IBM C2090-623 - IBM Cognos Analytics Administrator V1
A report author gets the following error message:
“An error has occurred. Please contact your administrator. The complete error has been logged by CAF with SecureErrorID:2004-05-25-15:44:11.296-#9.â€
How can the administrator get the complete error message?
An administrator created a Content Store export and included the user account information.
How can a listing of the content be exported?
An administrator is reviewing the memory allocations listed below in the current environment.
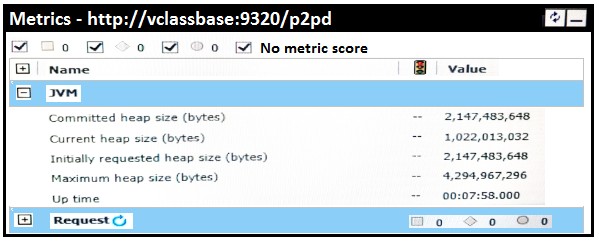
Which action should the administrator take?
An administrator is implementing security by managing and working with the Cognos namespace.
Which statement is true?
An administrator deleted a group inadvertently then recreated it, but now the access permissions based on that group no longer work.
What must be done?
An administrator is configuring settings for the Cognos Analytics Mobile app.
Which settings can be managed?
An administrator wants to exclude Request level logging details from being captured.
Which logging level must be set?
An administrator wants to control server workload by putting routing rules in place.
Which components can be used?
An administrator wants to start the LifeCycle Manager service.
How can this be done?
An administrator is performing tasks in the IBM Cognos Administration console.
Which task can be performed on the Status > System page?



