GAQM CPEH-001 - Certified Professional Ethical Hacker (CPEH)
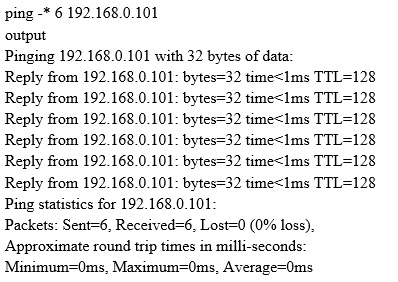
What does the option * indicate?
An unauthorized individual enters a building following an employee through the employee entrance after the lunch rush. What type of breach has the individual just performed?
What is the purpose of a demilitarized zone on a network?
What network security concept requires multiple layers of security controls to be placed throughout an IT infrastructure, which improves the security posture of an organization to defend against malicious attacks or potential vulnerabilities?
What kind of Web application vulnerability likely exists in their software?
A company's policy requires employees to perform file transfers using protocols which encrypt traffic. You suspect some employees are still performing file transfers using unencrypted protocols because the employees do not like changes. You have positioned a network sniffer to capture traffic from the laptops used by employees in the data ingest department. Using Wire shark to examine the captured traffic, which command can be used as a display filter to find unencrypted file transfers?
Steve, a scientist who works in a governmental security agency, developed a technological solution to identify people based on walking patterns and implemented this approach to a physical control access.
A camera captures people walking and identifies the individuals using Steve’s approach.
After that, people must approximate their RFID badges. Both the identifications are required to open the door.
In this case, we can say:
Which of the following is the best countermeasure to encrypting ransomwares?
You need to deploy a new web-based software package for your organization. The package requires three separate servers and needs to be available on the Internet. What is the recommended architecture in terms of server placement?
A hacker named Jack is trying to compromise a bank’s computer system. He needs to know the operating system of that computer to launch further attacks.
What process would help him?
In which of the following password protection technique, random strings of characters are added to the password before calculating their hashes?
Cross-site request forgery involves:
You need a tool that can do network intrusion prevention and intrusion detection, function as a network sniffer, and record network activity, what tool would you most likely select?
Which of the following Bluetooth hacking techniques does an attacker use to send messages to users without the recipient’s consent, similar to email spamming?
An attacker scans a host with the below command. Which three flags are set? (Choose three.)
#nmap –sX host.domain.com
What type of vulnerability/attack is it when the malicious person forces the user’s browser to send an authenticated request to a server?



