CompTIA CAS-004 - CompTIA SecurityX Certification Exam
A significant weather event caused all systems to fail over to the disaster recovery site successfully. However, successful data replication has not occurred in the last six months, which has resulted in
the service being unavailable. V•Vh1ch of the following would BEST prevent this scenario from happening again?
A cloud security architect has been tasked with finding a solution for hardening VMS. The solution must meet the following requirements:
• Data needs to be stored outside of the VMS.
• No unauthorized modifications to the VMS are allowed
• If a change needs to be done, a new VM needs to be deployed.
Which of the following is the BEST solution?
Which of the following testing plans is used to discuss disaster recovery scenarios with representatives from multiple departments within an incident response team but without taking any invasive actions?
A security consultant has been asked to recommend a secure network design that would:
• Permit an existing OPC server to communicate with a new Modbus server that is controlling electrical relays.
• Limit operational disruptions.
Due to the limitations within the Modbus protocol, which of the following configurations should the security engineer recommend as part of the solution?
A pharmaceutical company was recently compromised by ransomware. Given the following EDR output from the process investigation:
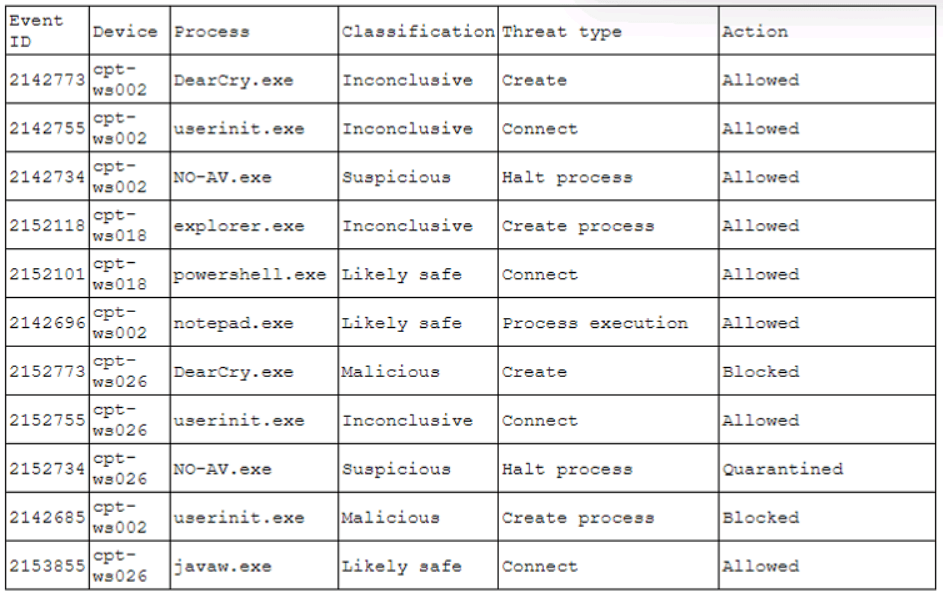
On which of the following devices and processes did the ransomware originate?
A company wants to implement a new website that will be accessible via browsers with no mobile applications available. The new website will allow customers to submit sensitive medical information securely and receive online medical advice. The company already has multiple other websites where it provides various public health data and information. The new website must implement the following:
• The highest form Of web identity validation
• Encryption of all web transactions
• The strongest encryption in-transit
• Logical separation based on data sensitivity
Other things that should be considered include:
• The company operates multiple other websites that use encryption.
• The company wants to minimize total expenditure.
• The company wants to minimize complexity
Which of the following should the company implement on its new website? (Select TWO).
Due to internal resource constraints, the management team has asked the principal security architect to recommend a solution that shifts most of the responsibility for application-level controls to the cloud provider. In the shared responsibility model, which of the following levels of service meets this requirement?
A security analyst runs a vulnerability scan on a network administrator's workstation The network administrator has direct administrative access to the company's SSO web portal The vulnerability scan uncovers cntical vulnerabilities with equally high CVSS scores for the user's browser, OS, email client and an offline password manager Which of the following should the security analyst patch FIRST?
An organization is running its e-commerce site in the cloud. The capacity is sufficient to meet the organization's needs throughout most of the year, except during the holidays when the organization plans to introduce a new line of products and expects an increase in traffic. The organization is not sure how well its products will be received. To address this issue, the organization needs to ensure that:
* System capacity is optimized.
* Cost is reduced.
Which of the following should be implemented to address these requirements? (Select TWO).
Which of the following is a risk associated with SDN?
A company wants to refactor a monolithic application to take advantage of cloud native services and service microsegmentation to secure sensitive application components. Which of the following should the company implement to ensure the architecture is portable?
A network administrator for a completely air-gapped and closed system has noticed that anomalous external files have been uploaded to one of the critical servers. The administrator has reviewed logs
in the SIEM that were collected from security appliances, network infrastructure devices, and endpoints. Which of the following processes, if executed, would be MOST likely to expose an attacker?
A security analyst for a managed service provider wants to implement the most up-to-date and effective security methodologies to provide clients with the best offerings. Which of the following resources
would the analyst MOST likely adopt?
A security solution uses a sandbox environment to execute zero-day software and collect indicators of compromise. Which of the following should the organization do to BEST take advantage of this solution?
Which of the following objectives BEST supports leveraging tabletop exercises in business continuity planning?



