ServiceNow CIS-SIR - Certified Implementation Specialist - Security Incident Response Exam
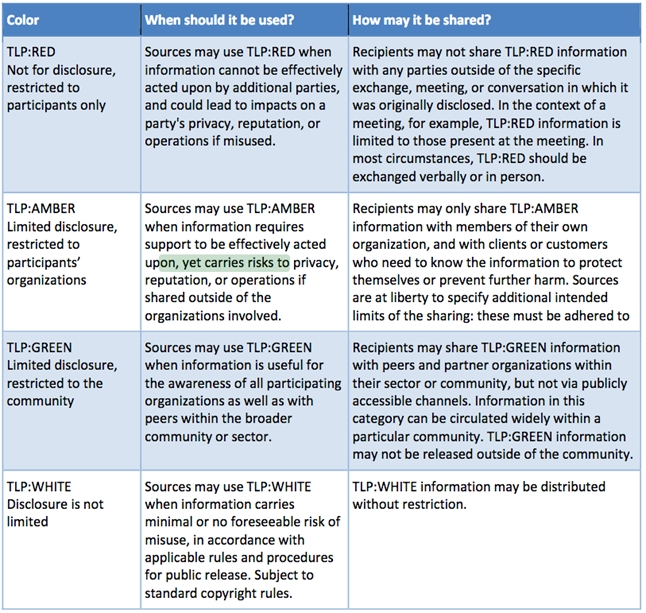
Security tag used when a piece of information requires support to be effectively acted upon, yet carries risks to privacy, reputation, or operations if shared outside of the organizations involved.
Using the KB articles for Playbooks tasks also gives you which of these advantages?
What is calculated as an arithmetic mean taking into consideration different values in the CI, Security Incident, and User records?
Which of the following State Flows are provided for Security Incidents? (Choose three.)
Which of the following are potential benefits for utilizing Security Incident assignment automation? (Choose two.)
What is the fastest way for security incident administrators to remove unwanted widgets from the Security Incident Catalog?
When a record is created in the Security Incident Phishing Email table what is triggered to create a Security Incident?
When a service desk agent uses the Create Security Incident UI action from a regular incident, what occurs?
Which of the following fields is used to identify an Event that is to be used for Security purposes?
Flow Triggers can be based on what? (Choose three.)



 Table
Description automatically generated
Table
Description automatically generated