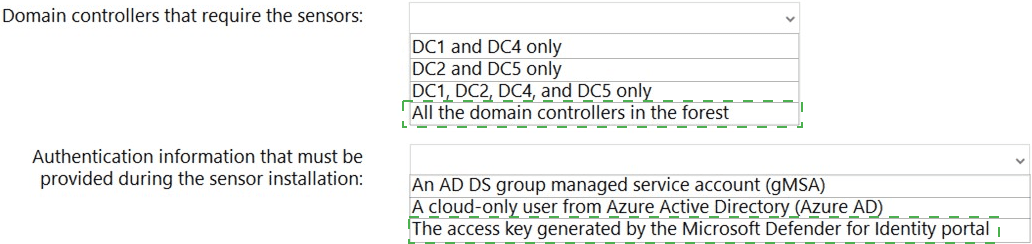
Your network contains an Active Directory Domain Services (AD DS) forest. The forest contains the domains shown in the following table.
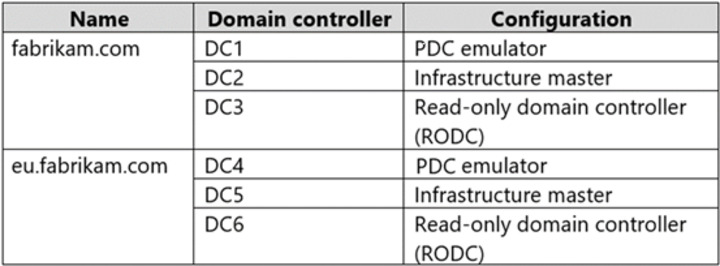
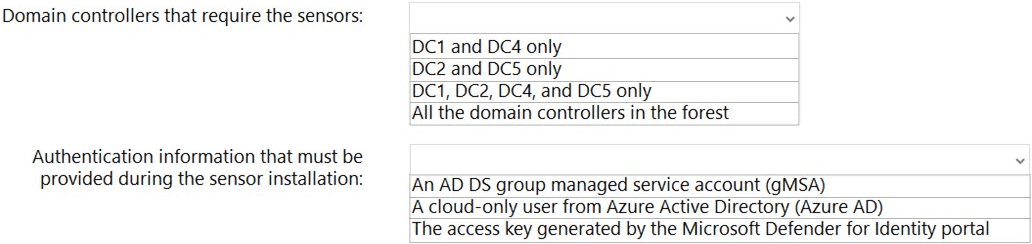
You are implementing Microsoft Defender for Identity sensors.
You need to install the sensors on the minimum number of domain controllers. The solution must ensure that Defender for Identity will detect all the security risks in both the domains.
What should you identify? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a failover cluster named Cluster1 that has the following configurations:
Number of nodes: 6
Quorum: Dynamic quorum
Witness: File share, Dynamic witness
What is the maximum number of nodes that can fail simultaneously while maintaining quorum?