CompTIA CNX-001 - CompTIA CloudNetX Exam
A network architect is designing a solution to place network core equipment in a rack inside a data center. This equipment is crucial to the enterprise and must be as secure as possible to minimize the chance that anyone could connect directly to the network core. The current security setup is:
In a locked building that requires sign in with a guard and identification check.
In a locked data center accessible by a proximity badge and fingerprint scanner.
In a locked cabinet that requires the security guard to call the Chief Information Security Officer (CISO) to get permission to provide the key.
Which of the following additional measures should the architect recommend to make this equipment more secure?
A call center company provides its services through a VoIP infrastructure. Recently, the call center set up an application to manage its documents on a cloud application. The application is causing recurring audio losses for VoIP callers. The network administrator needs to fix the issue with the least expensive solution. Which of the following is the best approach?
An architect needs to deploy a new payroll application on a cloud host. End users' access to the application will be based on the end users' role. In addition, the host must be deployed on the 192.168.77.32/30 subnet. Which of the following Zero Trust elements are being implemented in this design? (Choose two.)
A customer asks a MSP to propose a ZTA (Zero Trust Architecture) design for its globally distributed remote workforce. Given the following requirements:
Authentication should be provided through the customer's SAML identity provider.
Access should not be allowed from countries where the business does not operate.
Secondary authentication should be added to the workflow to allow for passkeys.
Changes to the user's device posture and hygiene should require reauthentication into the network.
Access to the network should only be allowed to originate from corporate-owned devices.
Which of the following solutions should the MSP recommend to meet the requirements?
A network administrator must connect a remote building at a manufacturing plant to the main building via a wireless connection. Which of the following should the administrator choose to get the greatest possible range from the wireless connection? (Choose two.)
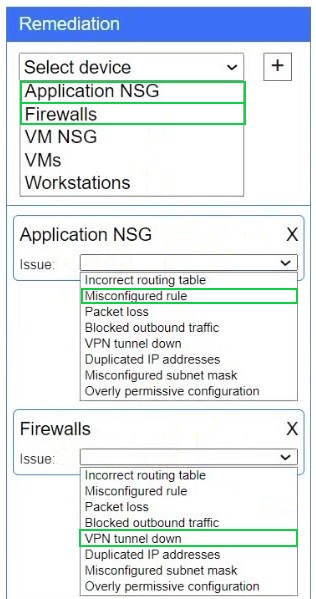
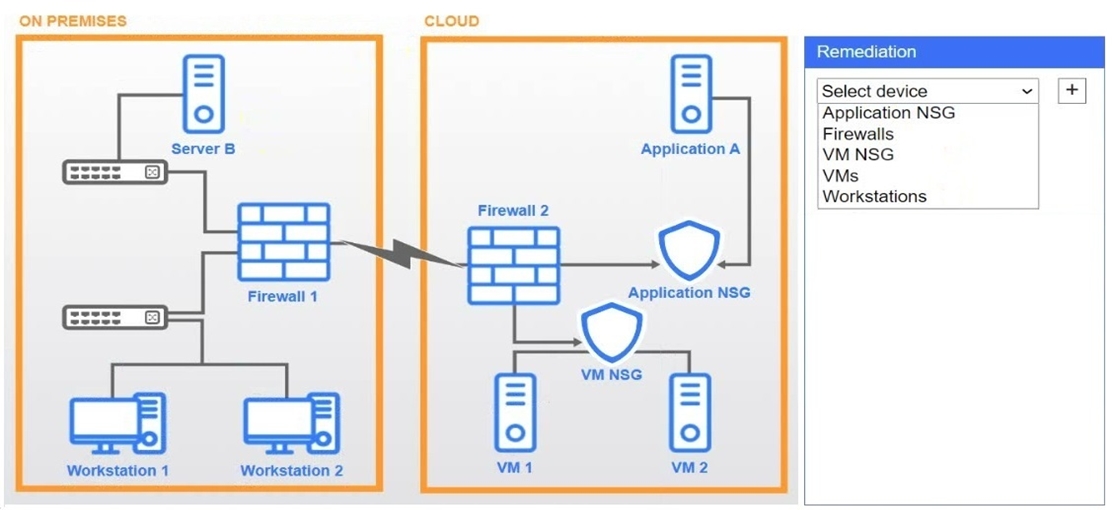
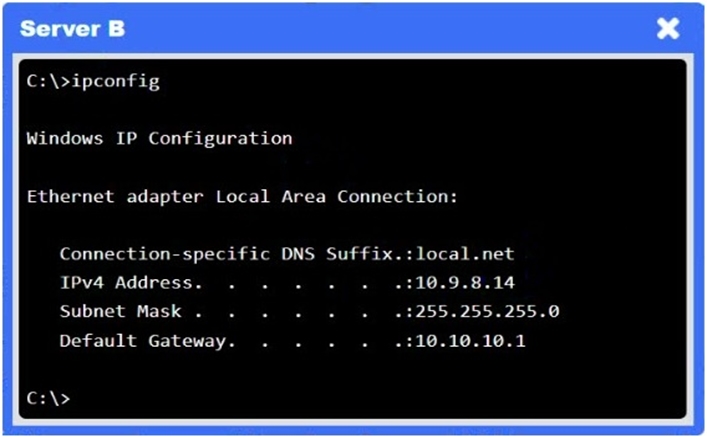
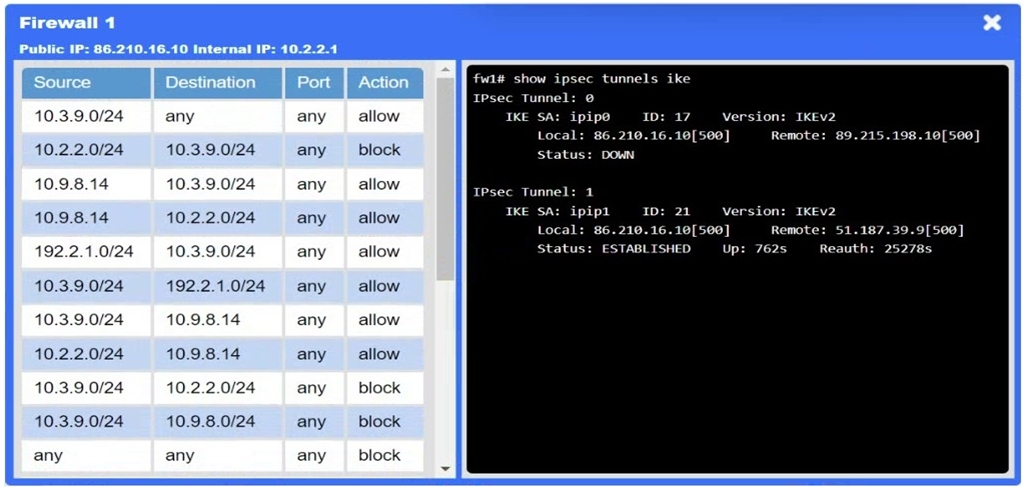
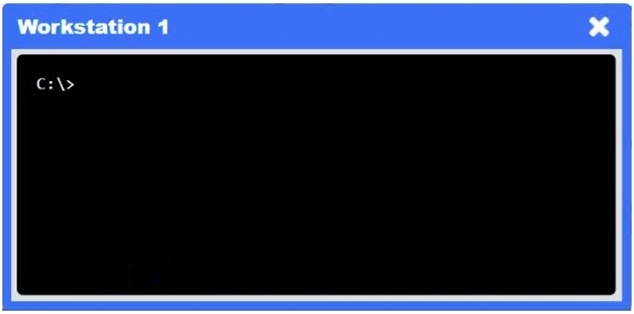
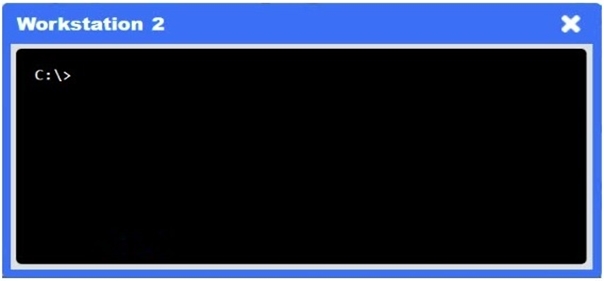
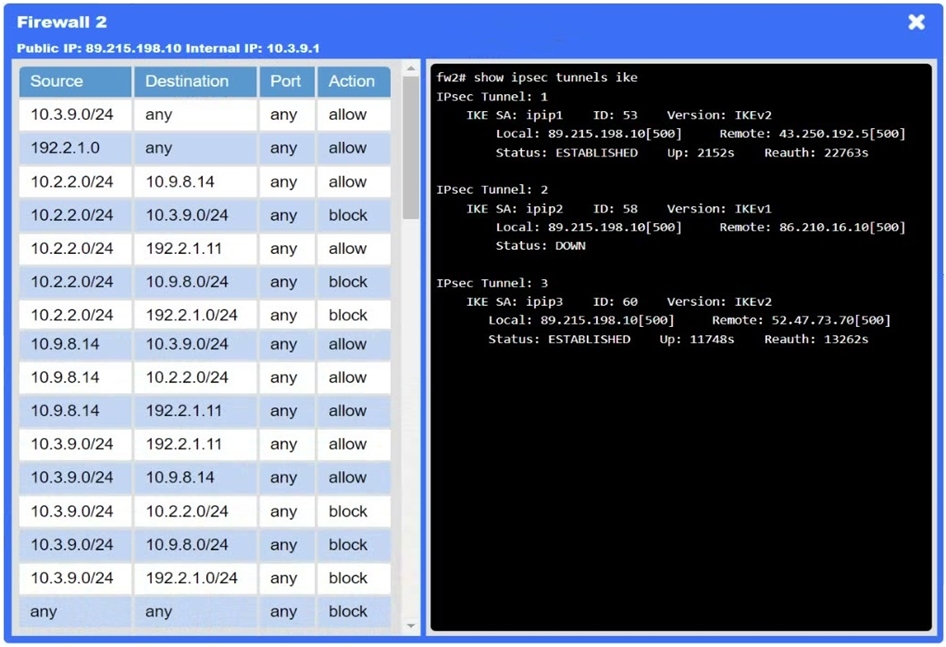
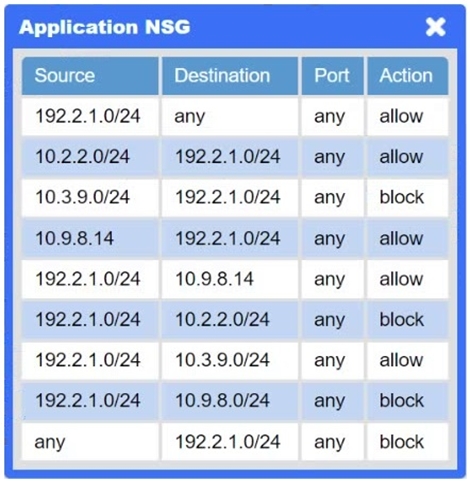
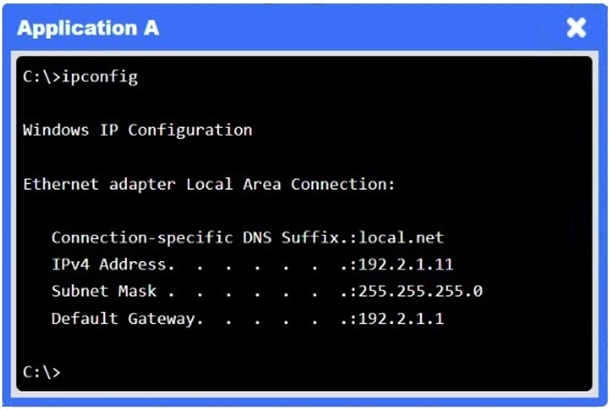
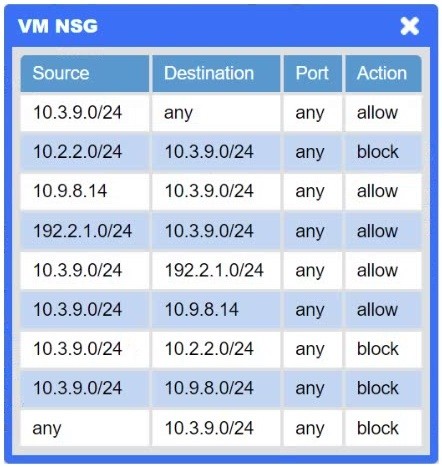
A network administrator needs to resolve connectivity issues in a hybrid cloud setup. Workstations and VMs are not able to access Application A. Workstations are able to access Server B.
INSTRUCTIONS
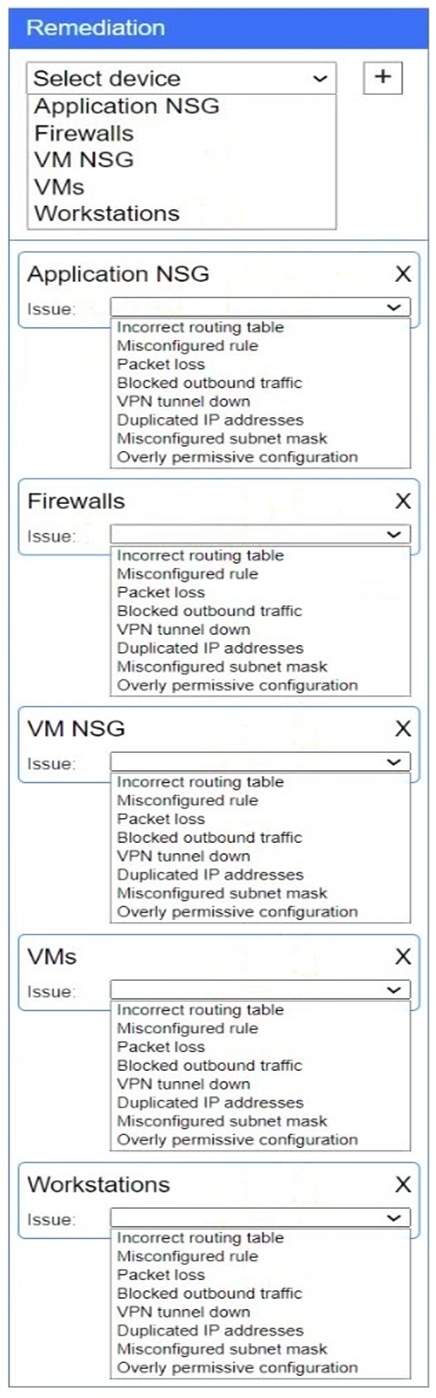
Click on workstations, VMs, firewalls, and NSGs to troubleshoot and gather information. Type help in the terminal to view a list of available commands.
Select the appropriate device(s) requiring remediation and identify the associated issue(s).
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.


A network architect is designing an expansion solution for the branch office network and requires the following business outcomes:
Maximize cost savings with reduced administration overhead
Easily expand connectivity to the cloud
Use cloud-based services to the branch offices
Which of the following should the architect do to best meet the requirements?
A network engineer adds a large group of servers to a screened subnet and configures them to use IPv6 only. The servers need to seamlessly communicate with IPv4 servers on the internal networks. Which of the following actions is the best way to achieve this goal?
A security architect needs to increase the security controls around computer hardware installations. The requirements are:
Auditable access logs to computer rooms
Alerts for unauthorized access attempts
Remote visibility to the inside of computer rooms
Which of the following controls best meet these requirements? (Choose two.)
A network architect needs to design a solution to ensure every cloud environment network is built to the same baseline. The solution must meet the following requirements:
Use automated deployment.
Easily update multiple environments.
Share code with a community of practice.
Which of the following are the best solutions? (Choose two.)