GAQM CPEH-001 - Certified Professional Ethical Hacker (CPEH)
A hacker searches in Google for filetype:pcf to find Cisco VPN config files. Those files may contain connectivity passwords that can be decoded with which of the following?
John the Ripper is a technical assessment tool used to test the weakness of which of the following?
While doing a Black box pen test via the TCP port (80), you noticed that the traffic gets blocked when you tried to pass IRC traffic from a web enabled host. However, you also noticed that outbound HTTP traffic is being allowed. What type of firewall is being utilized for the outbound traffic?
As an Ethical Hacker you are capturing traffic from your customer network with Wireshark and you need to find and verify just SMTP traffic. What command in Wireshark will help you to find this kind of traffic?
Why would an attacker want to perform a scan on port 137?
Shellshock had the potential for an unauthorized user to gain access to a server. It affected many internet-facing services, which OS did it not directly affect?
Which of the following tools is used by pen testers and analysts specifically to analyze links between data using link analysis and graphs?
Matthew received an email with an attachment named “YouWon$10Grand.zip.†The zip file contains a file named “HowToClaimYourPrize.docx.exe.†Out of excitement and curiosity, Matthew opened the said file. Without his knowledge, the file copies itself to Matthew’s APPDATA\IocaI directory and begins to beacon to a Command-and-control server to download additional malicious binaries. What type of malware has Matthew encountered?
The chance of a hard drive failure is known to be once every four years. The cost of a new hard drive is $500. EF (Exposure Factor) is about 0.5. Calculate for the Annualized Loss Expectancy (ALE).
Which among the following is a Windows command that a hacker can use to list all the shares to which the current user context has access?
Sandra is the security administrator of XYZ.com. One day she notices that the XYZ.com Oracle database server has been compromised and customer information along with financial data has been stolen. The financial loss will be estimated in millions of dollars if the database gets into the hands of competitors. Sandra wants to report this crime to the law enforcement agencies immediately. Which organization coordinates computer crime investigations throughout the United States?
Knowing the nature of backup tapes, which of the following is the MOST RECOMMENDED way of storing backup tapes?
While reviewing the result of scanning run against a target network you come across the following:
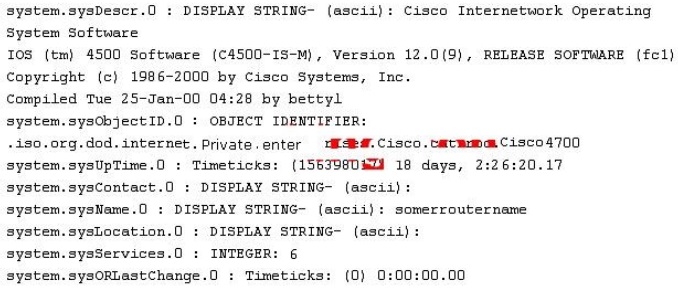
Which among the following can be used to get this output?
What kind of risk will remain even if all theoretically possible safety measures would be applied?
Which of the following is a vulnerability in GNU’s bash shell (discovered in September of 2014) that gives attackers access to run remote commands on a vulnerable system?



