CompTIA CS0-003 - CompTIA CyberSecurity Analyst CySA+ Certification Exam
An incident response team is assessing attack vectors of malware that is encrypting data with ransomware. There are no indications of a network-based intrusion.
Which of the following is the most likely root cause of the incident?
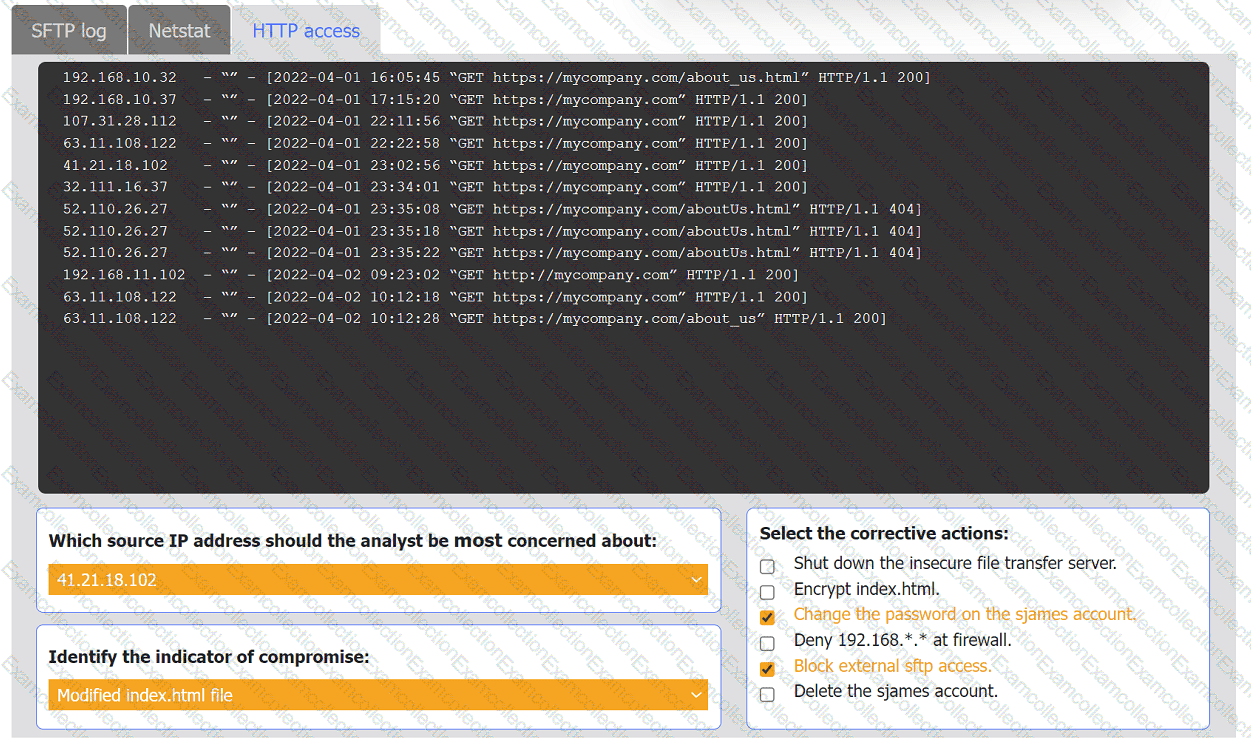
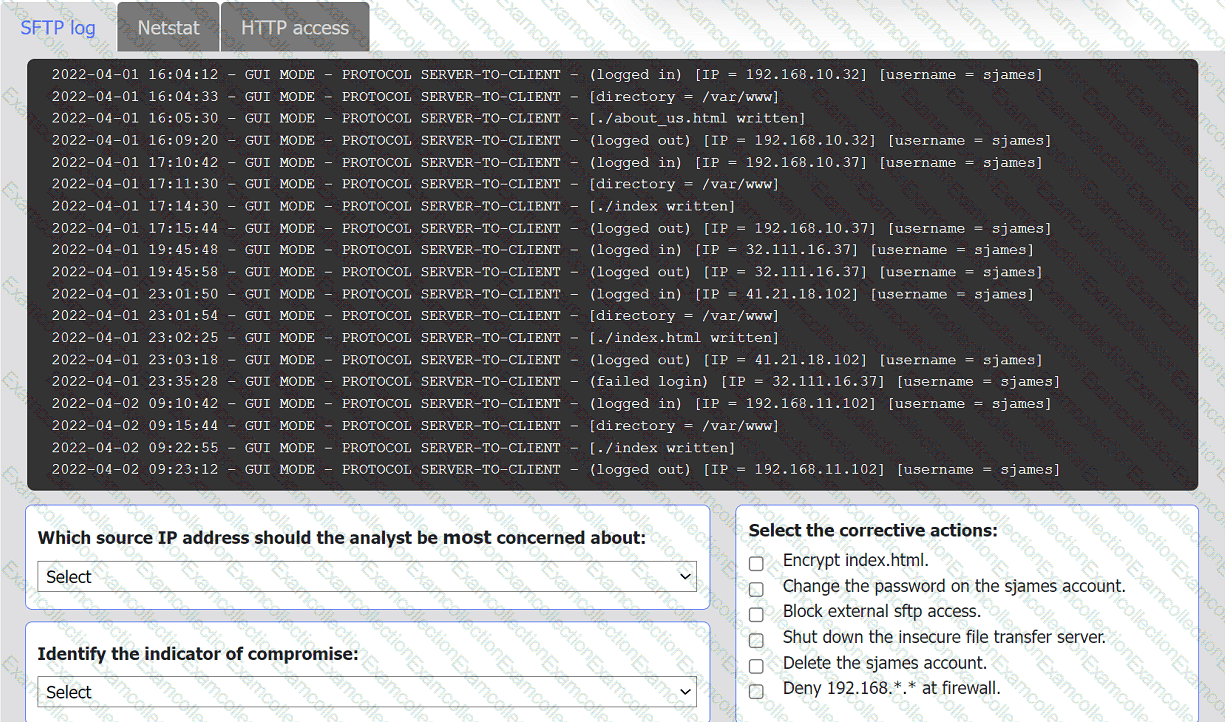
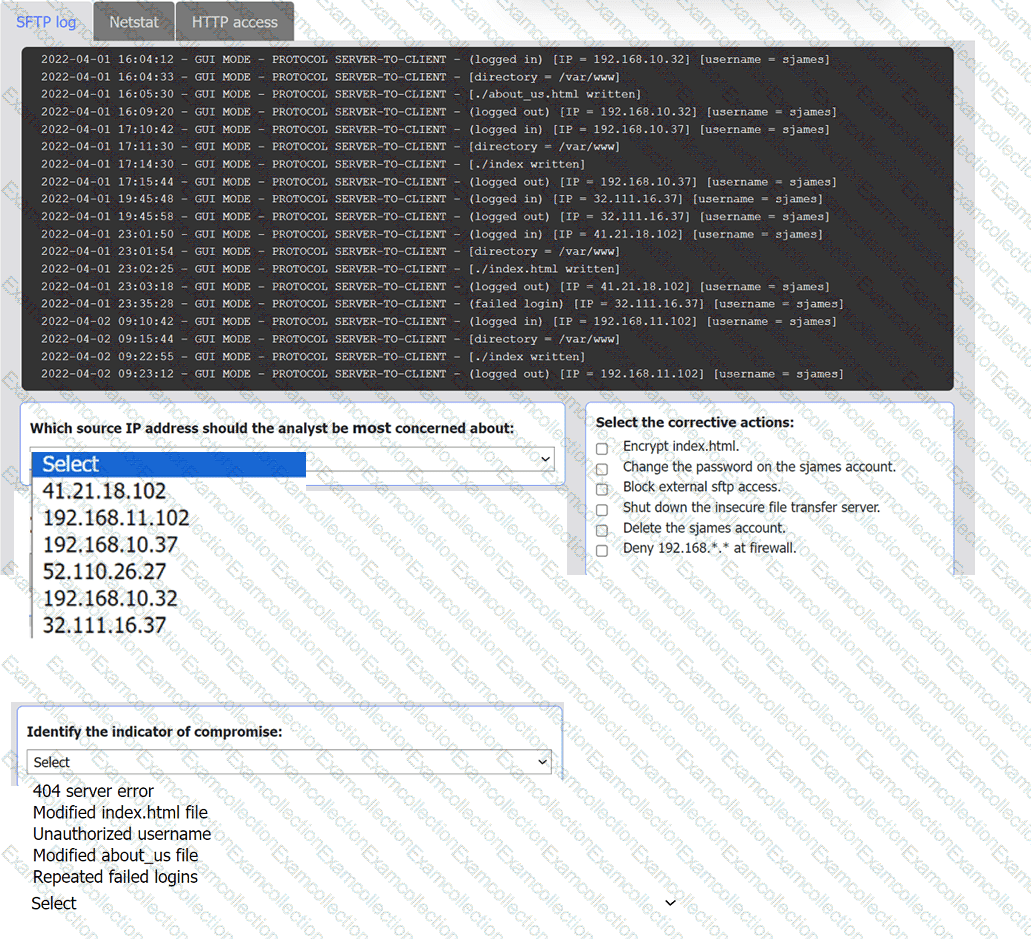
An organization's website was maliciously altered.
INSTRUCTIONS
Review information in each tab to select the source IP the analyst should be concerned
about, the indicator of compromise, and the two appropriate corrective actions.
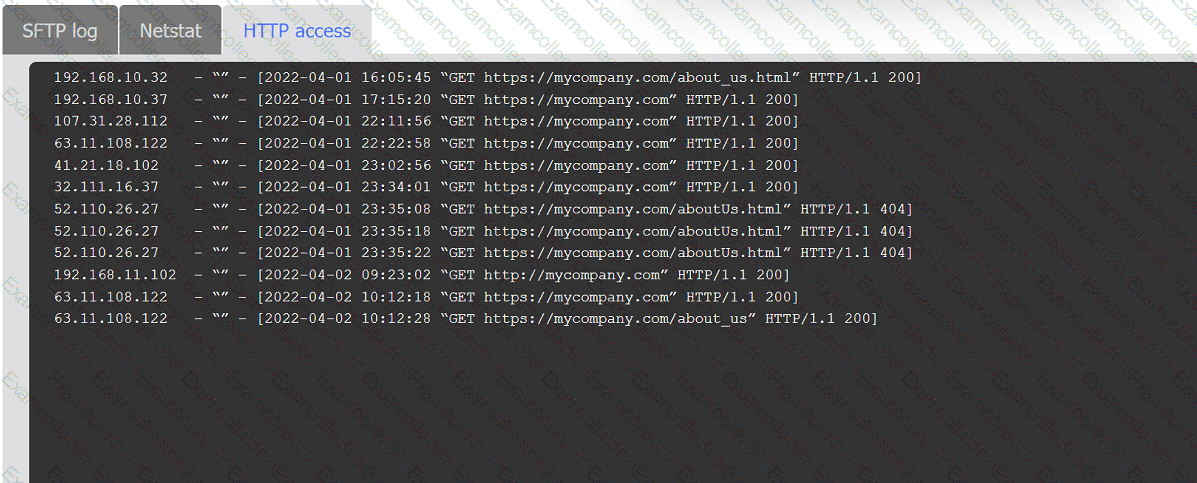
A web application team notifies a SOC analyst that there are thousands of HTTP/404 events on the public-facing web server. Which of the following is the next step for the analyst to take?
Which of the following actions would an analyst most likely perform after an incident has been investigated?
Which of the following risk management principles is accomplished by purchasing cyber insurance?
There are several reports of sensitive information being disclosed via file sharing services. The company would like to improve its security posture against this threat. Which of the following security controls would best support the company in this scenario?
A security analyst detects an email server that had been compromised in the internal network. Users have been reporting strange messages in their email inboxes and unusual network traffic. Which of the following incident response steps should be performed next?
Which of the following would a security analyst most likely use to compare TTPs between different known adversaries of an organization?
A security analyst has found a moderate-risk item in an organization's point-of-sale application. The organization is currently in a change freeze window and has decided that the risk is not high enough to correct at this time. Which of the following inhibitors to remediation does this scenario illustrate?
%77%77%77%2e%69%63%65%2d%70%74%69%63%2e%63%6f%6d
Which of the following would most likely explain this behavior?