GAQM CPEH-001 - Certified Professional Ethical Hacker (CPEH)
Using Windows CMD, how would an attacker list all the shares to which the current user context has access?
Which of the following statements is TRUE?
Jesse receives an email with an attachment labeled “Court_Notice_21206.zipâ€. Inside the zip file is a file named “Court_Notice_21206.docx.exe†disguised as a word document. Upon execution, a window appears stating, “This word document is corrupt.†In the background, the file copies itself to Jesse APPDATA\local directory and begins to beacon to a C2 server to download additional malicious binaries.
What type of malware has Jesse encountered?
This tool is an 802.11 WEP and WPA-PSK keys cracking program that can recover keys once enough data packets have been captured. It implements the standard FMS attack along with some optimizations like KoreK attacks, as well as the PTW attack, thus making the attack much faster compared to other WEP cracking tools.
Which of the following tools is being described?
Which of the following describes the characteristics of a Boot Sector Virus?
When you are collecting information to perform a data analysis, Google commands are very useful to find sensitive information and files. These files may contain information about passwords, system functions, or documentation.
What command will help you to search files using Google as a search engine?
A common cryptographical tool is the use of XOR. XOR the following binary values:
10110001
00111010
Which of the following is assured by the use of a hash?
How does the Address Resolution Protocol (ARP) work?
You've gained physical access to a Windows 2008 R2 server which has an accessible disc drive. When you attempt to boot the server and log in, you are unable to guess the password. In your tool kit you have an Ubuntu 9.10 Linux LiveCD. Which Linux based tool has the ability to change any user's password or to activate disabled Windows accounts?
You have compromised a server on a network and successfully opened a shell. You aimed to identify all operating systems running on the network. However, as you attempt to fingerprint all machines in the network using the nmap syntax below, it is not going through.
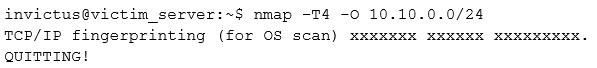
What seems to be wrong?
It is a kind of malware (malicious software) that criminals install on your computer so they can lock it from a remote location. This malware generates a pop-up window, webpage, or email warning from what looks like an official authority. It explains that your computer has been locked because of possible illegal activities on it and demands payment before you can access your files and programs again.
Which of the following terms best matches the definition?
Which of the following is the BEST way to defend against network sniffing?
Your team has won a contract to infiltrate an organization. The company wants to have the attack be as realistic as possible; therefore, they did not provide any information besides the company name.
What should be the first step in security testing the client?
It is an entity or event with the potential to adversely impact a system through unauthorized access, destruction, disclosure, denial of service or modification of data.
Which of the following terms best matches the definition?



