ISC CISSP - Certified Information Systems Security Professional (CISSP)
The BEST method to mitigate the risk of a dictionary attack on a system is to
use a hardware token.
use complex passphrases.
implement password history.
encrypt the access control list (ACL).
The Answer Is:
BExplanation:
The best method to mitigate the risk of a dictionary attack on a system is to use complex passphrases. A dictionary attack is a type of brute force attack that tries to guess or crack a password or a passphrase by using a list or a database of common or frequently used words, phrases, or combinations, such as names, dates, or dictionary words. A complex passphrase is a type of password or a passphrase that consists of a long and random sequence of characters, words, or symbols, that is hard to guess or crack by a dictionary attack or any other attack. A complex passphrase can provide a high level of security and entropy for a system, as it increases the possible combinations and reduces the probability of a successful attack.
A. Use a hardware token is not the best method to mitigate the risk of a dictionary attack on a system, but rather a method of enhancing the security of a system by using multifactor authentication. A hardware token is a type of device or a gadget that generates or stores a secret code or a value that can be used as a factor or a method of authentication, such as a one-time password (OTP), a personal identification number (PIN), or a cryptographic key. A hardware token can provide an additional layer of security and protection for the system, as it can prevent or reduce the risk of unauthorized or inappropriate access or login, by adding an extra layer of verification and validation for the users or the devices.
C. Implement password history is not the best method to mitigate the risk of a dictionary attack on a system, but rather a method of preventing password reuse or recycling by the users or the devices. Password history is a feature or a function that records and stores the previous passwords or passphrases used by the users or the devices, and prevents them from using the same or similar passwords or passphrases again, within a certain period of time or a certain number of changes. Password history can prevent password reuse or recycling by the users or the devices, as it can reduce the risk of compromise or exposure of the passwords or passphrases, by requiring them to use new and different passwords or passphrases periodically or frequently.
D. Encrypt the access control list (ACL) is not the best method to mitigate the risk of a dictionary attack on a system, but rather a method of protecting the access control information or data from unauthorized access or disclosure. An access control list (ACL) is a type of data structure or a file that stores and manages the access control rules or policies for a system or a resource, such as a file, a folder, or a network. An ACL specifies the permissions or the privileges that the users or the devices have or do not have for the system or the resource, such as read, write, execute, or delete. Encrypting the ACL is the process of transforming or encoding the ACL into an unreadable or unintelligible form, using a secret key or algorithm. Encrypting the ACL can protect the access control information or data from unauthorized access or disclosure, as it can prevent or reduce the risk of tampering or modification of the ACL by malicious actors or attackers.
References:Â CISSP All-in-One Exam Guide, Eighth Edition, Chapter 6, page 328;Â Official (ISC)2 CISSP CBK Reference, Fifth Edition, Chapter 6, page 289
The implementation of which features of an identity management system reduces costs and administration overhead while improving audit and accountability?
Two-factor authentication
Single Sign-On (SSO)
User self-service
A metadirectory
The Answer Is:
CExplanation:
 The feature of an identity management system that reduces costs and administration overhead while improving audit and accountability is user self-service. Identity management system is a system that manages the identity and the access of the users or the devices within an organization or a network, by performing the functions or the processes related to the identity and the access lifecycle, such as identification, authentication, authorization, and accountability. User self-service is a feature of an identity management system that allows the users or the devices to perform some of the tasks or the functions related to their identity and access management, such as creating, updating, or deleting their accounts, passwords, or profiles, or requesting, approving, or revoking their access rights or privileges, without requiring the intervention or the assistance of the administrators or the operators. User self-service can reduce the costs and the administration overhead for the organization, as it can decrease the workload and the dependency of the administrators or the operators, and it can increase the efficiency and the productivity of the users or the devices. User self-service can also improve the audit and the accountability for the organization, as it can provide more transparency and traceability of the identity and the access management activities, and it can enhance the compliance and the security of the identity and the access management policies and standards.
A. Two-factor authentication is not a feature of an identity management system that reduces costs and administration overhead while improving audit and accountability, but rather a feature of an identity management system that enhances the security and the reliability of the identity and the access management. Two-factor authentication is a feature of an identity management system that verifies the identity and the legitimacy of the users or the devices by requiring two or more factors or methods of authentication, such as something the user knows (e.g., password, PIN, or security question), something the user has (e.g., token, card, or smartphone), or something the user is (e.g., fingerprint, face, or voice). Two-factor authentication can enhance the security and the reliability of the identity and the access management, as it can prevent or reduce the risk of unauthorized or inappropriate access or login, by adding an extra layer of protection and verification for the users or the devices.
B. Single sign-on (SSO) is not a feature of an identity management system that reduces costs and administration overhead while improving audit and accountability, but rather a feature of an identity management system that improves the usability and the convenience of the identity and the access management. SSO is a feature of an identity management system that allows the users or the devices to access multiple or different applications, systems, or networks, by using a single or a common set of credentials, such as a username and a password, or a token and a PIN, without requiring to authenticate or to login separately or repeatedly for each application, system, or network. SSO can improve the usability and the convenience of the identity and the access management, as it can simplify and streamline the access and the login process for the users or the devices, and it can reduce the complexity and the redundancy of the credentials.
D. A metadirectory is not a feature of an identity management system that reduces costs and administration overhead while improving audit and accountability, but rather a feature of an identity management system that enables the integration and the synchronization of the identity and the access management. A metadirectory is a feature of an identity management system that stores and manages the identity and the access information of the users or the devices from multiple or different sources, such as directories, databases, or applications, and provides a unified and consistent view and access of the identity and the access information for the users or the devices. A metadirectory can enable the integration and the synchronization of the identity and the access management, as it can support the interoperability and the compatibility of the identity and the access information across different platforms, systems, or networks, and it can ensure the accuracy and the currency of the identity and the access information.
Between which pair of Open System Interconnection (OSI) Reference Model layers are routers used as a communications device?
Transport and Session
Data-Link and Transport
Network and Session
Physical and Data-Link
The Answer Is:
CExplanation:
According to the CISSP CBK Official Study Guide1, routers are used as a communications device between the network and session layers of the Open System Interconnection (OSI) Reference Model. The OSI Reference Model is a conceptual framework or a standard that defines the functions and processes of the communication or the networking system, which consists of seven layers, which are:
Physical: The layer that defines the physical or the tangible aspects of the communication or the networking system, such as the cables, connectors, or signals that transmit or receive the data or the information.
Data-Link: The layer that defines the logical or the intangible aspects of the communication or the networking system, such as the frames, addresses, or protocols that organize or control the data or the information.
Network: The layer that defines the routing or the forwarding aspects of the communication or the networking system, such as the packets, addresses, or protocols that determine or direct the path or the route of the data or the information.
Transport: The layer that defines the reliability or the quality aspects of the communication or the networking system, such as the segments, ports, or protocols that ensure or verify the delivery or the transmission of the data or the information.
Session: The layer that defines the connection or the interaction aspects of the communication or the networking system, such as the dialogs, tokens, or protocols that establish or maintain the session or the communication between the systems or the networks.
Presentation: The layer that defines the format or the representation aspects of the communication or the networking system, such as the encryption, compression, or translation of the data or the information.
Application: The layer that defines the functionality or the service aspects of the communication or the networking system, such as the applications, programs, or protocols that provide or support the functions or the services of the system or the network.
Routers are used as a communications device between the network and session layers of the OSI Reference Model, as they perform the functions or the tasks that are related to the network and session layers, such as:
Routing or forwarding the packets or the data between the systems or the networks, based on the network addresses or the protocols, such as the Internet Protocol (IP) addresses or the Internet Protocol (IP) protocols, which are defined or specified at the network layer of the OSI Reference Model.
Establishing or maintaining the sessions or the communications between the systems or the networks, based on the dialogs, tokens, or protocols, such as the Border Gateway Protocol (BGP) or the Open Shortest Path First (OSPF) protocols, which are defined or specified at the session layer of the OSI Reference Model.
Transport and session is not the pair of OSI Reference Model layers between which routers are used as a communications device, as routers do not perform the functions or the tasks that are related to the transport layer of the OSI Reference Model, such as ensuring or verifying the delivery or the transmission of the data or the information, based on the segments, ports, or protocols, such as the Transmission Control Protocol (TCP) or the User Datagram Protocol (UDP) protocols, which are defined or specified at the transport layer of the OSI Reference Model. Data-Link and transport is not the pair of OSI Reference Model layers between which routers are used as a communications device, as routers do not perform the functions or the tasks that are related to the data-link layer of the OSI Reference Model, such as organizing or controlling the data or the information, based on the frames, addresses, or protocols, such as the Media Access Control (MAC) addresses or the Ethernet protocols, which are defined or specified at the data-link layer of the OSI Reference Model. Physical and data-link is not the pair of OSI Reference Model layers between which routers are used as a communications device, as routers do not perform the functions or the tasks that are related to the physical layer of the OSI Reference Model, such as transmitting or receiving the data or the information, based on the cables, connectors, or signals, which are defined or specified at the physical layer of the OSI Reference Model. References: 1
Which of the following countermeasures is the MOST effective in defending against a social engineering attack?
Mandating security policy acceptance
Changing individual behavior
Evaluating security awareness training
Filtering malicious e-mail content
The Answer Is:
BExplanation:
According to the CISSP CBK Official Study Guide, the countermeasure that is the most effective in defending against a social engineering attack is changing individual behavior. A social engineering attack is an attack that exploits or manipulates the human or the psychological aspects of the system or the network, such as the trust, curiosity, or greed of the users or the employees, rather than the technical or the logical aspects of the system or the network, such as the hardware, software, or firmware of the system or the network. A social engineering attack may use various techniques or methods, such as the phishing, the baiting, or the pretexting of the users or the employees, to persuade or deceive them into performing or disclosing something that may compromise or harm the security or the integrity of the system or the network, such as the passwords, usernames, or data of the system or the network. The countermeasure that is the most effective in defending against a social engineering attack is changing individual behavior, as it addresses or targets the root cause or the source of the social engineering attack, which is the human or the psychological aspect of the system or the network, such as the trust, curiosity, or greed of the users or the employees. Changing individual behavior is the process of modifying or altering the actions or the reactions of the users or the employees, by using or applying the appropriate methods or mechanisms, such as the education, training, or awareness of the users or the employees. Changing individual behavior helps to prevent or mitigate the social engineering attack, as it reduces or eliminates the vulnerability or the susceptibility of the users or the employees to the social engineering attack, by increasing or enhancing their knowledge, skills, or awareness of the social engineering attack, as well as their ability, confidence, or readiness to resist or respond to the social engineering attack. Mandating security policy acceptance is not the countermeasure that is the most effective in defending against a social engineering attack, although it may be a benefit or a consequence of changing individual behavior.
From a cryptographic perspective, the service of non-repudiation includes which of the following features?
Validity of digital certificates
Validity of the authorization rules
Proof of authenticity of the message
Proof of integrity of the message
The Answer Is:
DExplanation:
the service of non-repudiation from a cryptographic perspective includes the proof of integrity of the message. This means that non-repudiation is a service that ensures that the sender of a message cannot deny sending it, and the receiver of a message cannot deny receiving it, by providing evidence that the message has not been altered or tampered with during transmission. Non-repudiation can be achieved by using digital signatures and certificates, which are cryptographic techniques that bind the identity of the sender to the content of the message, and verify that the message has not been modified. Non-repudiation does not include the validity of digital certificates, as this is a service that ensures that the certificates are authentic, current, and trustworthy, by checking their expiration dates, revocation status, and issuing authorities. Non-repudiation does not include the validity of the authorization rules, as this is a service that ensures that the access to a resource is granted or denied based on the policies and permissions defined by the owner or administrator. Non-repudiation does not include the proof of authenticity of the message, as this is a service that ensures that the message comes from the claimed sender, by verifying their identity and credentials.Â
Which of the following is a reason to use manual patch installation instead of automated patch management?
The cost required to install patches will be reduced.
The time during which systems will remain vulnerable to an exploit will be decreased.
The likelihood of system or application incompatibilities will be decreased.
The ability to cover large geographic areas is increased.
The Answer Is:
CExplanation:
Manual patch installation allows for thorough testing before deployment to ensure that the patch does not introduce new vulnerabilities or incompatibilities. Automated patch management can sometimes lead to unexpected issues if patches are not fully compatible with all systems and applications12 References: CISSP All-in-One Exam Guide, Eighth Edition, Chapter 7: Security Operations, p. 452; Official (ISC)2 CISSP CBK Reference, Fifth Edition, Domain 7: Security Operations, p. 863.
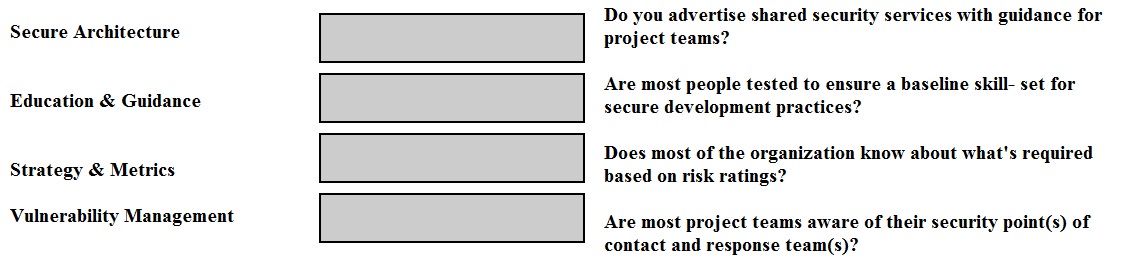
Match the objectives to the assessment questions in the governance domain of Software Assurance Maturity Model (SAMM).
The Answer Is:
Explanation:
The correct matches are as follows:
Secure Architecture -> Do you advertise shared security services with guidance for project teams?
Education & Guidance -> Are most people tested to ensure a baseline skill-set for secure development practices?
Strategy & Metrics -> Does most of the organization know about what’s required based on risk ratings?
Vulnerability Management -> Are most project teams aware of their security point(s) of contact and response team(s)?
Comprehensive Explanation: These matches are based on the definitions and objectives of the four governance domain practices in the Software Assurance Maturity Model (SAMM). SAMM is a framework to help organizations assess and improve their software security posture. The governance domain covers the organizational aspects of software security, such as policies, metrics, and roles.
Secure Architecture: This practice aims to provide a consistent and secure design for software projects, as well as reusable security services and components. The assessment question measures the availability and guidance of these shared security services for project teams.
Education & Guidance: This practice aims to raise the awareness and skills of the staff involved in software development, as well as provide them with the necessary tools and resources. The assessment question measures the level of testing and verification of the staff’s secure development knowledge and abilities.
Strategy & Metrics: This practice aims to define and communicate the software security strategy, goals, and priorities, as well as measure and monitor the progress and effectiveness of software security activities. The assessment question measures the degree of awareness and alignment of the organization with the risk-based requirements for software security.
Vulnerability Management: This practice aims to identify and remediate the vulnerabilities in the software products, as well as prevent or mitigate the impact of potential incidents. The assessment question measures the level of awareness and collaboration of the project teams with the security point(s) of contact and response team(s).
References:Â SAMM Governance Domain;Â Official (ISC)2 CISSP CBK Reference, Fifth Edition, Chapter 8, page 452

Which of the following is the MOST important goal of information asset valuation?
Developing a consistent and uniform method of controlling access on information assets
Developing appropriate access control policies and guidelines
Assigning a financial value to an organization’s information assets
Determining the appropriate level of protection
The Answer Is:
CExplanation:
 According to the CISSP All-in-One Exam Guide2, the most important goal of information asset valuation is to assign a financial value to an organization’s information assets. Information asset valuation is the process of estimating the worth or importance of the information assets that an organization owns, creates, uses, or maintains, such as data, documents, records, or intellectual property. Information asset valuation helps the organization to measure the impact and return of its information assets, as well as to determine the appropriate level of protection, investment, and management for them. Information asset valuation also helps the organization to comply with the legal, regulatory, and contractual obligations that may require the disclosure or reporting of the value of its information assets. Developing a consistent and uniform method of controlling access on information assets is not the most important goal of information asset valuation, although it may be a benefit or outcome of it. Controlling access on information assets is the process of granting or denying the rights and permissions to access, use, modify, or disclose the information assets, based on the identity, role, or need of the users or processes. Controlling access on information assets helps the organization to protect the confidentiality, integrity, and availability of its information assets, as well as to enforce the security policies and standards for them. Developing appropriate access control policies and guidelines is not the most important goal of information asset valuation, although it may be a benefit or outcome of it. Access control policies and guidelines are the documents that define the rules, principles, and procedures for controlling access on information assets, as well as the roles and responsibilities of the stakeholders involved. Access control policies and guidelines help the organization to establish and communicate the expectations and requirements for controlling access on information assets, as well as to monitor and audit the compliance and effectiveness of the access control mechanisms. Determining the appropriate level of protection is not the most important goal of information asset valuation, although it may be a benefit or outcome of it. The level of protection is the degree or extent of the security measures and controls that are applied to the information assets, to prevent or mitigate the potential threats and risks that may affect them. The level of protection should be proportional to the value and sensitivity of the information assets, as well as the impact and likelihood of the threats and risks. References: 2
Which of the following is the MOST effective method of mitigating data theft from an active user workstation?
Implement full-disk encryption
Enable multifactor authentication
Deploy file integrity checkers
Disable use of portable devices
The Answer Is:
DExplanation:
The most effective method of mitigating data theft from an active user workstation is to disable use of portable devices. Portable devices are the devices that can be easily connected to or disconnected from a workstation, such as USB drives, external hard drives, flash drives, or smartphones. Portable devices can pose a risk of data theft from an active user workstation, as they can be used to copy, transfer, or exfiltrate data from the workstation, either by malicious insiders or by unauthorized outsiders. By disabling use of portable devices, the data theft from an active user workstation can be prevented or reduced.
A. Implement full-disk encryption is not the most effective method of mitigating data theft from an active user workstation, but rather a method of mitigating data theft from a lost or stolen user workstation. Full-disk encryption is the process of transforming or encoding the entire data on a disk or a device into an unreadable or unintelligible form, using a secret key or algorithm. Full-disk encryption can protect the data from unauthorized access or disclosure if the disk or the device is lost or stolen, but it does not protect the data from unauthorized copying or transferring if the disk or the device is active and unlocked.
B. Enable multifactor authentication is not the most effective method of mitigating data theft from an active user workstation, but rather a method of mitigating unauthorized access or login to a user workstation. Multifactor authentication is the process of verifying the identity and the legitimacy of a user or a device by requiring two or more factors or methods of authentication, such as something the user knows (e.g., password, PIN, or security question), something the user has (e.g., token, card, or smartphone), or something the user is (e.g., fingerprint, face, or voice). Multifactor authentication can prevent or reduce unauthorized access or login to a user workstation, but it does not prevent or reduce data theft from an active user workstation, especially by malicious insiders who have legitimate access or login credentials.
C. Deploy file integrity checkers is not the most effective method of mitigating data theft from an active user workstation, but rather a method of detecting data tampering or corruption on a user workstation. File integrity checkers are the software tools or applications that monitor and verify the integrity or the authenticity of the files or the programs on a workstation, by using cryptographic techniques, such as hashing, digital signatures, or certificates. File integrity checkers can detect data tampering or corruption on a user workstation, but they cannot prevent or reduce data theft from an active user workstation, as they do not prevent or restrict data copying or transferring.
References:Â CISSP All-in-One Exam Guide, Eighth Edition, Chapter 6, page 330;Â Official (ISC)2 CISSP CBK Reference, Fifth Edition, Chapter 6, page 291
What is the MOST important element when considering the effectiveness of a training program for Business Continuity (BC) and Disaster Recovery (DR)?
Management support
Consideration of organizational need
Technology used for delivery
Target audience
The Answer Is:
AExplanation:
 The effectiveness of a BC/DR training program largely depends on management support because it ensures adequate resources, prioritization, and enforcement of policies are in place to make the training effective across the organization. References: ISC2 CISSP
The MAIN reason an organization conducts a security authorization process is to
force the organization to make conscious risk decisions.
assure the effectiveness of security controls.
assure the correct security organization exists.
force the organization to enlist management support.
The Answer Is:
AExplanation:
The main reason an organization conducts a security authorization process is to force the organization to make conscious risk decisions. A security authorization process is a process that evaluates and approves the security of an information system or a product before it is deployed or used. A security authorization process involves three steps: security categorization, security assessment, and security authorization. Security categorization is the step of determining the impact level of the information system or product on the confidentiality, integrity, and availability of the information and assets. Security assessment is the step of testing and verifying the security controls and measures implemented on the information system or product. Security authorization is the step of granting or denying the permission to operate or use the information system or product based on the security assessment results and the risk acceptance criteria. The security authorization process forces the organization to make conscious risk decisions, as it requires the organization to identify, analyze, and evaluate the risks associated with the information system or product, and to decide whether to accept, reject, mitigate, or transfer the risks. The other options are not the main reasons, but rather the benefits or outcomes of a security authorization process. Assuring the effectiveness of security controls is a benefit of a security authorization process, as it provides an objective and independent evaluation of the security controls and measures. Assuring the correct security organization exists is an outcome of a security authorization process, as it establishes the roles and responsibilities of the security personnel and stakeholders. Forcing the organization to enlist management support is an outcome of a security authorization process, as it involves the management in the risk decision making and approval process. References: CISSP All-in-One Exam Guide, Eighth Edition, Chapter 8, p. 419; Official (ISC)2 CISSP CBK Reference, Fifth Edition, Chapter 3, p. 150.
Denial of Service (DoS) attack
Address Resolution Protocol (ARP) spoof
Buffer overflow
Ping flood attack
The Answer Is:
AExplanation:
A Denial of Service (DoS) attack is an attempt to make a system or network unavailable or unresponsive by overwhelming it with excessive traffic or requests. A flood of malformed packets is a type of DoS attack that exploits the vulnerability of some systems or protocols to process packets that do not conform to the expected format or structure. These packets can cause errors, crashes, or resource exhaustion on the target system or network, preventing legitimate users from accessing it123. References:
CISSP - Certified Information Systems Security Professional, Domain 4: Communication and Network Security, Section: Secure Network Components
[(ISC)2 CISSP Certified Information Systems Security Professional Official Study Guide, 9th Edition], Chapter 10: Communication and Network Security, Section: Network Attacks, Page: 471
CISSP Exam Outline, Domain 4: Communication and Network Security, Section: Implement secure communication channels according to design, Subsection: Prevent or mitigate network attacks
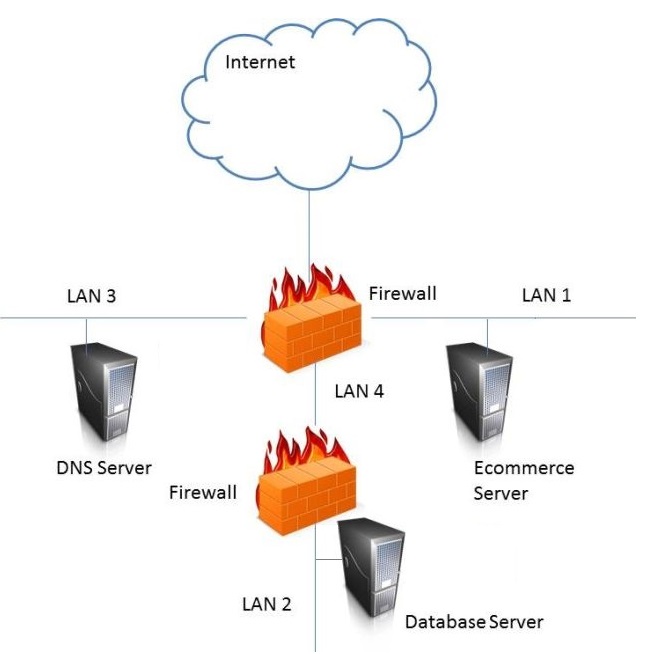
In the network design below, where is the MOST secure Local Area Network (LAN) segment to deploy a Wireless Access Point (WAP) that provides contractors access to the Internet and authorized enterprise services?
The Answer Is:
Explanation:
LAN 4
The most secure LAN segment to deploy a WAP that provides contractors access to the Internet and authorized enterprise services is LAN 4. A WAP is a device that enables wireless devices to connect to a wired network using Wi-Fi, Bluetooth, or other wireless standards. A WAP can provide convenience and mobility for the users, but it can also introduce security risks, such as unauthorized access, eavesdropping, interference, or rogue access points. Therefore, a WAP should be deployed in a secure LAN segment that can isolate the wireless traffic from the rest of the network and apply appropriate security controls and policies. LAN 4 is connected to the firewall that separates it from the other LAN segments and the Internet. This firewall can provide network segmentation, filtering, and monitoring for the WAP and the wireless devices. The firewall can also enforce the access rules and policies for the contractors, such as allowing them to access the Internet and some authorized enterprise services, but not the other LAN segments that may contain sensitive or critical data or systems34 References: CISSP All-in-One Exam Guide, Eighth Edition, Chapter 6: Communication and Network Security, p. 317; Official (ISC)2 CISSP CBK Reference, Fifth Edition, Domain 4: Communication and Network Security, p. 437.
What is the GREATEST challenge to identifying data leaks?
Available technical tools that enable user activity monitoring.
Documented asset classification policy and clear labeling of assets.
Senior management cooperation in investigating suspicious behavior.
Law enforcement participation to apprehend and interrogate suspects.
The Answer Is:
BExplanation:
 The greatest challenge to identifying data leaks is having a documented asset classification policy and clear labeling of assets. Data leaks are the unauthorized or accidental disclosure or exposure of sensitive or confidential data, such as personal information, trade secrets, or intellectual property. Data leaks can cause serious damage or harm to the data owner, such as reputation loss, legal liability, or competitive disadvantage. The greatest challenge to identifying data leaks is having a documented asset classification policy and clear labeling of assets, which means that the organization has defined and implemented the rules and guidelines for categorizing and marking the data according to their sensitivity, value, or criticality. Having a documented asset classification policy and clear labeling of assets can help to identify data leaks by enabling the detection, tracking, and reporting of the data movements, access, or usage, and by alerting the data owner, custodian, or user of any unauthorized or abnormal data activities or incidents. The other options are not the greatest challenges, but rather the benefits or enablers of identifying data leaks. Available technical tools that enable user activity monitoring are not the greatest challenges, but rather the benefits, of identifying data leaks, as they can provide the means or mechanisms for collecting, analyzing, and auditing the data actions or behaviors of the users or devices. Senior management cooperation in investigating suspicious behavior is not the greatest challenge, but rather the enabler, of identifying data leaks, as it can provide the support or authority for conducting the data leak investigation and taking the appropriate actions or measures. Law enforcement participation to apprehend and interrogate suspects is not the greatest challenge, but rather the enabler, of identifying data leaks, as it can provide the assistance or collaboration for pursuing and prosecuting the data leak perpetrators or offenders. References: CISSP All-in-One Exam Guide, Eighth Edition, Chapter 1, p. 29; Official (ISC)2 CISSP CBK Reference, Fifth Edition, Chapter 5, p. 287.
Which Web Services Security (WS-Security) specification negotiates how security tokens will be issued, renewed and validated? Click on the correct specification in the image below.
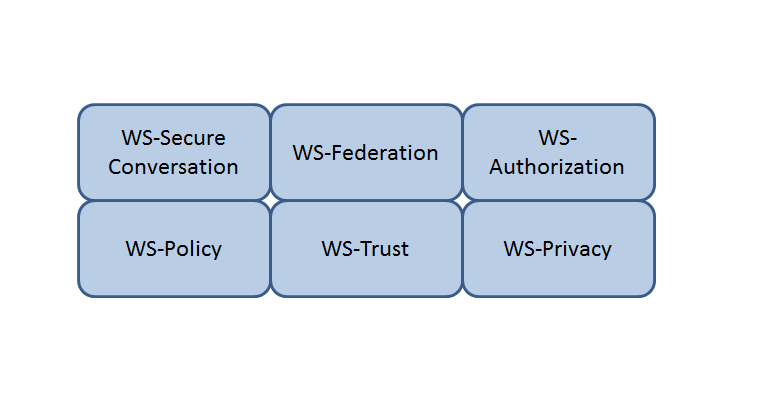
The Answer Is:
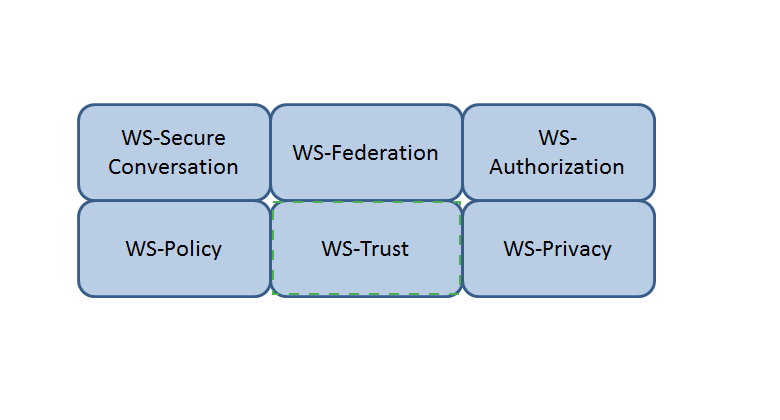
Explanation:
WS-Trust
WS-Trust is a Web Services Security (WS-Security) specification that negotiates how security tokens will be issued, renewed and validated. WS-Trust defines a framework for establishing trust relationships between different parties, and a protocol for requesting and issuing security tokens that can be used to authenticate and authorize the parties. WS-Trust also supports different types of security tokens, such as Kerberos tickets, X.509 certificates, SAML assertions, etc56 References: CISSP All-in-One Exam Guide, Eighth Edition, Chapter 6: Communication and Network Security, p. 346; Official (ISC)2 CISSP CBK Reference, Fifth Edition, Domain 4: Communication and Network Security, p. 465.



