ISC CISSP - Certified Information Systems Security Professional (CISSP)
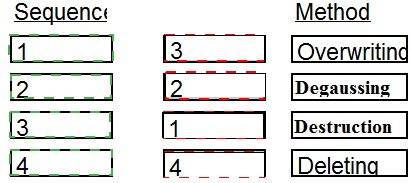
Place in order, from BEST (1) to WORST (4), the following methods to reduce the risk of data remanence on magnetic media.
The Answer Is:
Explanation:
Degaussing
Overwriting
Destruction
Deleting
Comprehensive Explanation: Degaussing is the process of decreasing or eliminating a remnant magnetic field to reduce the risk of data remanence on magnetic media, making it the best method among the options provided. Overwriting involves replacing old data with new data, which can also be effective but not as thorough as degaussing. Destruction refers to physically destroying the media, which is effective but not always practical or environmentally friendly. Deleting is simply removing data pointers and does not actually erase the data from the media, making it the worst option.
References:
CISSP All-in-One Exam Guide, Eighth Edition, Chapter 10, p. 518.
CISSP practice exam questions and answers, Question 7.
Retaining system logs for six months or longer can be valuable for what activities?
Disaster recovery and business continuity
Forensics and incident response
Identity and authorization management
Physical and logical access control
The Answer Is:
BExplanation:
 Retaining system logs for six months or longer can be valuable for forensics and incident response activities. System logs are records of events that occur on a system, such as user actions, system errors, security alerts, network traffic, etc. System logs can provide useful evidence and information for investigating and analyzing security incidents, such as the source, scope, impact, and timeline of the incident, as well as the potential vulnerabilities, threats, and attackers involved. System logs can also help with incident recovery and remediation, as well as with improving security controls and policies12 References: CISSP All-in-One Exam Guide, Eighth Edition, Chapter 7: Security Operations, p. 437; Official (ISC)2 CISSP CBK Reference, Fifth Edition, Domain 7: Security Operations, p. 849.
Which of the following statements is TRUE regarding value boundary analysis as a functional software testing technique?
It is useful for testing communications protocols and graphical user interfaces.
It is characterized by the stateless behavior of a process implemented in a function.
Test inputs are obtained from the derived threshold of the given functional specifications.
An entire partition can be covered by considering only one representative value from that partition.
The Answer Is:
CExplanation:
Value boundary analysis is a functional software testing technique that tests the behavior of a software system or component when it receives inputs that are at the boundary or edge of the expected range of values. Value boundary analysis is based on the assumption that errors are more likely to occur at the boundary values than at the normal values. Test inputs are obtained from the derived threshold of the given functional specifications, such as the minimum, maximum, or just above or below the boundary values. Value boundary analysis can help identify errors or defects in the software system or component that may cause unexpected or incorrect outputs, crashes, or failures34 References: CISSP All-in-One Exam Guide, Eighth Edition, Chapter 8: Software Development Security, p. 497; Official (ISC)2 CISSP CBK Reference, Fifth Edition, Domain 8: Software Development Security, p. 1015.
What is the process called when impact values are assigned to the security objectives for information types?
Qualitative analysis
Quantitative analysis
Remediation
System security categorization
The Answer Is:
DExplanation:
The process called when impact values are assigned to the security objectives for information types is system security categorization. System security categorization is a process of determining the potential impact on an organization if a system or information is compromised, based on the security objectives of confidentiality, integrity, and availability. System security categorization helps to identify the security requirements and controls for the system or information, as well as to prioritize the resources and efforts for protecting them. System security categorization can be based on the standards or guidelines provided by the organization or the relevant authorities, such as the Federal Information Processing Standards (FIPS) Publication 199 or the National Institute of Standards and Technology (NIST) Special Publication 800-6034 References: CISSP All-in-One Exam Guide, Eighth Edition, Chapter 1: Security and Risk Management, p. 29; Official (ISC)2 CISSP CBK Reference, Fifth Edition, Domain 1: Security and Risk Management, p. 31.
The goal of a Business Continuity Plan (BCP) training and awareness program is to
enhance the skills required to create, maintain, and execute the plan.
provide for a high level of recovery in case of disaster.
describe the recovery organization to new employees.
provide each recovery team with checklists and procedures.
The Answer Is:
AExplanation:
 A Business Continuity Plan (BCP) is a document that outlines the processes and procedures that an organization will follow in the event of a disruption or disaster, such as a fire, flood, cyberattack, etc. The BCP aims to ensure the continuity of the organization’s critical functions and minimize the impact of the disruption or disaster on the organization’s operations, assets, and stakeholders. A BCP training and awareness program is a set of activities that educate the organization’s staff and management on the BCP, its objectives, scope, roles, and responsibilities. The goal of a BCP training and awareness program is to enhance the skills required to create, maintain, and execute the plan, as well as to increase the awareness and commitment of the organization’s staff and management to the BCP. Providing for a high level of recovery in case of disaster is not the goal of a BCP training and awareness program, but rather the goal of the BCP itself. Describing the recovery organization to new employees is not the goal of a BCP training and awareness program, but rather a specific task within the program. Providing each recovery team with checklists and procedures is not the goal of a BCP training and awareness program, but rather a specific task within the program. References: Business Continuity Plan (BCP), [CISSP All-in-One Exam Guide, Eighth Edition, Chapter 7: Security Operations]2
What is the MOST efficient way to secure a production program and its data?
Disable default accounts and implement access control lists (ACL)
Harden the application and encrypt the data
Disable unused services and implement tunneling
Harden the servers and backup the data
The Answer Is:
BExplanation:
The most efficient way to secure a production program and its data is to harden the application and encrypt the data. Hardening the application means applying the security best practices and standards to the development, testing, deployment, and maintenance of the application, such as input validation, output encoding, error handling, logging, patching, and configuration. Encrypting the data means applying the cryptographic techniques and algorithms to the data at rest and in transit, such as symmetric encryption, asymmetric encryption, hashing, and digital signatures. These two measures can provide a comprehensive and effective protection for the application and its data against various threats and attacks.
A. Disable default accounts and implement access control lists (ACL) is not the most efficient way to secure a production program and its data, because it only addresses one aspect of security, which is access control. Disabling default accounts and implementing ACLs can prevent unauthorized or inappropriate access to the application and its data, but it does not protect the application and its data from other vulnerabilities or risks, such as injection, cross-site scripting, denial-of-service, or data leakage.
C. Disable unused services and implement tunneling is not the most efficient way to secure a production program and its data, because it only addresses one aspect of security, which is network security. Disabling unused services and implementing tunneling can reduce the attack surface and enhance the confidentiality and integrity of the data in transit, but it does not protect the application and its data from other vulnerabilities or risks, such as logic flaws, broken authentication, insecure storage, or data tampering.
D. Harden the servers and backup the data is not the most efficient way to secure a production program and its data, because it only addresses one aspect of security, which is system security. Hardening the servers and backing up the data can improve the performance and availability of the application and its data, but it does not protect the application and its data from other vulnerabilities or risks, such as code injection, session hijacking, privilege escalation, or data disclosure.
References:Â CISSP All-in-One Exam Guide, Eighth Edition, Chapter 8, page 481;Â Official (ISC)2 CISSP CBK Reference, Fifth Edition, Chapter 8, page 437
A vulnerability in which of the following components would be MOST difficult to detect?
Kernel
Shared libraries
Hardware
System application
The Answer Is:
CExplanation:
 According to the CISSP CBK Official Study Guide, a vulnerability in hardware would be the most difficult to detect. A vulnerability is a weakness or exposure in a system, network, or application, which may be exploited by threats and cause harm to the organization or its assets. A vulnerability can exist in various components of a system, network, or application, such as the kernel, the shared libraries, the hardware, or the system application. A vulnerability in hardware would be the most difficult to detect, as it may require physical access, specialized tools, or advanced skills to identify and measure the vulnerability. Hardware is the physical or tangible component of a system, network, or application that provides the basic functionality, performance, and support for the system, network, or application, such as the processor, memory, disk, or network card. Hardware may have vulnerabilities due to design flaws, manufacturing defects, configuration errors, or physical damage. A vulnerability in hardware may affect the security, reliability, or availability of the system, network, or application, such as causing data leakage, performance degradation, or system failure. A vulnerability in the kernel would not be the most difficult to detect, although it may be a difficult to detect. The kernel is the core or central component of a system, network, or application that provides the basic functionality, performance, and control for the system, network, or application, such as the operating system, the hypervisor, or the firmware. The kernel may have vulnerabilities due to design flaws, coding errors, configuration errors, or malicious modifications. A vulnerability in the kernel may affect the security, reliability, or availability of the system, network, or application, such as causing privilege escalation, system compromise, or system crash. A vulnerability in the kernel may be detected by using various tools, techniques, or methods, such as code analysis, vulnerability scanning, or penetration testing. A vulnerability in the shared libraries would not be the most difficult to detect, although it may be a difficult to detect. The shared libraries are the reusable or common components of a system, network, or application, that provide the functionality, performance, and compatibility for the system, network, or application, such as the dynamic link libraries, the application programming interfaces, or the frameworks.Â
After a thorough analysis, it was discovered that a perpetrator compromised a network by gaining access to the network through a Secure Socket Layer (SSL) Virtual Private Network (VPN) gateway. The perpetrator guessed a username and brute forced the password to gain access. Which of the following BEST mitigates this issue?
Implement strong passwords authentication for VPN
Integrate the VPN with centralized credential stores
Implement an Internet Protocol Security (IPSec) client
Use two-factor authentication mechanisms
The Answer Is:
DExplanation:
The best way to mitigate the issue of a perpetrator compromising a network by gaining access to the network through an SSL VPN gateway by guessing a username and brute forcing the password is to use two-factor authentication mechanisms. Two-factor authentication is a method of verifying the identity of a user or device by requiring two different types of factors, such as something the user knows (e.g., password, PIN, etc.), something the user has (e.g., token, smart card, etc.), or something the user is (e.g., biometric, fingerprint, etc.). Two-factor authentication can enhance the security of the network access by making it harder for attackers to impersonate or compromise the legitimate users or devices. If the perpetrator only knows the username and password, they will not be able to access the network without the second factor, such as a token or a biometric34 References: CISSP All-in-One Exam Guide, Eighth Edition, Chapter 6: Communication and Network Security, p. 321; Official (ISC)2 CISSP CBK Reference, Fifth Edition, Domain 4: Communication and Network Security, p. 449.
Which of the following activities BEST identifies operational problems, security misconfigurations, and malicious attacks?
Policy documentation review
Authentication validation
Periodic log reviews
Interface testing
The Answer Is:
CExplanation:
The activity that best identifies operational problems, security misconfigurations, and malicious attacks is periodic log reviews. Log reviews are the process of examining and analyzing the records of events or activities that occur on a system or network, such as user actions, system errors, security alerts, or network traffic. Periodic log reviews can help to identify operational problems, such as system failures, performance issues, or configuration errors, by detecting anomalies, trends, or patterns in the log data. Periodic log reviews can also help to identify security misconfigurations, such as weak passwords, open ports, or missing patches, by comparing the log data with the security policies, standards, or baselines. Periodic log reviews can also help to identify malicious attacks, such as unauthorized access, data breaches, or denial of service, by recognizing signs of intrusion, compromise, or exploitation in the log data. The other options are not the best activities to identify operational problems, security misconfigurations, and malicious attacks, but rather different types of activities. Policy documentation review is the process of examining and evaluating the documents that define the rules and guidelines for the system or network security, such as policies, procedures, or standards. Policy documentation review can help to ensure the completeness, consistency, and compliance of the security documents, but not to identify the actual problems or attacks. Authentication validation is the process of verifying and confirming the identity and credentials of a user or device that requests access to a system or network, such as passwords, tokens, or certificates. Authentication validation can help to prevent unauthorized access, but not to identify the existing problems or attacks. Interface testing is the process of checking and evaluating the functionality, usability, and reliability of the interfaces between different components or systems, such as modules, applications, or networks. Interface testing can help to ensure the compatibility, interoperability, and integration of the interfaces, but not to identify the problems or attacks. References: CISSP All-in-One Exam Guide, Eighth Edition, Chapter 7, p. 377; Official (ISC)2 CISSP CBK Reference, Fifth Edition, Chapter 7, p. 405.
Which of the following BEST describes the purpose of performing security certification?
To identify system threats, vulnerabilities, and acceptable level of risk
To formalize the confirmation of compliance to security policies and standards
To formalize the confirmation of completed risk mitigation and risk analysis
To verify that system architecture and interconnections with other systems are effectively implemented
The Answer Is:
BExplanation:
 The best description of the purpose of performing security certification is to formalize the confirmation of compliance to security policies and standards. Security certification is the process of evaluating and validating the security posture and compliance of a system or network against a set of predefined criteria, such as security policies, standards, regulations, or best practices. Security certification results in a formal statement or document that attests the level of security and compliance achieved by the system or network.
A. To identify system threats, vulnerabilities, and acceptable level of risk is not the best description of the purpose of performing security certification, but rather the purpose of performing security assessment. Security assessment is the process of identifying and analyzing the security threats, vulnerabilities, and risks of a system or network, and determining the acceptable level of risk and the risk mitigation strategies.
C. To formalize the confirmation of completed risk mitigation and risk analysis is not the best description of the purpose of performing security certification, but rather the purpose of performing security accreditation. Security accreditation is the process of authorizing and approving the operation of a system or network based on the results of security certification and risk analysis, and the acceptance of residual risk.
D. To verify that system architecture and interconnections with other systems are effectively implemented is not the best description of the purpose of performing security certification, but rather one of the possible aspects or objectives of security certification. Security certification can cover various aspects of system security, such as architecture, design, implementation, configuration, operation, maintenance, or interconnection.
References:Â CISSP All-in-One Exam Guide, Eighth Edition, Chapter 3, page 147;Â Official (ISC)2 CISSP CBK Reference, Fifth Edition, Chapter 3, page 123
Which of the following prevents improper aggregation of privileges in Role Based Access Control (RBAC)?
Hierarchical inheritance
Dynamic separation of duties
The Clark-Wilson security model
The Bell-LaPadula security model
The Answer Is:
BExplanation:
The method that prevents improper aggregation of privileges in role based access control (RBAC) is dynamic separation of duties. RBAC is a type of access control model that assigns permissions and privileges to users or devices based on their roles or functions within an organization, rather than their identities or attributes. RBAC can simplify and streamline the access control management, as it can reduce the complexity and redundancy of the permissions and privileges. However, RBAC can also introduce the risk of improper aggregation of privileges, which is the situation where a user or a device can accumulate more permissions or privileges than necessary or appropriate for their role or function, either by having multiple roles or by changing roles over time. Dynamic separation of duties is a method that prevents improper aggregation of privileges in RBAC, by enforcing rules or constraints that limit or restrict the roles or the permissions that a user or a device can have or use at any given time or situation.
A. Hierarchical inheritance is not a method that prevents improper aggregation of privileges in RBAC, but rather a method that enables proper delegation of privileges in RBAC. Hierarchical inheritance is a method that allows the roles or the permissions in RBAC to be organized and structured in a hierarchical or a tree-like manner, where the higher-level roles or permissions can inherit or include the lower-level roles or permissions. Hierarchical inheritance can facilitate the delegation of privileges in RBAC, as it can ensure that the roles or the permissions are consistent and compatible with the organizational hierarchy or the business logic.
C. The Clark-Wilson security model is not a method that prevents improper aggregation of privileges in RBAC, but rather a type of access control model that enforces the integrity or the accuracy of the data or the transactions within an information system. The Clark-Wilson security model is a type of access control model that defines and regulates the access and the operations that the users or the devices can perform on the data or the transactions, based on the concepts of well-formed transactions, separation of duties, and auditing. The Clark-Wilson security model can prevent unauthorized or improper modification or manipulation of the data or the transactions, by ensuring that the access and the operations are valid and verified.
D. The Bell-LaPadula security model is not a method that prevents improper aggregation of privileges in RBAC, but rather a type of access control model that enforces the confidentiality or the secrecy of the data or the information within an information system. The Bell-LaPadula security model is a type of access control model that defines and regulates the access and the operations that the users or the devices can perform on the data or the information, based on the concepts of security levels, security labels, and security rules. The Bell-LaPadula security model can prevent unauthorized or improper disclosure or leakage of the data or the information, by ensuring that the access and the operations are consistent and compliant with the security policies.
References:Â CISSP All-in-One Exam Guide, Eighth Edition, Chapter 6, page 349;Â Official (ISC)2 CISSP CBK Reference, Fifth Edition, Chapter 6, page 310
Which of the following is needed to securely distribute symmetric cryptographic keys?
Officially approved Public-Key Infrastructure (PKI) Class 3 or Class 4 certificates
Officially approved and compliant key management technology and processes
An organizationally approved communication protection policy and key management plan
Hardware tokens that protect the user’s private key.
The Answer Is:
BExplanation:
According to the CISSP All-in-One Exam Guide2, the thing that is needed to securely distribute symmetric cryptographic keys is officially approved and compliant key management technology and processes. Symmetric cryptography is a type of cryptography that uses the same key to encrypt and decrypt the data or information, such as the Advanced Encryption Standard (AES) or the Data Encryption Standard (DES). Symmetric cryptographic keys are the secret or random values that are used to perform the encryption and decryption operations, such as the 128-bit or 256-bit keys. Key management is the process of generating, distributing, storing, using, changing, and destroying the cryptographic keys, as well as the policies and procedures that govern the process. Key management technology and processes are the tools and methods that are used to implement and perform the key management process, such as the key distribution protocols, the key servers, or the key lifecycle models. Key management technology and processes need to be officially approved and compliant, which means that they need to meet the standards, regulations, and requirements that are established by the authorities or organizations that oversee or regulate the cryptography or the security of the data or information, such as the National Institute of Standards and Technology (NIST) or the Payment Card Industry Data Security Standard (PCI DSS). Officially approved and compliant key management technology and processes are needed to securely distribute symmetric cryptographic keys, as they ensure that the keys are generated, distributed, stored, used, changed, and destroyed in a secure and consistent manner, and that the keys are protected from unauthorized or unintended access, disclosure, modification, corruption, loss, or theft. Officially approved Public-Key Infrastructure (PKI) Class 3 or Class 4 certificates are not the things that are needed to securely distribute symmetric cryptographic keys, although they may be the things that are needed to securely distribute asymmetric cryptographic keys. PKI is a system or a framework that provides the services and mechanisms for the creation, management, distribution, and verification of the digital certificates, which are the electronic documents that bind the identity and the public key of an entity, such as a person, a device, or an organization. PKI uses asymmetric cryptography, which is a type of cryptography that uses a pair of keys to encrypt and decrypt the data or information, such as the Rivest-Shamir-Adleman (RSA) or the Elliptic Curve Cryptography (ECC). Asymmetric cryptographic keys are the public or private values that are used to perform the encryption and decryption operations, such as the 2048-bit or 4096-bit keys. PKI certificates are classified into different classes or levels, based on the identity verification and assurance requirements, such as Class 1, Class 2, Class 3, or Class 4. Class 3 and Class 4 certificates are the highest classes or levels of PKI certificates, which require the most rigorous and stringent identity verification and assurance processes, such as the face-to-face or the in-person verification. Class 3 and Class 4 certificates are used for the high-security or high-value applications or transactions, such as the e-commerce, the e-government, or the e-banking. Class 3 and Class 4 certificates may help to securely distribute asymmetric cryptographic keys, as they ensure that the public keys are authentic, valid, and trustworthy, and that the identity and the public key of the entity are properly and securely bound. However, Class 3 and Class 4 certificates are not the things that are needed to securely distribute symmetric cryptographic keys, as they are not related to the symmetric cryptography or the symmetric cryptographic keys. An organizationally approved communication protection policy and key management plan is not the thing that is needed to securely distribute symmetric cryptographic keys, although it may be a document that guides or supports the key management technology and processes. A communication protection policy is a document that defines the rules, principles, and guidelines for the protection of the data or information that is transmitted or received over the communication channels or networks, such as the encryption, authentication, or integrity methods or mechanisms. A key management plan is a document that defines the objectives, scope, roles, and responsibilities for the key management process, as well as the policies and procedures for the key management process, such as the key generation, distribution, storage, use, change, and destruction policies and procedures. An organizationally approved communication protection policy and key management plan may help to guide or support the key management technology and processes, but it is not the thing that is needed to securely distribute symmetric cryptographic keys, as it is not the tool or method that is used to implement or perform the key management process. Hardware tokens that protect the user’s private key are not the things that are needed to securely distribute symmetric cryptographic keys, although they may be the things that are used to store or use the symmetric cryptographic keys. Hardware tokens are the physical or tangible devices that are used to store or use the cryptographic keys, such as the smart cards, the USB drives, or the hardware security modules. Hardware tokens may help to protect the user’s private key, which is the asymmetric cryptographic key that is used to decrypt the data or information, or to sign the data or information, such as the RSA or the ECC private key. Hardware tokens may also help to store or use the symmetric cryptographic key, which is the symmetric cryptographic key that is used to encrypt and decrypt the data or information, such as the AES or the DES key. However, hardware tokens are not the things that are needed to securely distribute symmetric cryptographic keys, as they are not the tools or methods that are used to generate or distribute the symmetric cryptographic keys. References: 2
What operations role is responsible for protecting the enterprise from corrupt or contaminated media?
Information security practitioner
Information librarian
Computer operator
Network administrator
The Answer Is:
BExplanation:
According to the CISSP CBK Official Study Guide1, an information librarian is responsible for managing, maintaining, and protecting the organization’s knowledge resources, including ensuring that media (such as hard drives, USBs, CDs) are free from corruption or contamination to protect the enterprise’s data integrity. An information librarian is also responsible for cataloging, indexing, and classifying the media, as well as providing access and retrieval services to the authorized users. An information librarian may also perform backup, recovery, and disposal of the media, as well as monitor and audit the usage and security of the media. An information security practitioner is not the operations role that is responsible for protecting the enterprise from corrupt or contaminated media, although they may be involved in defining and enforcing the policies and standards for the media security. An information security practitioner is a general term for a person who performs various functions and tasks related to the information security of the organization, such as planning, designing, implementing, testing, operating, or auditing the information security systems and controls. An information security practitioner may also provide guidance, advice, and training to the other roles and stakeholders on the information security matters. A computer operator is not the operations role that is responsible for protecting the enterprise from corrupt or contaminated media, although they may be involved in using and handling the media. A computer operator is a person who operates and controls the computer systems and devices of the organization, such as the servers, workstations, printers, or scanners. A computer operator may also perform tasks such as loading and unloading the media, running and monitoring the programs and applications, troubleshooting and resolving the errors and problems, and reporting and documenting the activities and incidents. A network administrator is not the operations role that is responsible for protecting the enterprise from corrupt or contaminated media, although they may be involved in configuring and connecting the media. A network administrator is a person who administers and manages the network systems and devices of the organization, such as the routers, switches, firewalls, or wireless access points. A network administrator may also perform tasks such as installing and updating the network software and hardware, setting and maintaining the network parameters and security, optimizing and troubleshooting the network performance and availability, and supporting and assisting the network users and clients. References: 1
Which of the following adds end-to-end security inside a Layer 2 Tunneling Protocol (L2TP) Internet Protocol Security (IPSec) connection?
Temporal Key Integrity Protocol (TKIP)
Secure Hash Algorithm (SHA)
Secure Shell (SSH)
Transport Layer Security (TLS)
The Answer Is:
DExplanation:
 According to the CISSP CBK Official Study Guide1, the protocol that adds end-to-end security inside a Layer 2 Tunneling Protocol (L2TP) Internet Protocol Security (IPSec) connection is Transport Layer Security (TLS). L2TP is a tunneling protocol that is used or applied to create or establish a virtual private network (VPN) connection between two or more systems or networks, by using or applying the Layer 2 or the data-link layer of the Open System Interconnection (OSI) Reference Model, which is the layer that defines the logical or the intangible aspects of the communication or the networking system, such as the frames, addresses, or protocols that organize or control the data or the information. IPSec is a security protocol that is used or applied to secure or protect the VPN connection between two or more systems or networks, by using or applying the Layer 3 or the network layer of the OSI Reference Model, which is the layer that defines the routing or the forwarding aspects of the communication or the networking system, such as the packets, addresses, or protocols that determine or direct the path or the route of the data or the information. IPSec helps to ensure the security or the integrity of the VPN connection between two or more systems or networks, by providing or supporting the confidentiality, integrity, authentication, or non-repudiation of the data or the information that passes through the VPN connection, by using or applying the appropriate methods or mechanisms, such as the encryption, hashing, digital signature, or key exchange of the data or the information. TLS is a security protocol that is used or applied to secure or protect the application or the service that runs or operates inside the VPN connection between two or more systems or networks, by using or applying the Layer 4 or the transport layer of the OSI Reference Model, which is the layer that defines the reliability or the quality aspects of the communication or the networking system, such as the segments, ports, or protocols that ensure or verify the delivery or the transmission of the data or the information. TLS helps to ensure the security or the integrity of the application or the service that runs or operates inside the VPN connection between two or more systems or networks, by providing or supporting the confidentiality, integrity, authentication, or non-repudiation of the data or the information that passes through the application or the service, by using or applying the appropriate methods or mechanisms, such as the encryption, hashing, digital signature, or key exchange of the data or the information. TLS adds end-to-end security inside the L2TP IPSec connection, as it provides or supports an additional layer or level of security or protection to the data or the information that passes through the VPN connection between two or more systems or networks, as well as the application or the service that runs or operates inside the VPN connection between two or more systems or networks, by securing or protecting the data or the information from the source or the origin to the destination or the end of the VPN connection, as well as the application or the service, regardless or irrespective of the intermediate or the intermediate systems or networks that are involved or included in the VPN connection, as well as the application or the service. TKIP is not the protocol that adds end-to-end security inside the L2TP IPSec connection, although it may be a benefit or a consequence of using TLS.
Which of the following is a function of Security Assertion Markup Language (SAML)?
File allocation
Redundancy check
Extended validation
Policy enforcement
The Answer Is:
DExplanation:
A function of Security Assertion Markup Language (SAML) is policy enforcement. SAML is an XML-based standard for exchanging authentication and authorization information between different entities, such as service providers and identity providers. SAML enables policy enforcement by allowing the service provider to specify the security requirements and conditions for accessing its resources, and allowing the identity provider to assert the identity and attributes of the user who requests access. The other options are not functions of SAML, but rather different concepts or technologies. File allocation is the process of assigning disk space to files. Redundancy check is a method of detecting errors in data transmission or storage. Extended validation is a type of certificate that provides a higher level of assurance for the identity of the website owner. References: CISSP All-in-One Exam Guide, Eighth Edition, Chapter 5, p. 283; Official (ISC)2 CISSP CBK Reference, Fifth Edition, Chapter 6, p. 361.



