CompTIA CS0-002 - CompTIA CySA+ Certification Exam (CS0-002)
An organization supports a large number of remote users. Which of the following is the best option to protect the data on the remote users' laptops?
Which of the following organizational initiatives would be MOST impacted by data severighty issues?
During routine monitoring a security analyst identified the following enterpnse network traffic:
Packet capture output:
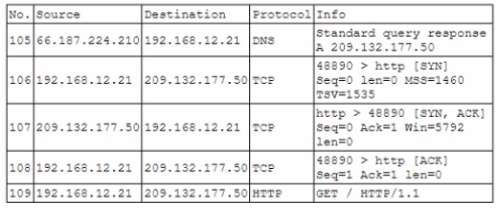
Which of the following BEST describes what the security analyst observed?
In SIEM software, a security analysis selected some changes to hash signatures from monitored files during the night followed by SMB brute-force attacks against the file servers Based on this behavior, which of the following actions should be taken FIRST to prevent a more serious compromise?
Which of the following is an advantage of SOAR over SIEM?
The incident response team is working with a third-party forensic specialist to investigate the root cause of a recent intrusion An analyst was asked to submit sensitive network design details for review The forensic specialist recommended electronic delivery for efficiency but email was not an approved communication channel to send network details Which of the following BEST explains the importance of using a secure method of communication during incident response?
A security operations manager wants some recommendations for improving security monitoring. The security team currently uses past events to create an IOC list for monitoring.
Which of the following is the best suggestion for improving monitoring capabilities?
A security analyst implemented a solution that would analyze the attacks that the organization's firewalls failed to prevent. The analyst used the existing systems to enact the solution and executed the following command:
$ sudo nc —1 —v —e maildaemon.py 25 > caplog.txt
Which of the following solutions did the analyst implement?
A product security analyst has been assigned to evaluate and validate a new products security capabilities Part of the evaluation involves reviewing design changes at specific intervals tor security deficiencies recommending changes and checking for changes at the next checkpoint Which of the following BEST defines the activity being conducted?
Which of the following is the most effective approach to minimize the occurrence of vulnerabilities introduced by unintentional misconfigurations in the cloud?



