CompTIA CAS-004 - CompTIA SecurityX Certification Exam
An analyst needs to evaluate all images and documents that are publicly shared on a website. Which of the following would be the best tool to evaluate the metadata of these files?
A security team is creating tickets to track the progress of remediation. Which of the following is used to specify the due dates for high- and critical-priority findings?
During a software assurance assessment, an engineer notices the source code contains multiple instances of strcpy. which does not verify the buffer length. Which of the following solutions should be integrated into the SDLC process to reduce future risks?
After establishing coding standards and integrating software assurance tools into CI/CD pipelines, an architect continues to find too many different coding styles throughout the team. Which of the following additional measures can the architect take to help improve consistency?
The security team is looking into aggressive bot behavior that is resulting in performance issues on the web server After further investigation, the security engineer determines that the bot traffic is legitimate. Which of the following is the best course of action to reduce performance issues without allocating additional resources to the server?
A security engineer is reviewing metrics for a series of bug bounty reports. The engineer finds systematic cross-site scripting issues and unresolved previous findings. Which of the following is the best solution to address the issue?
A security analyst received the following finding from a cloud security assessment tool:
Virtual Machine Data Disk is encrypted with the default encryption key.
Because the organization hosts highly sensitive data files, regulations dictate it must be encrypted so it is unreadable to the CSP. Which of the following should be implemented to remediate the finding and meet the regulatory requirement? (Select two).
The findings from a recent penetration test report indicate a systematic issue related to cross-site scripting (XSS). A security engineer would like to prevent this type of issue for future reports. Which of the following mitigation strategies should the engineer use to best resolve the issue?
A security engineer is re-architecting a network environment that provides regional electric distribution services. During a pretransition baseline assessment, the engineer identified the following security-relevant characteristics of the environment:
• Enterprise IT servers and supervisory industrial systems share the same subnet.
• Supervisory controllers use the 750MHz band to direct a portion of fielded PLCs.
• Command and telemetry messages from industrial control systems are unencrypted and unauthenticated.
Which of the following re-architecture approaches would be best to reduce the company's risk?
A security engineer needs to select the architecture for a cloud database that will protect an organization's sensitive data. The engineer has a choice between a single-tenant or a multitenant database architecture offered by a cloud vendor. Which of the following best describes the security benefits of the single-tenant option? (Select two).
A help desk technician is troubleshooting an issue with an employee's laptop that will not boot into its operating system. The employee reported the laptop had been stolen but then found it one day later. The employee has asked the technician for help recovering important data. The technician has identified the following:
• The laptop operating system was not configured with BitLocker.
• The hard drive has no hardware failures.
• Data is present and readable on the hard drive, although it appears to be illegible.
Which of the following is the most likely reason the technician is unable to retrieve legible data from the hard drive?
A cyberanalyst has been tasked with recovering PDF files from a provided image file. Which of the following is the best file-carving tool for PDF recovery?
After a server was compromised an incident responder looks at log files to determine the attack vector that was used The incident responder reviews the web server log files from the time before an unexpected SSH session began:
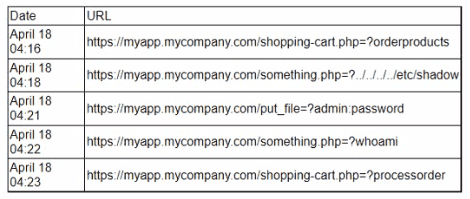
Which of the following is the most likely vulnerability that was exploited based on the log files?
A security engineer is working for a service provider and analyzing logs and reports from a new EDR solution, which is installed on a small group of workstations. Later that day, another security engineer receives an email from two developers reporting the software being used for development activities is now blocked. The developers have not made any changes to the software being used. Which of the following is the EDR reporting?
A new VM server (Web Server C) was spun up in the cloud and added to the load balancer to an existing web application (Application A) that does not require internet access. Sales users arereporting intermittent issues with this application when processing orders that require access to the warehouse department.
Given the following information:
Firewall rules: Existing rules do not account for Web Server C’s IP address (10.2.0.92).
Application A Security Group: Inbound rules and outbound rules are insufficient for the new server.
The security team wants to minimize the firewall rule set by avoiding specific host rules whenever possible. Which of the following actions must be taken to resolve the issue and meet the security team's requirements?



