GAQM CPEH-001 - Certified Professional Ethical Hacker (CPEH)
Suppose you’ve gained access to your client’s hybrid network. On which port should you listen to in order to know which Microsoft Windows workstations has its file sharing enabled?
A recent security audit revealed that there were indeed several occasions that the company’s network was breached. After investigating, you discover that your IDS is not configured properly and therefore is unable to trigger alarms when needed. What type of alert is the IDS giving?
While doing a technical assessment to determine network vulnerabilities, you used the TCP XMAS scan. What would be the response of all open ports?
Bob received this text message on his mobile phone: ““Hello, this is Scott Smelby from the Yahoo Bank. Kindly contact me for a vital transaction on: scottsmelby@yahoo.comâ€â€. Which statement below is true?
XOR is a common cryptographic tool. 10110001 XOR 00111010 is?
While performing ping scans into a target network you get a frantic call from the organization's security team. They report that they are under a denial of service attack. When you stop your scan, the smurf attack event stops showing up on the organization's IDS monitor.
How can you modify your scan to prevent triggering this event in the IDS?
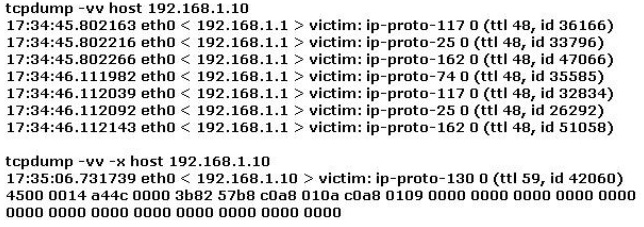
Study the log below and identify the scan type.
Defining rules, collaborating human workforce, creating a backup plan, and testing the plans are within what phase of the Incident Handling Process?
A hacker was able to easily gain access to a website. He was able to log in via the frontend user login form of the website using default or commonly used credentials. This exploitation is an example of what Software design flaw?
In order to prevent particular ports and applications from getting packets into an organization, what does a firewall check?
A server has been infected by a certain type of Trojan. The hacker intended to utilize it to send and host junk mails. What type of Trojan did the hacker use?
What is the term coined for logging, recording and resolving events in a company?
When security and confidentiality of data within the same LAN is of utmost priority, which IPSec mode should you implement?
A big company, who wanted to test their security infrastructure, wants to hire elite pen testers like you. During the interview, they asked you to show sample reports from previous penetration tests. What should you do?
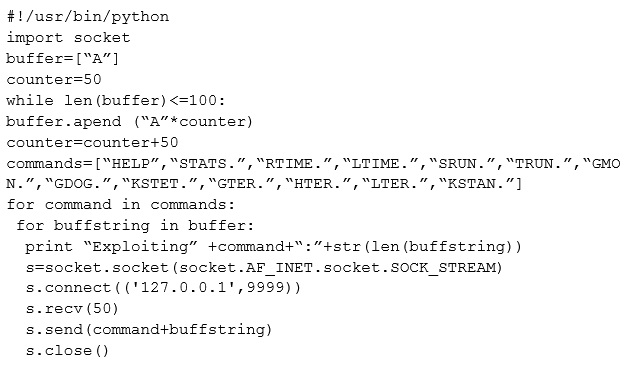
What is the code written for?