Isaca CRISC - Certified in Risk and Information Systems Control
Which of the following will BEST help to ensure the continued effectiveness of the IT risk management function within an organization experiencing high employee turnover?
Which of the following is the BEST control to detect an advanced persistent threat (APT)?
A software developer has administrative access to a production application. Which of the following should be of GREATEST concern to a risk practitioner?
Which of the following is the PRIMARY factor in determining a recovery time objective (RTO)?
Which of the following is the PRIMARY objective of risk management?
After mapping generic risk scenarios to organizational security policies, the NEXT course of action should be to:
Which of the following will BEST support management reporting on risk?
Which of the following is MOST important to the successful development of IT risk scenarios?
Which of the following is the PRIMARY reason to ensure policies and standards are properly documented within the risk management process?
Which of the following BEST reduces the probability of laptop theft?
A company has located its computer center on a moderate earthquake fault. Which of the following is the MOST important consideration when establishing a contingency plan and an alternate processing site?
Which of the following changes would be reflected in an organization's risk profile after the failure of a critical patch implementation?
An organization has outsourced its backup and recovery procedures to a third-party cloud provider. Which of the following is the risk practitioner s BEST course of action?
Which of the following is the BEST indication that an organization's risk management program has not reached the desired maturity level?
Which of the following is MOST important to ensure when reviewing an organization's risk register?
Which of the following resources is MOST helpful to a risk practitioner when updating the likelihood rating in the risk register?
it was determined that replication of a critical database used by two business units failed. Which of the following should be of GREATEST concern1?
Which of the blowing is MOST important when implementing an organization s security policy?
The risk associated with inadvertent disclosure of database records from a public cloud service provider (CSP) would MOST effectively be reduced by:
Which of the following is the FIRST step in managing the risk associated with the leakage of confidential data?
Which of the following should be the FIRST step when a company is made aware of new regulatory requirements impacting IT?
Which of the following BEST protects an organization against breaches when using a software as a service (SaaS) application?
A risk practitioner discovers that an IT operations team manager bypassed web filtering controls by using a mobile device, in violation of the network security policy. Which of the following should the risk practitioner do FIRST?
Which of the following should a risk practitioner do NEXT after learning that Internet of Things (loT) devices installed in the production environment lack appropriate security controls for
sensitive data?
The BEST way for management to validate whether risk response activities have been completed is to review:
Which process is MOST effective to determine relevance of threats for risk scenarios?
The head of a business operations department asks to review the entire IT risk register. Which of the following would be the risk manager s BEST approach to this request before sharing the register?
An organization has committed to a business initiative with the knowledge that the risk exposure is higher than the risk appetite. Which of the following is the risk practitioner's MOST important action related to this decision?
The following is the snapshot of a recently approved IT risk register maintained by an organization's information security department.
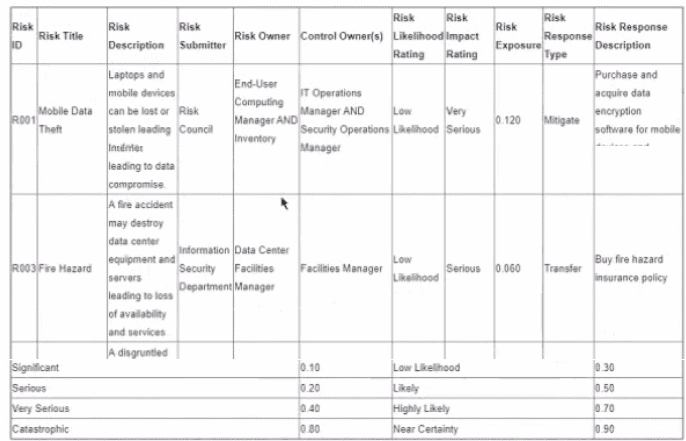
After implementing countermeasures listed in ‘’Risk Response Descriptions’’ for each of the Risk IDs, which of the following component of the register MUST change?
Which of the following can be used to assign a monetary value to risk?
Which of the following is the PRIMARY role of the board of directors in corporate risk governance?
What is MOST important for the risk practitioner to understand when creating an initial IT risk register?
Key control indicators (KCls) help to assess the effectiveness of the internal control environment PRIMARILY by:
Which of the following is the MOST effective way to validate organizational awareness of cybersecurity risk?
When reviewing a business continuity plan (BCP). which of the following would be the MOST significant deficiency?
A chief information officer (CIO) has identified risk associated with shadow systems being maintained by business units to address specific functionality gaps in the organization'senterprise resource planning (ERP) system. What is the BEST way to reduce this risk going forward?
Which of the following statements describes the relationship between key risk indicators (KRIs) and key control indicators (KCIs)?
Warning banners on login screens for laptops provided by an organization to its employees are an example of which type of control?
Which of the following is the BEST recommendation of a risk practitioner for an organization that recently changed its organizational structure?
Which of the following is the MAIN benefit to an organization using key risk indicators (KRIs)?
A multinational company needs to implement a new centralized security system. The risk practitioner has identified a conflict between the organization's data-handling policy and local privacy regulations. Which of the following would be the BEST recommendation?
When preparing a risk status report for periodic review by senior management, it is MOST important to ensure the report includes
Accountability for a particular risk is BEST represented in a:
Who is MOST important lo include in the assessment of existing IT risk scenarios?
Which of the following metrics is BEST used to communicate to senior management that the control environment manages risk within appetite and tolerance?
Which of the following is the BEST way to protect sensitive data from administrators within a public cloud?
A risk practitioner has learned that an effort to implement a risk mitigation action plan has stalled due to lack of funding. The risk practitioner should report that the associated risk has been:
After entering a large number of low-risk scenarios into the risk register, it is MOST important for the risk practitioner to:
Who is the MOST appropriate owner for newly identified IT risk?
The BEST way to determine the likelihood of a system availability risk scenario is by assessing the:



