CompTIA CS0-003 - CompTIA CyberSecurity Analyst CySA+ Certification Exam
A security analyst is reviewing the following alert that was triggered by FIM on a critical system:
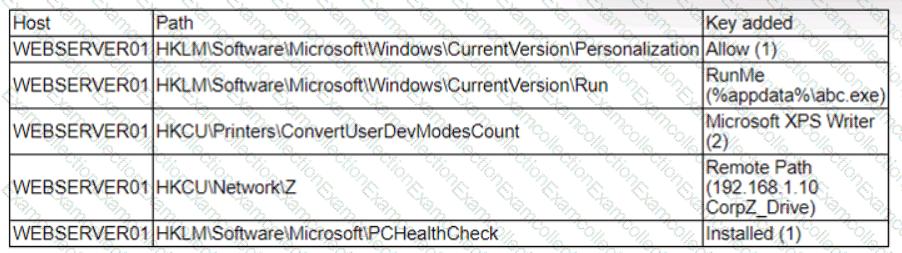
Which of the following best describes the suspicious activity that is occurring?
A security analyst observed the following activity from a privileged account:
. Accessing emails and sensitive information
. Audit logs being modified
. Abnormal log-in times
Which of the following best describes the observed activity?
Which of the following characteristics ensures the security of an automated information system is the most effective and economical?
A SOC receives several alerts indicating user accounts are connecting to the company’s identity provider through non-secure communications. User credentials for accessing sensitive, business-critical systems could be exposed. Which of the following logs should the SOC use when determining malicious intent?
A user downloads software that contains malware onto a computer that eventually infects numerous other systems. Which of the following has the user become?
Several incidents have occurred with a legacy web application that has had little development work completed. Which of the following is the most likely cause of the incidents?
A security analyst has prepared a vulnerability scan that contains all of the company's functional subnets. During the initial scan, users reported that network printers began to print pages that contained unreadable text and icons.
Which of the following should the analyst do to ensure this behavior does not oocur during subsequent vulnerability scans?
A company receives a penetration test report summary from a third party. The report summary indicates a proxy has some patches that need to be applied. The proxy is sitting in a rack and is not being
used, as the company has replaced it with a new one. The CVE score of the vulnerability on the proxy is a 9.8. Which of the following best practices should the company follow with this proxy?
A security analyst is reviewing a packet capture in Wireshark that contains an FTP session from a potentially compromised machine. The analyst sets the following display filter: ftp. The analyst can see there are several RETR requests with 226 Transfer complete responses, but the packet list pane is not showing the packets containing the file transfer itself. Which of the following can the analyst perform to see the entire contents of the downloaded files?
An analyst investigated a website and produced the following:
Starting Nmap 7.92 ( https://nmap.org ) at 2022-07-21 10:21 CDT
Nmap scan report for insecure.org (45.33.49.119)
Host is up (0.054s latency).
rDNS record for 45.33.49.119: ack.nmap.org
Not shown: 95 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
25/tcp closed smtp
80/tcp open http Apache httpd 2.4.6
113/tcp closed ident
443/tcp open ssl/http Apache httpd 2.4.6
Service Info: Host: issues.nmap.org
Service detection performed. Please report any incorrect results at https://nmap .org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 20.52 seconds
Which of the following syntaxes did the analyst use to discover the application versions on this vulnerable website?



