CompTIA CAS-005 - CompTIA SecurityX Certification Exam
Which of the following is the main reason quantum computing advancements are leading companies and countries to deploy new encryption algorithms?
The ISAC for the retail industry recently released a report regarding social engineering tactics in which small groups create distractions for employees while other malicious individuals install advanced card skimmers on the payment systems. The Chief Information Security Officer (CISO) thinks that security awareness training, technical control implementations, and governance already in place is adequate to protect from this threat. The board would like to test these controls. Which of the following should the CISO recommend?
A company's security policy states that any publicly available server must be patched within 12 hours after a patch is released A recent llS zero-day vulnerability was discovered that affects all versions of the Windows Server OS:
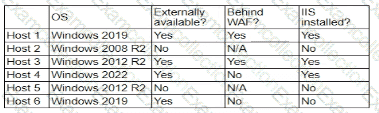
Which of the following hosts should a security analyst patch first once a patch is available?
After a vendor identified a recent vulnerability, a severity score was assigned to the vulnerability. A notification was also publicly distributed. Which of the following would most likely include information regarding the vulnerability and the recommended remediation steps?
An organization currently has IDS, firewall, and DLP systems in place. The systems administrator needs to integrate the tools in the environment to reduce response time. Which of the following should the administrator use?
A company migrated a critical workload from its data center to the cloud. The workload uses a very large data set that requires computational-intensive data processing. The business unit that uses the workload is projecting the following growth pattern:
• Storage requirements will double every six months.
• Computational requirements will fluctuate throughout the year.
• Average computational requirements will double every year.
Which of the following should the company do to address the business unit's requirements?
While reviewing recent modem reports, a security officer discovers that several employees were contacted by the same individual who impersonated a recruiter. Which of the following best describes this type of correlation?



