CompTIA CAS-005 - CompTIA SecurityX Certification Exam
An organization wants to manage specialized endpoints and needs a solution that provides the ability to
* Centrally manage configurations
* Push policies.
• Remotely wipe devices
• Maintain asset inventory
Which of the following should the organization do to best meet these requirements?
During a recentsecurity event, access from thenon-production environment to the production environmentenabledunauthorized usersto:
Installunapproved software
Makeunplanned configuration changes
During theinvestigation, the following findings were identified:
Several new users were added in bulkby theIAM team
Additionalfirewalls and routerswere recently added
Vulnerability assessmentshave been disabled formore than 30 days
Theapplication allow listhas not been modified intwo weeks
Logs were unavailablefor various types of traffic
Endpoints have not been patchedinover ten days
Which of the following actions would most likely need to be taken toensure proper monitoring?(Select two)
A user tried to access a web page at http://10.1.1.1 . Previously the web page did not require authentication, and now the browser is prompting for credentials. Which of the following actions would best prevent the issue from reoccurring and reduce the likelihood of credential exposure?
A software development team requires valid data for internal tests. Company regulations, however do not allow the use of this data in cleartext. Which of the following solutions best meet these requirements?
A web application server that provides services to hybrid modern and legacy financial applications recently underwent a scheduled upgrade to update common libraries, including OpenSSL. Multiple users are now reporting failed connection attempts to the server. The technician performing initial triage identified the following:
• Client applications more than five years old appear to be the most affected.
• Web server logs show initial connection attempts by affected hosts.
• For the failed connections, logs indicate "cipher unavailable."
Which of the following is most likely to safely remediate this situation?
A technician is reviewing the logs and notices a large number of files were transferred to remote sites over the course of three months. This activity then stopped. The files were transferred via TLS-protected HTTP sessions from systems that do not normally send traffic to those sites. The technician will define this threat as:
A security analyst isreviewing the following event timeline from an COR solution:
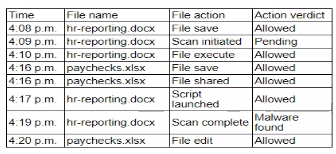
Which of the following most likely has occurred and needs to be fixed?
Which of the following is the main reason quantum computing advancements are leading companies and countries to deploy new encryption algorithms?
A company detects suspicious activity associated with external connections Security detection tools are unable tocategorize this activity. Which of the following is the best solution to help the company overcome this challenge?
Asoftware company deployed a new application based on its internal code repository Several customers are reporting anti-malware alerts on workstations used to test the application Which of the following is the most likely cause of the alerts?



