CompTIA CS0-002 - CompTIA CySA+ Certification Exam (CS0-002)
A company is building a new internal network. Instead of creating new credentials, the company wants to streamline each employee's authentication. Which of the following technologies would best fulfill this requirement?
In response to an audit finding, a company's Chief information Officer (CIO) instructed the security department to Increase the security posture of the vulnerability management program. Currency, the company's vulnerability management program has the following attributes:
Which of the following would BEST Increase the security posture of the vulnerably management program?
A security manager has asked an analyst to provide feedback on the results of a penetration test. After reviewing the results, the manager requests
information regarding the possible exploitation of vulnerabilities. Which of the following information data points would be MOST useful for the analyst
to provide to the security manager, who would then communicate the risk factors to the senior management team? (Select TWO).
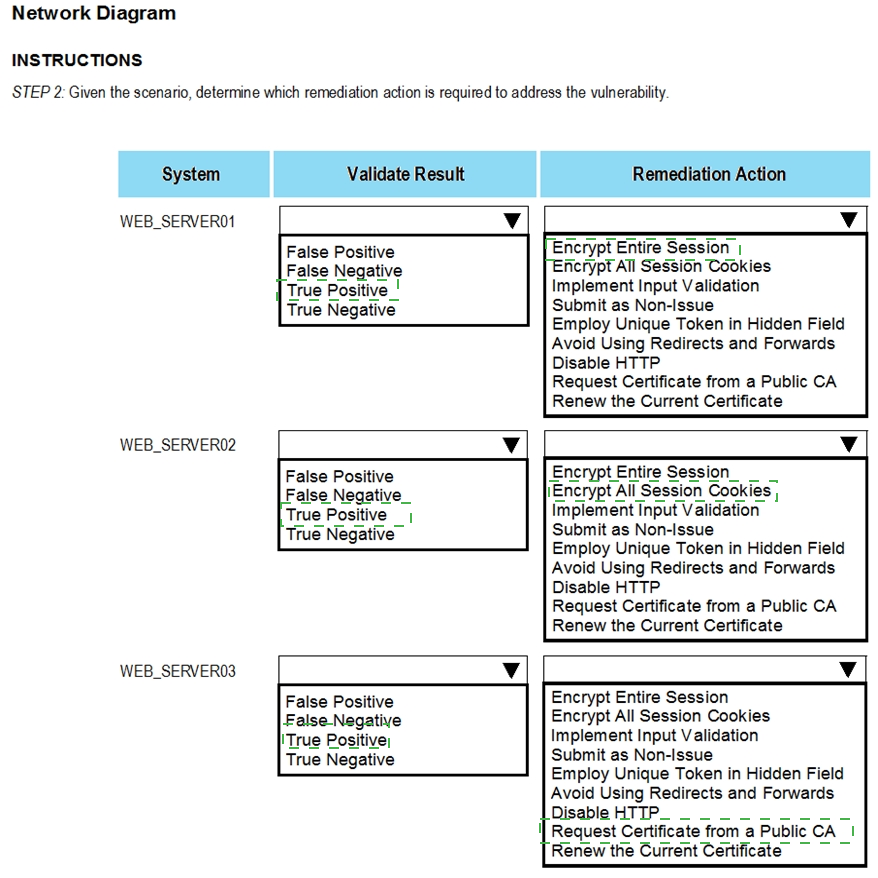
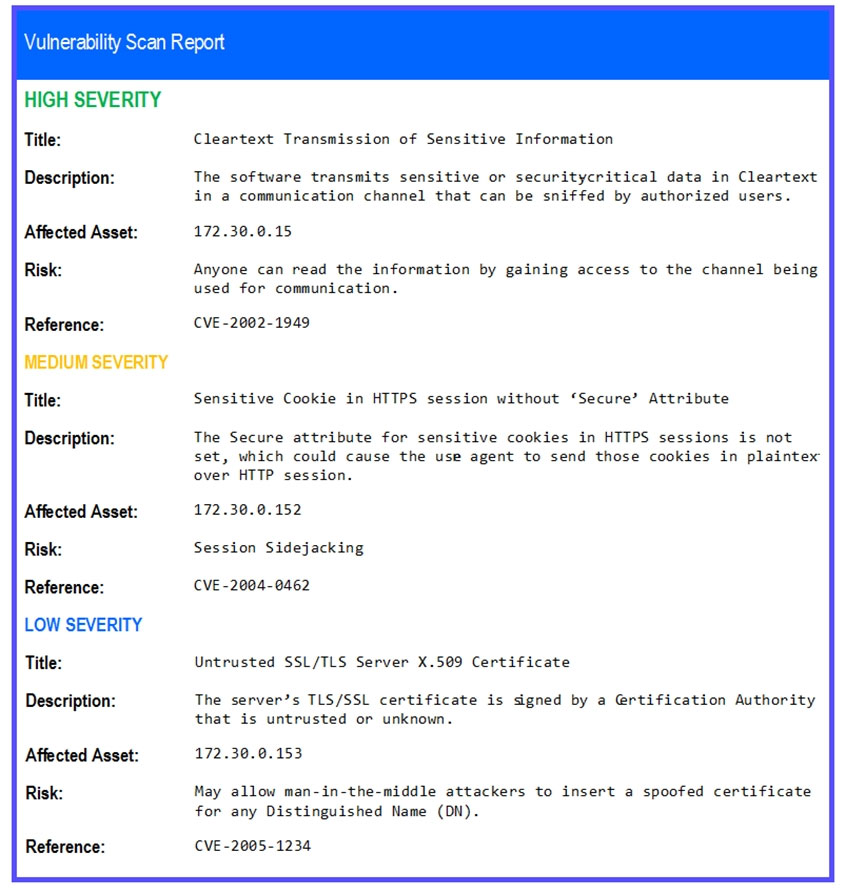
The developers recently deployed new code to three web servers. A daffy automated external device scan report shows server vulnerabilities that are failure items according to PCI DSS.
If the venerability is not valid, the analyst must take the proper steps to get the scan clean.
If the venerability is valid, the analyst must remediate the finding.
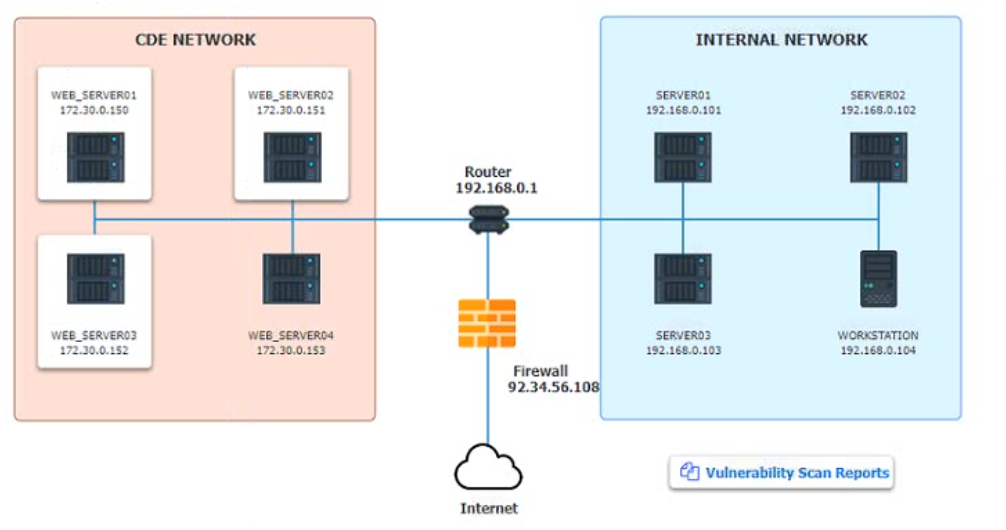
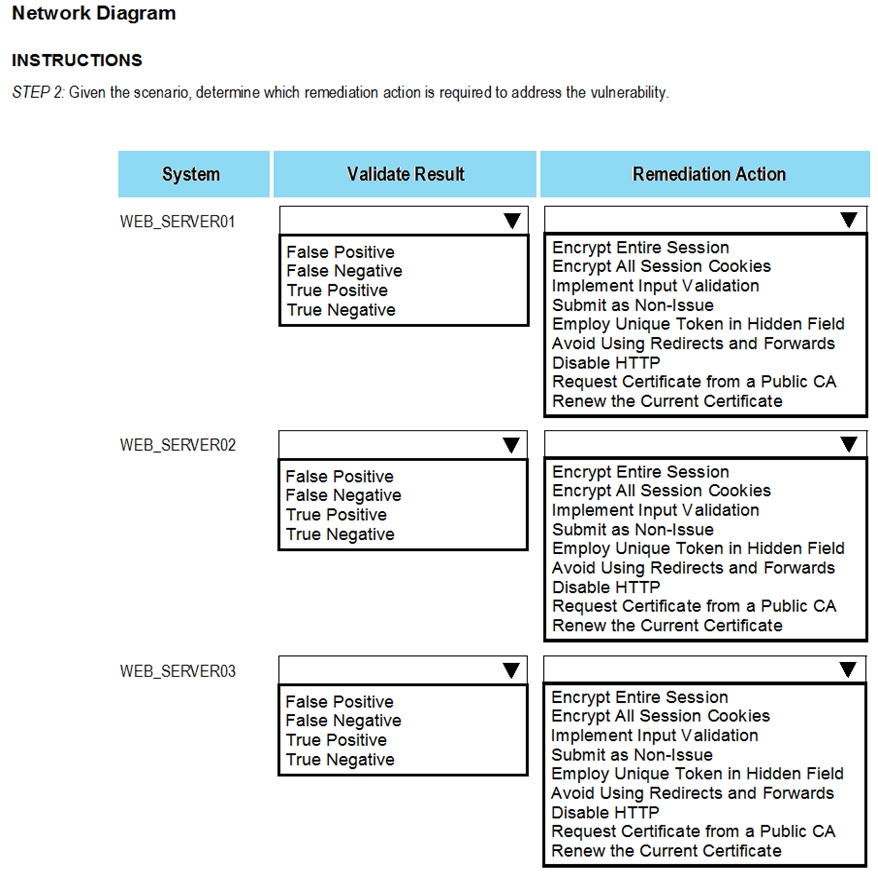
After reviewing the information provided in the network diagram, select the STEP 2 tab to complete the simulation by selecting the correct Validation Result and Remediation Action for each server listed using the drop-down options.
INTRUCTIONS:
The simulation includes 2 steps.
Step1:Review the information provided in the network diagram and then move to the STEP 2 tab.
STEP 2: Given the Scenario, determine which remediation action is required to address the vulnerability.
A vulnerability assessment solution is hosted in the cloud This solution will be used as an accurate inventory data source for both the configuration management database and the governance nsk and compliance tool An analyst has been asked to automate the data acquisition Which of the following would be the BEST way to acqutre the data'
A security analyst is reviewing the following server statistics:
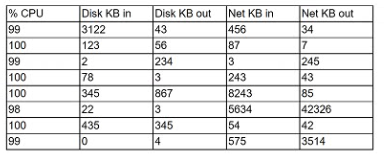
Which of the following Is MOST likely occurring?
A Chief Executive Officer (CEO) is concerned about the company’s intellectual property being leaked to competitors. The security team performed an extensive review but did not find any indication of an outside breach. The data sets are currently encrypted using the Triple Data Encryption Algorithm. Which of the following courses of action is appropriate?
The following output is from a tcpdump al the edge of the corporate network:
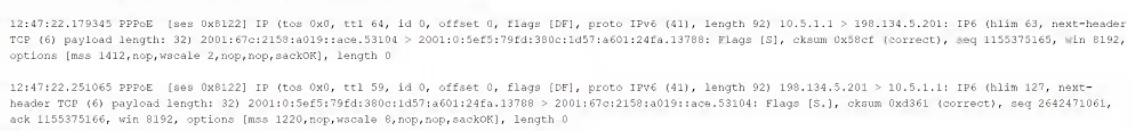
Which of the following best describes the potential security concern?
During a review of SIEM alerts, a securrty analyst discovers the SIEM is receiving many alerts per day from the file-integrity monitoring toot about files from a newly deployed application that should not change. Which of the following steps should the analyst complete FIRST to respond to the issue7
A code review reveals a web application is using lime-based cookies for session management. This is a security concern because lime-based cookies are easy to: