Paloalto Networks CloudSec-Pro - Palo Alto Networks Cloud Security Professional
Total 258 questions
The security auditors need to ensure that given compliance checks are being run on the host. Which option is a valid host compliance policy?
A Prisma Cloud Administrator needs to enable a Registry Scanning for a registry that stores Windows images. Which of the following statement is correct regarding this process?
What are the two ways to scope a CI policy for image scanning? (Choose two.)
The exclamation mark on the resource explorer page would represent?
A customer has a requirement to automatically protect all Lambda functions with runtime protection. What is the process to automatically protect all the Lambda functions?
A container and image compliance rule has been configured by enabling all checks; however, upon review, the container's compliance view reveals only the entries in the image below.
What is the appropriate action to take next?
Under which tactic is “Exploit Public-Facing Application†categorized in the ATT&CK framework?
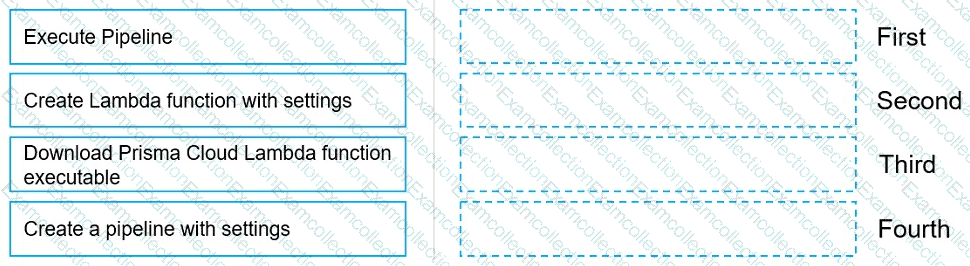
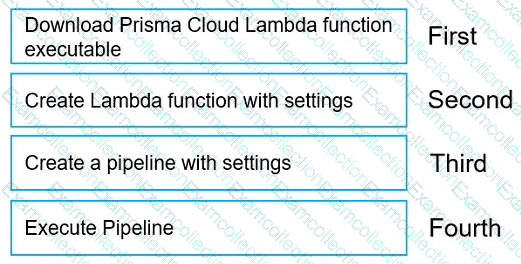
Move the steps to the correct order to set up and execute a serverless scan using AWS DevOps.
A customer has a requirement to terminate any Container from image topSecret:latest when a process named ransomWare is executed.
How should the administrator configure Prisma Cloud Compute to satisfy this requirement?
Which two bot categories belong to unknown bots under Web-Application and API Security (WAAS) bot protection? (Choose two.)



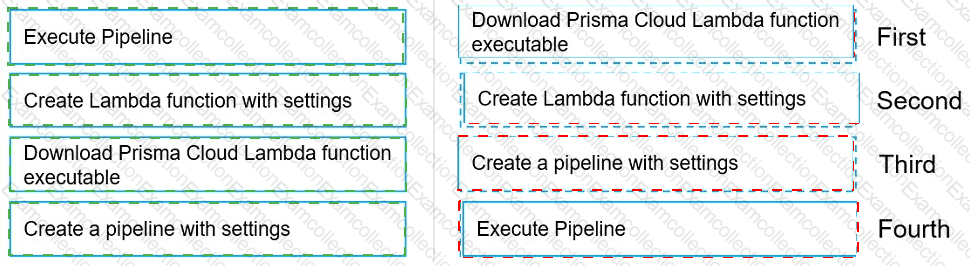
 Graphical user interface, text, application Description automatically generated
Graphical user interface, text, application Description automatically generated