Paloalto Networks CloudSec-Pro - Palo Alto Networks Cloud Security Professional
Total 258 questions
A customer has a requirement to restrict any container from resolving the name www.evil-url.com.
How should the administrator configure Prisma Cloud Compute to satisfy this requirement?
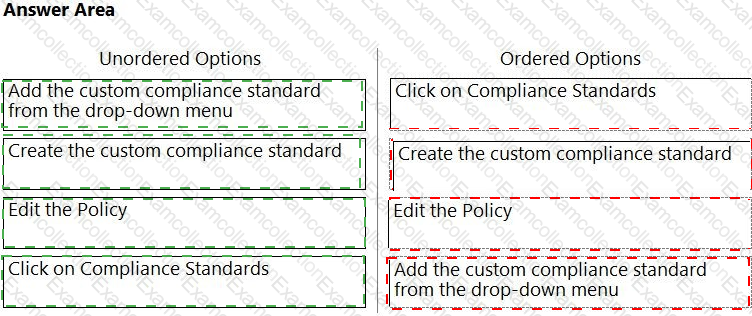
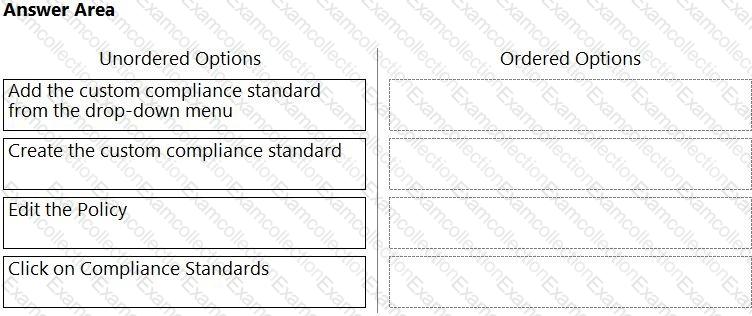
Which order of steps map a policy to a custom compliance standard?
(Drag the steps into the correct order of occurrence, from the first step to the last.)
What is the most reliable and extensive source for documentation on Prisma Cloud APIs?
Which two attributes are required for a custom config RQL? (Choose two.)
Which two services require external notifications to be enabled for policy violations in the Prisma Cloud environment? (Choose two.)
Which three elements are part of SSH Events in Host Observations? (Choose three.)
Web-Application and API Security (WAAS) provides protection for which two protocols? (Choose two.)
Which “kind†of Kubernetes object is configured to ensure that Defender is acting as the admission controller?
Which step should a SecOps engineer implement in order to create a network exposure policy that identifies instances accessible from any untrusted internet sources?
Which two actions are required in order to use the automated method within Amazon Web Services (AWS) Cloud to streamline the process of using remediation in the identity and access management (IAM) module? (Choose two.)