Blockchain CBSP - BTA Certified Blockchain Security Professional
Which of the following are shared benefits of private and permissioned blockchain architectures? Select all that apply.
Which of the following attacks were enabled by design decisions made by the blockchain's developers? Select all that apply
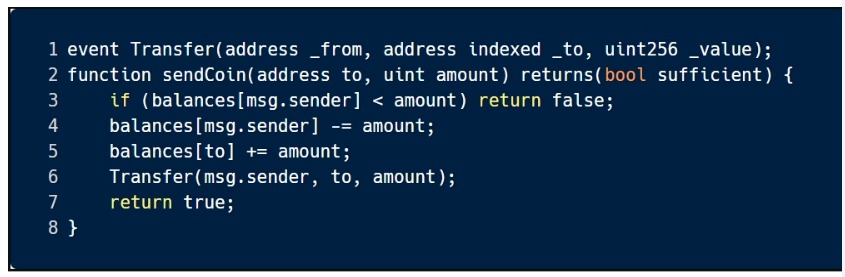
This sample code is vulnerable to which of the following attacks? Select all that apply.
Transaction validation on DAG-based DLTs is designed in a way that allows legitimate transactions to be considered untrusted due to random chance.
Determining if a transaction is part of the distributed ledger is less computationally intensive in DAG-based solutions than in blockchain
Which smart contract auditing strategy determines the inputs that will cause different parts of the code to run?
This sample code is vulnerable to which of the following attacks? Select all that apply.



