CompTIA CNX-001 - CompTIA CloudNetX Exam
Application development team users are having issues accessing the database server within the cloud environment. All other users are able to use SSH to access this server without issues. The network architect reviews the following information to troubleshoot the issue:
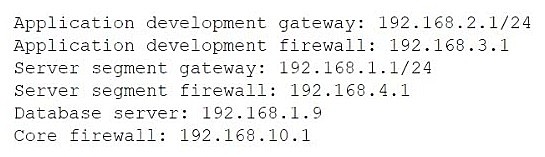
Traceroute output from an application developer's machine with the assigned IP 192.168.2.7:
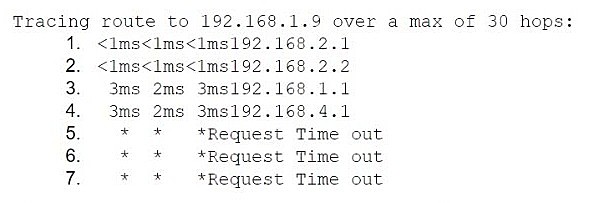
Application development gateway: 192.168.2.1/24
Server segment gateway: 192.168.1.1/24
Database server: 192.168.1.9
Application developer machine IP: 192.168.2.7
Traceroute ends at hop 4: 192.168.4.1 (server segment firewall), then times out
Which of the following is the most likely cause of the issue?
A company is expanding its network and needs to ensure improved stability and reliability. The proposed solution must fulfill the following requirements:
Detection and prevention of network loops
Automatic configuration of ports
Standard protocol (not proprietary)
Which of the following protocols is the most appropriate?
A developer reports errors when trying to access a web application. The developer uses Postman to troubleshoot and receives the following error:
HTTP Status: 403 Forbidden
Headers include authentication-related variables such as access_key, signature, salt, and timestamp
The request is a GET request to a payment methods API
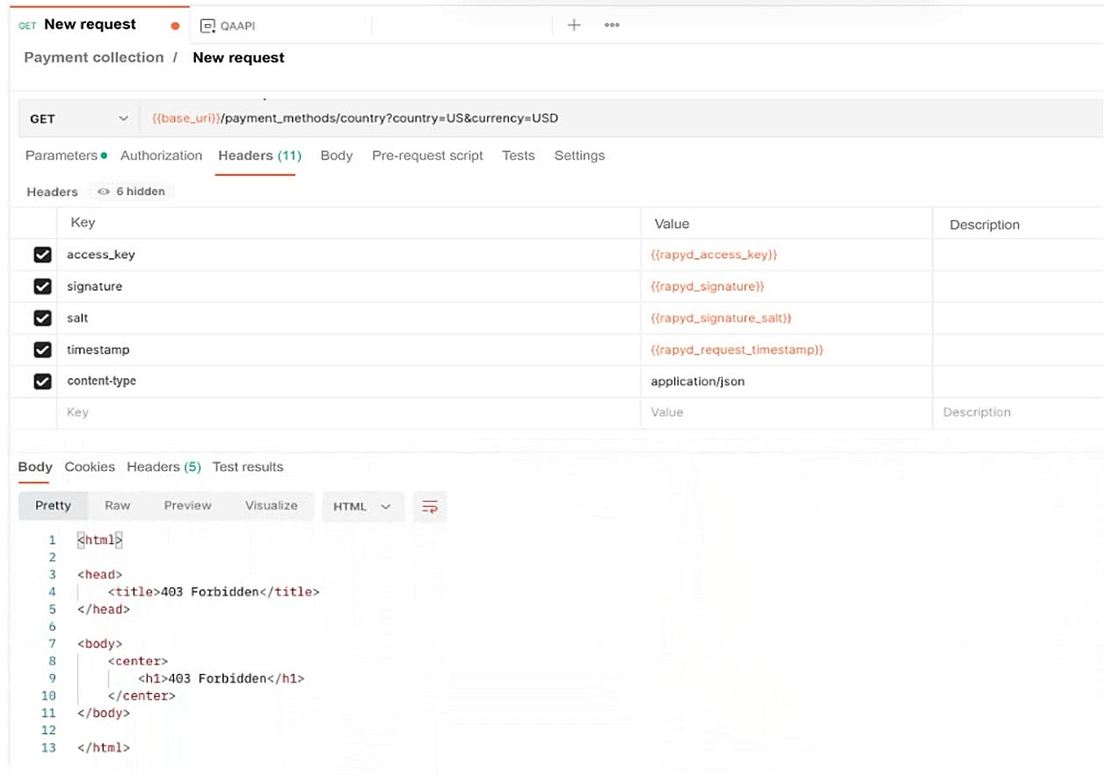
Which of the following is the cause of the issue?
A network engineer identified several failed log-in attempts to the VPN from a user's account. When the engineer inquired, the user mentioned the IT help desk called and asked them to change their password. Which of the following types of attacks occurred?
A SaaS company's new service currently is being provided through four servers. The company's end users are having connection issues, which is affecting about 25% of the connections. Which of the following is most likely the root cause of this issue?
A network architect is working on a physical network design template for a small education institution's satellite campus that is not yet built. The new campus location will consist of two small buildings with classrooms, one screening room with audiovisual equipment, and 200 seats for students. Which of the following enterprise network designs should the architect suggest?
A cloud network engineer needs to enable network flow analysis in the VPC so headers and payload of captured data can be inspected. Which of the following should the engineer use for this task?
A company is migrating an application to the cloud for modernization. The engineer needs to provide dependencies between application and database tiers in the environment. Which of the following should the engineer reference in order to best meet this requirement?
A network administrator is troubleshooting an outage at a remote site. The administrator examines the logs and determines that one of the internet links at the site appears to be down. After the service provider confirms this information, the administrator fails over traffic to the backup link. Which of the following should the administrator do next?
A network engineer is establishing a wireless network for handheld inventory scanners in a manufacturing company's warehouse. The engineer needs an authentication mechanism for these scanners that uses the Wi-Fi network and works with the company's Active Directory. The business requires that the solution authenticate the users and authorize the scanners. Which of the following provides the best solution for authentication and authorization?



