CompTIA CAS-004 - CompTIA SecurityX Certification Exam
A mobile application developer is creating a global, highly scalable, secure chat application. The developer would like to ensure the application is not susceptible to on-path attacks while the user is traveling in potentially hostile regions. Which of the following would BEST achieve that goal?
A DNS forward lookup zone named complia.org must:
• Ensure the DNS is protected from on-path attacks.
• Ensure zone transfers use mutual authentication and are authenticated and negotiated.
Which of the following should the security architect configure to meet these requirements? (Select two).
A company recently deployed a SIEM and began importing logs from a firewall, a file server, a domain controller a web server, and a laptop. A security analyst receives a series of SIEM alerts and prepares to respond. The following is the alert information:
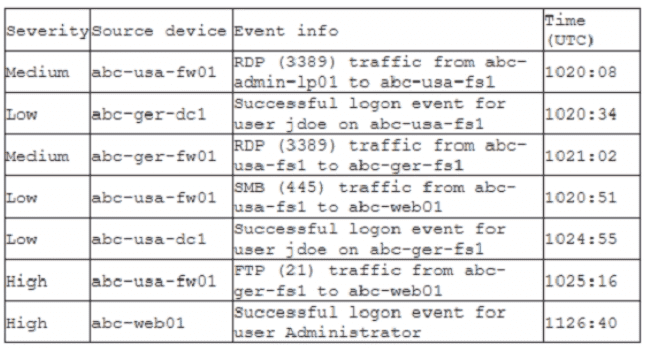
Which of the following should the security analyst do FIRST?
The primary advantage of an organization creating and maintaining a vendor risk registry is to:
A technology company developed an in-house chat application that is used only by developers. An open-source library within the application has been deprecated. The facts below are provided:
The cost of replacing this system is nominal.
The system provides no revenue to the business.
The system is not a critical part of the business.
Which of the following is the best risk mitigation strategy?
A customer requires secure communication of subscribed web services at all times, but the company currently signs its own certificate requests to an internal CA. Which of the following approaches will best meet the customer's requirements?
A security administrator is setting up a virtualization solution that needs to run services from a single host. Each service should be the only one running in its environment. Each environment needs to have its own operating system as a base but share the kernel version and properties of the running host. Which of the following technologies would best meet these requirements?
A new requirement for legislators has forced a government security team to develop a validation process to verify the integrity of a downloaded file and the sender of the file Which of the following is the BEST way for the security team to comply with this requirement?
When managing and mitigating SaaS cloud vendor risk, which of the following responsibilities belongs to the client?
A regulated company is in the process of refreshing its entire infrastructure. The company has a business-critical process running on an old 2008 Windows server. If this server fails, the company would lose millions of dollars in revenue. Which of the following actions should the company take?
A PKI engineer is defining certificate templates for an organization's CA and would like to ensure at least two of the possible SAN certificate extension fields populate for documentation purposes. Which of the following are explicit options within this extension? (Select two).
Based on a recent security audit, a company discovered the perimeter strategy is inadequate for its recent growth. To address this issue, the company is looking for a solution that
includes the following requirements:
• Collapse of multiple network security technologies into a single footprint
• Support for multiple VPNs with different security contexts
• Support for application layer security (Layer 7 of the OSI Model)
Which of the following technologies would be the most appropriate solution given these requirements?
A security engineer is concerned about the threat of side-channel attacks The company experienced a past attack that degraded parts of a SCADA system, causing a fluctuation to 20,000rpm from its normal operating range As a result, the part deteriorated more quickly than the mean time to failure A further investigation revealed the attacker was able to determine the acceptable rpm range, and the malware would then fluctuate the rpm until the pan failed Which of the following solutions would be best to prevent a side-channel attack in the future?
In support of disaster recovery objectives, a third party agreed to provide 99.999% uptime. Recently, a hardware failure impacted a firewall without service degradation. Which of the following resiliency concepts was most likely in place?
To save on device life-cycle costs, a company is transitioning to a BYOD deployment scheme for enterprise mobility. Local laws protect users from corporate-initiated wiping or manipulation of data not owned by the company. Which of the following techniques would best protect corporate data while ensuring the integrity of private data?



