CompTIA CS0-002 - CompTIA CySA+ Certification Exam (CS0-002)
A Chief Executive Officer (CEO) is concerned the company will be exposed to data sovereignty issues as a result of some new privacy regulations to help mitigate this risk. The Chief Information Security Officer (CISO) wants to implement an appropriate technical control. Which of the following would meet the requirement?
A company's security team recently discovered a number of workstations that are at the end of life. The workstation vendor informs the team that the product is no longer supported and patches are no longer available The company is not prepared to cease its use of these workstations Which of the following would be the BEST method to protect these workstations from threats?
A security analyst responds to a series of events surrounding sporadic bandwidth consumption from an endpoint device. The security analyst then identifies the following additional details:
• Bursts of network utilization occur approximately every seven days.
• The content being transferred appears to be encrypted or obfuscated.
• A separate but persistent outbound TCP connection from the host to infrastructure in a third-party cloud is in place.
• The HDD utilization on the device grows by 10GB to 12GB over the course of every seven days.
• Single file sizes are 10GB.
Which of the following describes the most likely cause of the issue?
Wncn ol the following provides an automated approach 10 checking a system configuration?
Which of the following attack techniques has the GREATEST likelihood of quick success against Modbus assets?
A security engineer is reviewing security products that identify malicious actions by users as part of a company's insider threat program. Which of the following is the most appropriate product category for this purpose?
A company's legal and accounting teams have decided it would be more cost-effective to offload the risks of data storage to a third party. The IT management team has decided to implement a cloud model and has asked the security team for recommendations. Which of the following will allow all data to be kept on the third-party network?
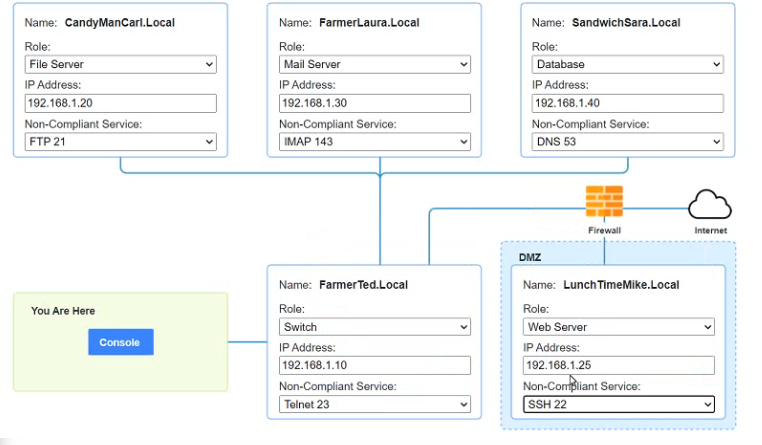
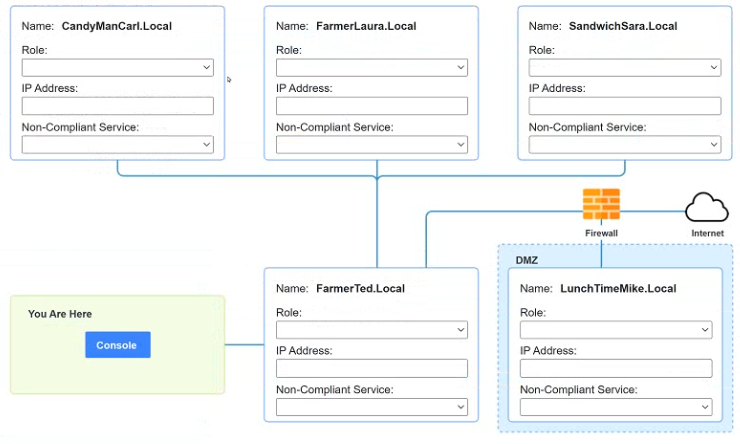
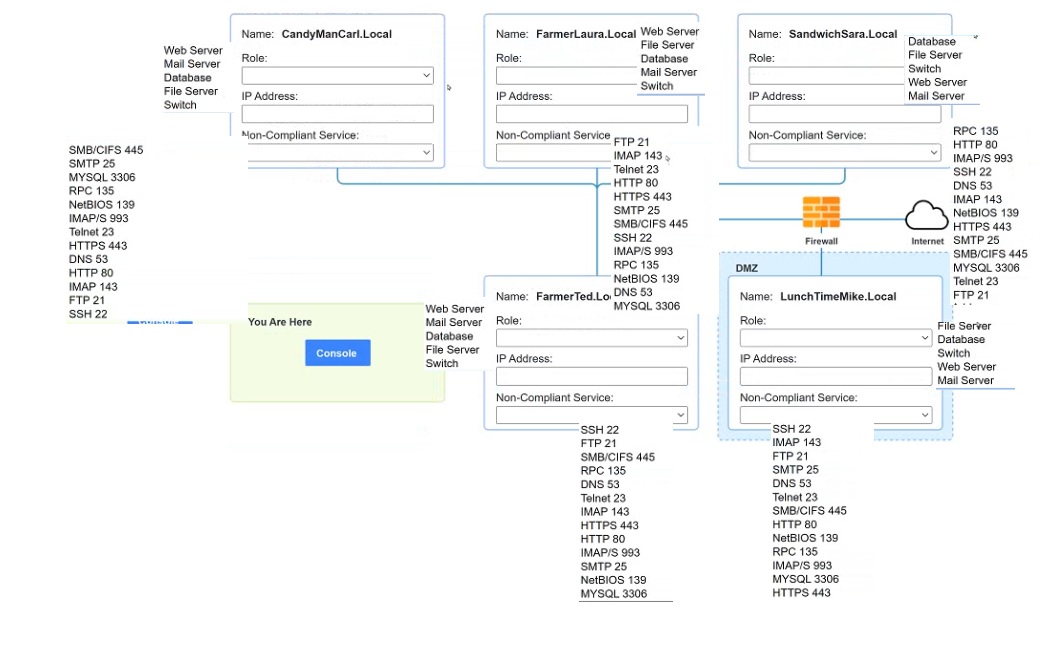
You are a penetration tester who is reviewing the system hardening guidelines for a company. Hardening guidelines indicate the following.
There must be one primary server or service per device.
Only default port should be used
Non- secure protocols should be disabled.
The corporate internet presence should be placed in a protected subnet
Instructions :
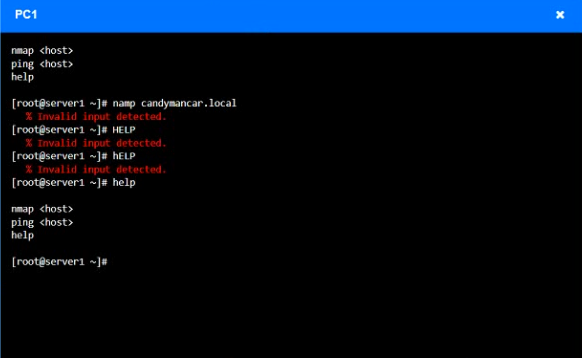
Using the available tools, discover devices on the corporate network and the services running on these devices.
You must determine
ip address of each device
The primary server or service each device
The protocols that should be disabled based on the hardening guidelines
An analyst is reviewing email headers to determine if an email has been sent from a legitimate sender. The organization uses SPF to validate email origination. Which of the following most likely indicates an invalid originator?
A digital forensics investigator works from duplicate images to preserve the integrity of the original evidence. Which of the following types of media are most volatile and should be preserved? (Select two).