GAQM CEH-001 - Certified Ethical Hacker (CEH)
What port scanning method is the most reliable but also the most detectable?
Which type of Nmap scan is the most reliable, but also the most visible, and likely to be picked up by and IDS?
What does the term “Ethical Hacking†mean?
What are the default passwords used by SNMP? (Choose two.)
Which of the following would be the best reason for sending a single SMTP message to an address that does not exist within the target company?
You have initiated an active operating system fingerprinting attempt with nmap against a target system:
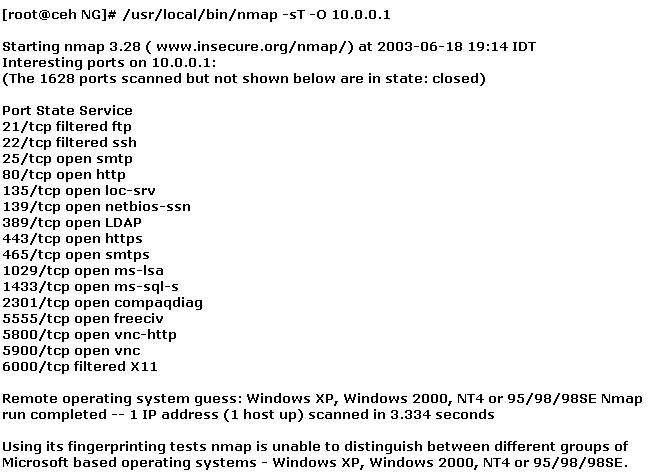
What operating system is the target host running based on the open ports shown above?
Name two software tools used for OS guessing? (Choose two.
__________ is found in all versions of NTFS and is described as the ability to fork file data into existing files without affecting their functionality, size, or display to traditional file browsing utilities like dir or Windows Explorer
Your lab partner is trying to find out more information about a competitors web site. The site has a .com extension. She has decided to use some online whois tools and look in one of the regional Internet registrys. Which one would you suggest she looks in first?
Network Administrator Patricia is doing an audit of the network. Below are some of her findings concerning DNS. Which of these would be a cause for alarm?
Select the best answer.
A very useful resource for passively gathering information about a target company is:
Your XYZ trainee Sandra asks you which are the four existing Regional Internet Registry (RIR's)?
When Jason moves a file via NFS over the company's network, you want to grab a copy of it by sniffing. Which of the following tool accomplishes this?
Fingerprinting an Operating System helps a cracker because:
John wishes to install a new application onto his Windows 2000 server.
He wants to ensure that any application he uses has not been Trojaned.
What can he do to help ensure this?
Bob wants to prevent attackers from sniffing his passwords on the wired network. Which of the following lists the best options?
Which definition among those given below best describes a covert channel?
What is the proper response for a NULL scan if the port is open?
Ethereal works best on ____________.
You have hidden a Trojan file virus.exe inside another file readme.txt using NTFS streaming.
Which command would you execute to extract the Trojan to a standalone file?



