CompTIA CAS-005 - CompTIA SecurityX Certification Exam
Previously intercepted communications must remain secure even if a current encryption key is compromised in the future. Which of the following best supports this requirement?
An organization would like to increase the effectiveness of its incident response process across its multiplatform environment. A security engineer needs to implement the improvements using the organization's existing incident response tools. Which of the following should the security engineer use?
While performing threat-hunting functions, an analyst is using the Diamond Model of Intrusion Analysis. The analyst identifies the likely adversary, the infrastructure involved, and the target. Which of the following must the threat hunter document to use the model effectively?
A product development team has submitted code snippets for review prior to release.
INSTRUCTIONS
Analyze the code snippets, and then select one vulnerability, and one fix for each code snippet.
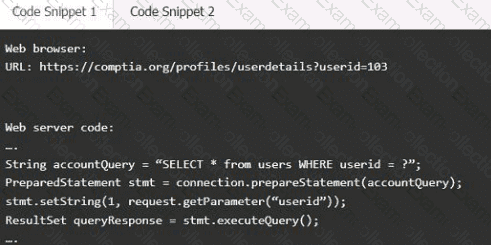
Code Snippet 1
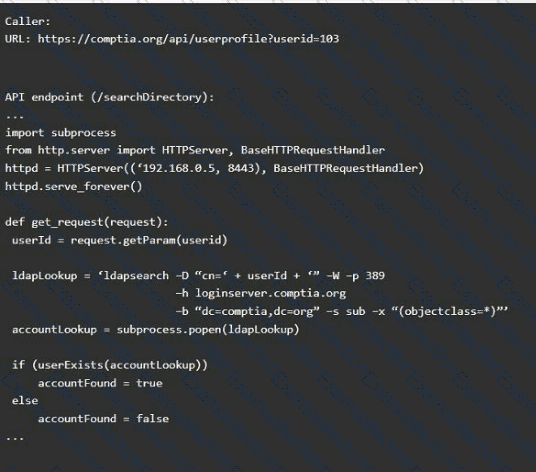
Code Snippet 2
Vulnerability 1:
SQL injection
Cross-site request forgery
Server-side request forgery
Indirect object reference
Cross-site scripting
Fix 1:
Perform input sanitization of the userid field.
Perform output encoding of queryResponse,
Ensure usex:ia belongs to logged-in user.
Inspect URLS and disallow arbitrary requests.
Implementanti-forgery tokens.
Vulnerability 2
1) Denial of service
2) Command injection
3) SQL injection
4) Authorization bypass
5) Credentials passed via GET
Fix 2
A) Implement prepared statements and bind
variables.
B) Remove the serve_forever instruction.
C) Prevent the "authenticated" value from being overridden by a GET parameter.
D) HTTP POST should be used for sensitive parameters.
E) Perform input sanitization of the userid field.
A company wants to install a three-tier approach to separate the web. database, and application servers A security administrator must harden the environment which of the following is the best solution?
A company wants to modify its process to comply with privacy requirements after an incident involving PII data in a development environment. In order to perform functionality tests, the QA team still needs to use valid data in the specified format. Which of the following best addresses the risk without impacting the development life cycle?
A company lined an email service provider called my-email.com to deliver company emails. The company stalled having several issues during the migration. A security engineer is troubleshooting and observes the following configuration snippet:
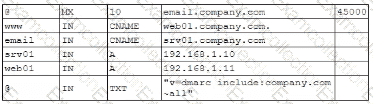
Which of the following should the security engineer modify to fix the issue? (Select two).
An organization determines existing business continuity practices are inadequate to support critical internal process dependencies during a contingency event. A compliance analyst wants the Chief Information Officer (CIO) to identify the level of residual risk that is acceptable to guide remediation activities. Which of the following does the CIO need to clarify?
An organization recently migrated data to a new file management system. The architect decides to use a discretionary authorization model on the new system. Which of the following best explains the architect's choice?
An organization is increasing its focus on training that addresses new social engineering and phishing attacks. Which of the following is the organization most concerned about?



