GAQM CEH-001 - Certified Ethical Hacker (CEH)
Which of the following LM hashes represents a password of less than 8 characters?
Which of the following command line switch would you use for OS detection in Nmap?
An Nmap scan shows the following open ports, and nmap also reports that the OS guessing results to match too many signatures hence it cannot reliably be identified:
21 ftp
23 telnet
80 http
443 https
What does this suggest?
Exhibit
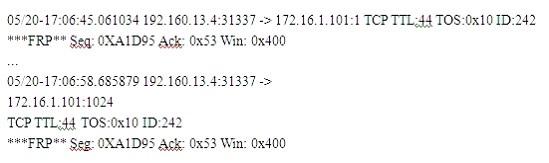
(Note: the student is being tested on concepts learnt during passive OS fingerprinting, basic TCP/IP connection concepts and the ability to read packet signatures from a sniff dump.)
Snort has been used to capture packets on the network. On studying the packets, the penetration tester finds it to be abnormal. If you were the penetration tester, why would you find this abnormal?
What is odd about this attack? Choose the best answer.
John has scanned the web server with NMAP. However, he could not gather enough information to help him identify the operating system running on the remote host accurately.
What would you suggest to John to help identify the OS that is being used on the remote web server?
What port scanning method involves sending spoofed packets to a target system and then looking for adjustments to the IPID on a zombie system?
At a Windows Server command prompt, which command could be used to list the running services?
Which of the following ICMP message types are used for destinations unreachables?
_________ is one of the programs used to wardial.
Sandra has been actively scanning the client network on which she is doing a vulnerability assessment test. While conducting a port scan she notices open ports in the range of 135 to 139. What protocol is most likely to be listening on those ports?
What is the proper response for a NULL scan if the port is closed?
While investigating a claim of a user downloading illegal material, the investigator goes through the files on the suspect's workstation. He comes across a file that is just called "file.txt" but when he opens it, he finds the following:
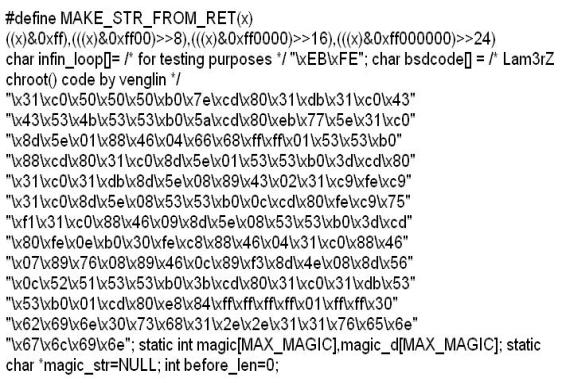
What can he infer from this file?
Exhibit
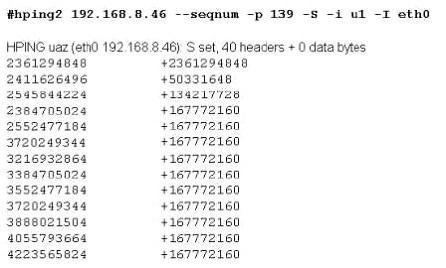
Joe Hacker runs the hping2 hacking tool to predict the target host’s sequence numbers in one of the hacking session.
What does the first and second column mean? Select two.
Bob has been hired to perform a penetration test on XYZ.com. He begins by looking at IP address ranges owned by the company and details of domain name registration. He then goes to News Groups and financial web sites to see if they are leaking any sensitive information of have any technical details online.
Within the context of penetration testing methodology, what phase is Bob involved with?
What is "Hacktivism"?
A company is legally liable for the content of email that is sent from its systems, regardless of whether the message was sent for private or business-related purposes. This could lead to prosecution for the sender and for the company's directors if, for example, outgoing email was found to contain material that was pornographic, racist, or likely to incite someone to commit an act of terrorism. You can always defend yourself by "ignorance of the law" clause.
Ann would like to perform a reliable scan against a remote target. She is not concerned about being stealth at this point.
Which of the following type of scans would be the most accurate and reliable option?
While performing ping scans into a target network you get a frantic call from the organization’s security team. They report that they are under a denial of service attack. When you stop your scan, the smurf attack event stops showing up on the organization’s IDS monitor. How can you modify your scan to prevent triggering this event in the IDS?
While attempting to discover the remote operating system on the target computer, you receive the following results from an nmap scan:

Remote operating system guess: Too many signatures match to reliably guess the OS.
Nmap run completed -- 1 IP address (1 host up) scanned in 277.483 seconds
What should be your next step to identify the OS?
While performing a ping sweep of a subnet you receive an ICMP reply of Code 3/Type 13 for all the pings sent out.
What is the most likely cause behind this response?



