Microsoft AZ-801 - Configuring Windows Server Hybrid Advanced Services
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a failover cluster named Cluster1 that hosts an application named App1.
The General tab in App1 Properties is shown in the General exhibit. (Click the General tab.)
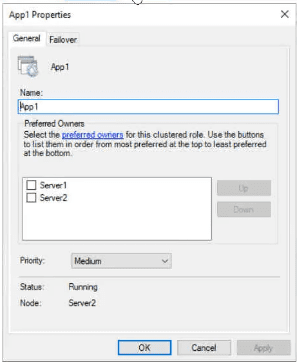
The Failover tab in App1 Properties is shown in the Failover exhibit. (Click the Failover tab.)
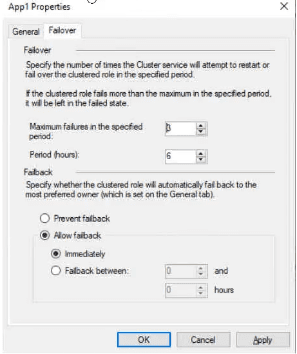
Server1 shuts down unexpectedly.
You need to ensure that when you start Server1, App1 continues to run on Server2.
Solution: From the Failover settings, you select Prevent failback.
Does this meet the goal?
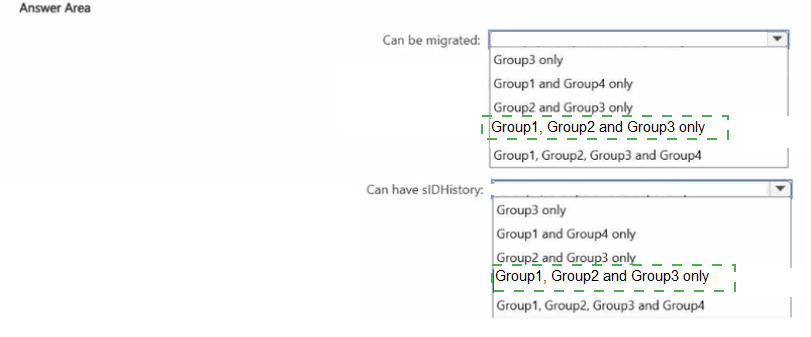
Your network contains two Active Directory Domain Services (AD DS) forests named contoso.com and fabtikam.com. Contoso.com includes the groups shown in the following table.
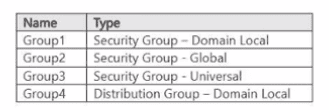
You need to migrate the groups to fabrikam.com by using ADMT.
Which groups can be migrated and which groups can have the sIDHistory attribute populated after the migration?
You have an Azure virtual machine named VM1 that runs Windows Server.
You need to encrypt the contents of the disks on VM1 by using Azure Disk Encryption.
What is a prerequisite for implementing Azure Disk Encryption?
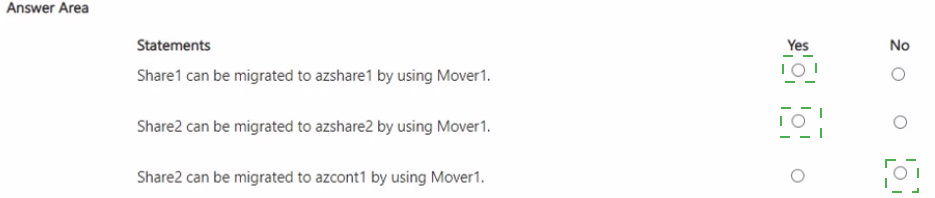
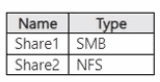
You have an on-premises server named Server1 that runs Windows Server and contains the shares shown in the following table.
You have an Azure subscription named Sub1 that contains an Azure Storage Mover resource named Mover1 and the storage accounts shown in the following table.

The storage accounts contain the resources shown in the following table.
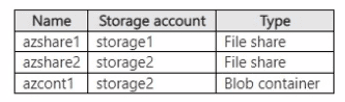
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
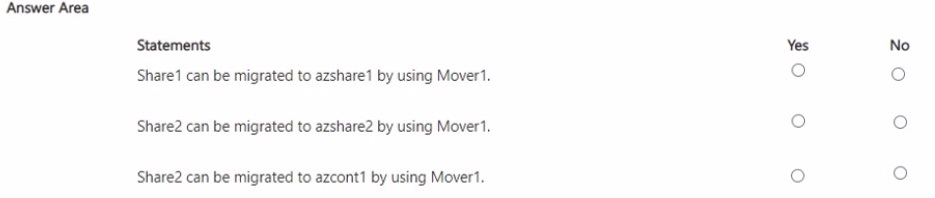
You have a failover cluster named Cluster1 that contains the nodes shown in the following table.
A File Server for general use cluster role named HAFS is configured as shown in the General exhibit (Click the General tab.)

Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a server named Server1 that runs Windows Server.
You need to ensure that only specific applications can modify the data in protected folders on Server1.
Solution: From App & browser control, you configure the Exploit protection settings.
Does this meet the goal?
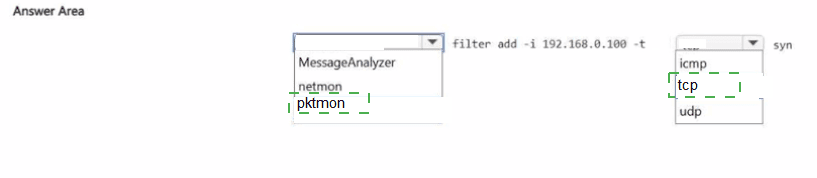
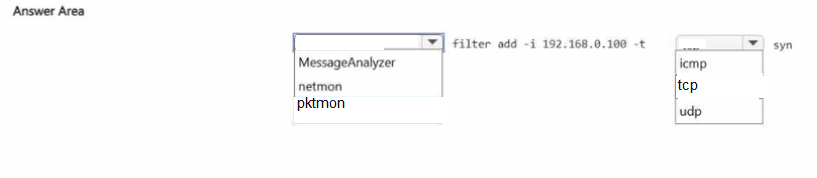
You have a server named Server1 that runs Windows Server.
You need to capture the SYN packets exchanged between Server1 and an IP address of 192.168.0.100. How should you complete the command? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Your network contains an Active Directory Domain Services (AD DS) domain All domain members have Microsoft Defender Credential Guard with UEFI tock configured in the domain you deploy a server named Server1 that runs Windows Server. You disable Credential Guard on Server1. You need to ensure that Server1 is MOST subject to Credential Guard restrictions. What should you do next?
Your on-premises network contains an Active Directory Domain Services (AD DS) domain. The domain contains five servers that run Windows Server. The network also contains two workgroup servers that run Windows Server.
You need to implement a connection security rule between the member servers and the workgroup servers.
Which authentication method should you use?
Your network contains an on-premises Active Directory Domain Services (AD DS) domain. The domain contains two virtual machines named VM1 and VM2 that run Windows Server.
You plan to implement a failover cluster named Cluster1 that will use VM1 and VM2 as nodes.
You need to ensure that Cluster1 can use floating IP addresses.
Which two components should you deploy? Each correct answer presents part-of the solution.
NOTE: Each correct selection is worth one point.