GAQM CPEH-001 - Certified Professional Ethical Hacker (CPEH)
If executives are found liable for not properly protecting their company's assets and information systems, what type of law would apply in this situation?
Scenario: 1. Victim opens the attacker’s web site.
2. Attacker sets up a web site which contains interesting and attractive content like 'Do you want to make S100 In a day?',
3. Victim clicks to the interesting and attractive content url.
4- Attacker creates a transparent iframe' in front of the url which victim attempt to click, so victim thinks that he/she clicks to the 'Do you want to make $1000 in a day?' url but actually he/sne clicks to the content or url that exists in the transparent iframe' which is setup by the attacker.
What is the name of the attack which is mentioned in the scenario?
PGP, SSL, and IKE are all examples of which type of cryptography?
An Internet Service Provider (ISP) has a need to authenticate users connecting using analog modems, Digital Subscriber Lines (DSL), wireless data services, and Virtual Private Networks (VPN) over a Frame Relay network.
Which AAA protocol is most likely able to handle this requirement?
The network in ABC company is using the network address 192.168.1.64 with mask 255.255.255.192. In the network the servers are in the addresses 192.168.1.122, 192.168.1.123 and 192.168.1.124.
An attacker is trying to find those servers but he cannot see them in his scanning. The command he is using is:
nmap 192.168.1.64/28.
Why he cannot see the servers?
What is the difference between the AES and RSA algorithms?
If you want only to scan fewer ports than the default scan using Nmap tool, which option would you use?
The network team has well-established procedures to follow for creating new rules on the firewall. This includes having approval from a manager prior to implementing any new rules. While reviewing the firewall configuration, you notice a recently implemented rule but cannot locate manager approval for it. What would be a good step to have in the procedures for a situation like this?
In which of the following cryptography attack methods, the attacker makes a series of interactive queries, choosing subsequent plaintexts based on the information from the previous encryptions?
Which of the following is an adaptive SQL Injection testing technique used to discover coding errors by inputting massive amounts of random data and observing the changes in the output?
In the field of cryptanalysis, what is meant by a “rubber-hose" attack?
The Payment Card Industry Data Security Standard (PCI DSS) contains six different categories of control objectives. Each objective contains one or more requirements, which must be followed in order to achieve compliance. Which of the following requirements would best fit under the objective, "Implement strong access control measures"?
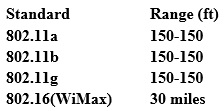
From the following table, identify the wrong answer in terms of Range (ft).
Which protocol is used for setting up secure channels between two devices, typically in VPNs?
Which of the following attacks exploits web age vulnerabilities that allow an attacker to force an unsuspecting user’s browser to send malicious requests they did not intend?



