GAQM CPEH-001 - Certified Professional Ethical Hacker (CPEH)
Which Intrusion Detection System is best applicable for large environments where critical assets on the network need extra security and is ideal for observing sensitive network segments?
What does a firewall check to prevent particular ports and applications from getting packets into an organization?
Which of the following is a low-tech way of gaining unauthorized access to systems?
What is the role of test automation in security testing?
Cryptography is the practice and study of techniques for secure communication in the presence of third parties (called adversaries.) More generally, it is about constructing and analyzing protocols that overcome the influence of adversaries and that are related to various aspects in information security such as data confidentiality, data integrity, authentication, and non-repudiation. Modern cryptography intersects the disciplines of mathematics, computer science, and electrical engineering. Applications of cryptography include ATM cards, computer passwords, and electronic commerce.
Basic example to understand how cryptography works is given below:

Which of the following choices is true about cryptography?
The "gray box testing" methodology enforces what kind of restriction?
The company ABC recently contracted a new accountant. The accountant will be working with the financial statements. Those financial statements need to be approved by the CFO and then they will be sent to the accountant but the CFO is worried because he wants to be sure that the information sent to the accountant was not modified once he approved it. What of the following options can be useful to ensure the integrity of the data?
Which method of password cracking takes the most time and effort?
An attacker is using nmap to do a ping sweep and a port scanning in a subnet of 254 addresses.
In which order should he perform these steps?
What is not a PCI compliance recommendation?
What is the way to decide how a packet will move from an untrusted outside host to a protected inside that is behind a firewall, which permits the hacker to determine which ports are open and if the packets can pass through the packet-filtering of the firewall?
When purchasing a biometric system, one of the considerations that should be reviewed is the processing speed. Which of the following best describes what it is meant by processing?
By using a smart card and pin, you are using a two-factor authentication that satisfies
An IT employee got a call from one of our best customers. The caller wanted to know about the company's network infrastructure, systems, and team. New opportunities of integration are in sight for both company and customer. What should this employee do?
Eve stole a file named secret.txt, transferred it to her computer and she just entered these commands:
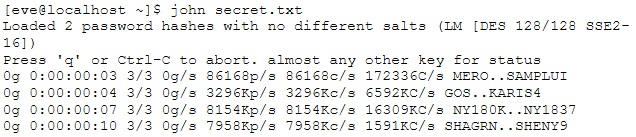
What is she trying to achieve?



