CompTIA CS0-002 - CompTIA CySA+ Certification Exam (CS0-002)
A security learn implemented a SCM as part for its security-monitoring program there is a requirement to integrate a number of sources Into the SIEM to provide better context relative to the events being processed. Which of the following B€ST describes the result the security learn hopes to accomplish by adding these sources?
In web application scanning, static analysis refers to scanning:
A security officer needs to find the most cost-effective solution to the current data privacy and protection gap found in the last security assessment Which of the following is the BEST recommendation?
An organization is focused on restructuring its data governance programs and an analyst has been Tasked with surveying sensitive data within the organization. Which of the following is the MOST accurate method for the security analyst to complete this assignment?
A Chief Information Officer wants to implement a BYOD strategy for all company laptops and mobile phones. The Chief Information Security Officer is concerned with ensuring all devices are patched and running some sort of protection against malicious software. Which of the following existing technical controls should a security analyst recommend to best meet all the requirements?
A cybersecurity analyst is supporting an Incident response effort via threat Intelligence Which of the following is the analyst most likely executing?
Which of the following is a vulnerability associated with the Modbus protocol?
A security analyst is reviewing WAF alerts and sees the following request:

Which of the following BEST describes the attack?
An organization has the following vulnerability remediation policies:
• For production environment servers:
• Vulnerabilities with a CVSS score of 9.0 or greater must be remediated within 48 hours.
• Vulnerabilities with a CVSS score of 5.0 to 8.9 must be remediated within 96 hours.
• Vulnerabilities in lower environments may be left unremediated for up to two weeks.
* All vulnerability remediations must be validated in a testing environment before they are applied in the production environment.
The organization has two environments: production and testing. The accountingProd server is the only server that contains highly sensitive information.
A recent vulnerability scan provided the following report:
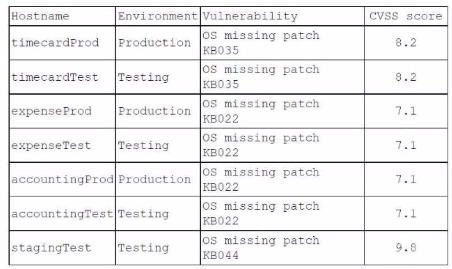
Which of the following identifies the server that should be patched first? (Choose Two)
Which of the following BEST explains the function of trusted firmware updates as they relate to hardware assurance?



