CompTIA CAS-005 - CompTIA SecurityX Certification Exam
A security analyst is reviewing the following authentication logs:
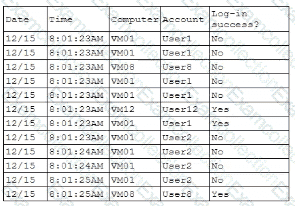
Which of the following should the analyst do first?
During a gap assessment, an organization notes that OYOD usage is asignificant risk. The organization implemented administrative policies prohibiting BYOD usage However, the organization has not implemented technical controls to prevent the unauthorized use of BYOD assets when accessing the organization's resources. Which of the following solutions should the organization implement to b»« reduce the risk of OYOD devices? (Select two).
A news organization wants to implement workflows that allow users to request that untruthful data be retraced and scrubbed from online publications to comply with the right to be forgotten Which of the following regulations is the organization most likely trying to address'
A company implemented a NIDS and a NIPS on the most critical environments. Since this implementation, the company has been experiencing network connectivity issues. Which of the following should the security architect recommend for a new NIDS/NIPS implementation?
An organization found a significant vulnerability associated with a commonly used package in a variety of operating systems. The organization develops a registry of software dependencies to facilitate incident response activities. As part of the registry, the organization creates hashes of packages that have been formally vetted. Which of the following attack vectors does this registry address?
A threat hunter is identifying potentially malicious activity associated with an APT. When the threat hunter runs queries against the SIEM platform with a date range of 60 to 90 days ago, the involved account seems to be typically most active in the evenings. When the threat hunter reruns the same query with a date range of 5 to 30 days ago, the account appears to be most active in the early morning. Which of the following techniques is the threat hunter using to better understand the data?
Which of the following best describes a common use case for homomorphic encryption?
A developer makes a small change to a resource allocation module on a popular social media website and causes a memory leak. During a peak utilization period, several web servers crash, causing the website to go offline. Which of the following testing techniques is the most efficient way to prevent this from reoccurring?
Protected company data was recently exfiltrated. The SOC did not find any indication of a network or outside physical intrusion, and the DLP systems reported no unusual activity. The incident response team determined a text file was encrypted and reviews the following log excerpt:
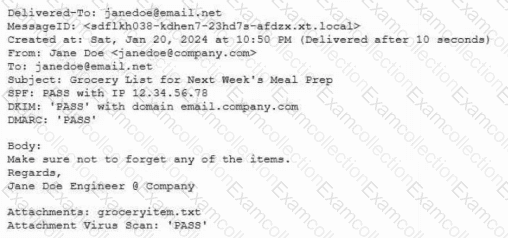
Which of the following is the most appropriate action for the team to take?
A security engineer is implementing a code signing requirement for all code developed by the organization. Currently, the PKI only generates website certificates. Which of the following steps should the engineer perform first?



