GAQM CPEH-001 - Certified Professional Ethical Hacker (CPEH)
In this attack, a victim receives an e-mail claiming from PayPal stating that their account has been disabled and confirmation is required before activation. The attackers then scam to collect not one but two credit card numbers, ATM PIN number and other personal details. Ignorant users usually fall prey to this scam.
Which of the following statement is incorrect related to this attack?
You are programming a buffer overflow exploit and you want to create a NOP sled of 200 bytes in the program exploit.c
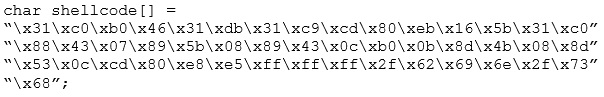
What is the hexadecimal value of NOP instruction?
You work for Acme Corporation as Sales Manager. The company has tight network security restrictions. You are trying to steal data from the company's Sales database (Sales.xls) and transfer them to your home computer. Your company filters and monitors traffic that leaves from the internal network to the Internet. How will you achieve this without raising suspicion?
What is a NULL scan?
What is the proper response for a NULL scan if the port is closed?
In the context of Windows Security, what is a 'null' user?
What ports should be blocked on the firewall to prevent NetBIOS traffic from not coming through the firewall if your network is comprised of Windows NT, 2000, and XP?
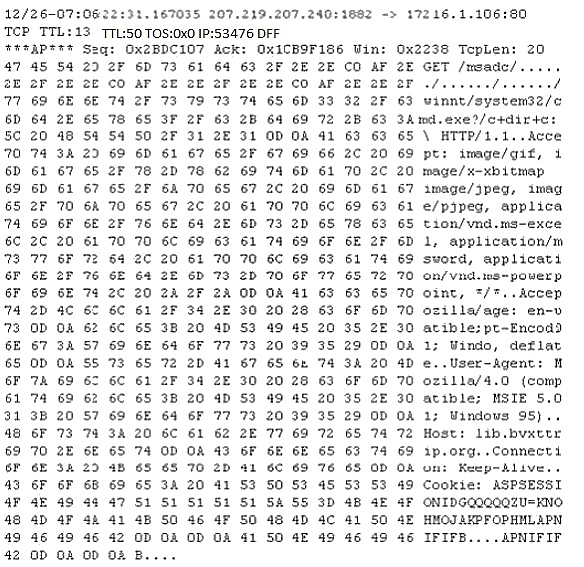
Study the following log extract and identify the attack.
Windows LAN Manager (LM) hashes are known to be weak.
Which of the following are known weaknesses of LM? (Choose three.)
_________ is a tool that can hide processes from the process list, can hide files, registry entries, and intercept keystrokes.
Which command can be used to show the current TCP/IP connections?
You have retrieved the raw hash values from a Windows 2000 Domain Controller. Using social engineering, you come to know that they are enforcing strong passwords. You understand that all users are required to use passwords that are at least 8 characters in length. All passwords must also use 3 of the 4 following categories: lower case letters, capital letters, numbers and special characters. With your existing knowledge of users, likely user account names and the possibility that they will choose the easiest passwords possible, what would be the fastest type of password cracking attack you can run against these hash values and still get results?
What hacking attack is challenge/response authentication used to prevent?
Which of the following algorithms can be used to guarantee the integrity of messages being sent, in transit, or stored?
Elliot is in the process of exploiting a web application that uses SQL as a back-end database. He’s determined that the application is vulnerable to SQL injection, and has introduced conditional timing delays into injected queries to determine whether they are successful. What type of SQL injection is Elliot most likely performing?



