GAQM CEH-001 - Certified Ethical Hacker (CEH)
You are trying to package a RAT Trojan so that Anti-Virus software will not detect it. Which of the listed technique will NOT be effective in evading Anti-Virus scanner?
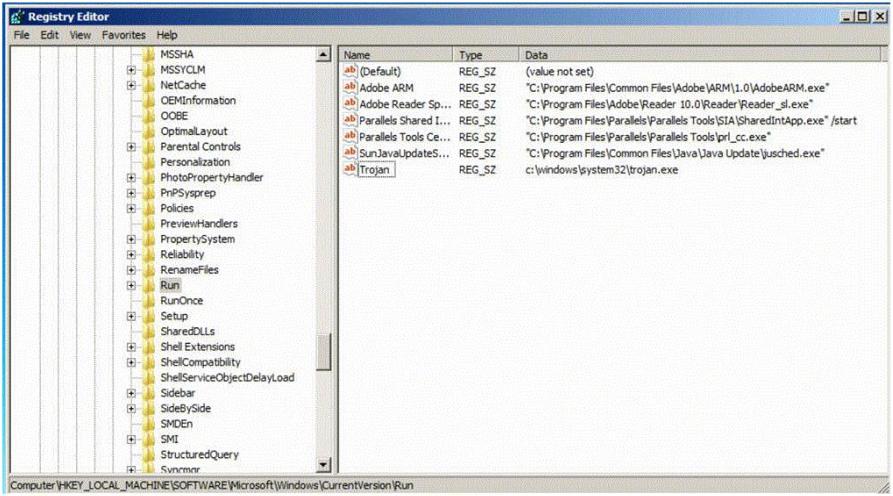
Which of the following Registry location does a Trojan add entries to make it persistent on Windows 7? (Select 2 answers)
Jake is a network administrator who needs to get reports from all the computer and network devices on his network. Jake wants to use SNMP but is afraid that won't be secure since passwords and messages are in clear text. How can Jake gather network information in a secure manner?



