EMC D-ISM-FN-23 - Dell Information Storage and Management Foundations 2023 Exam
What is an accurate description about Dell EMC VxBlock system?
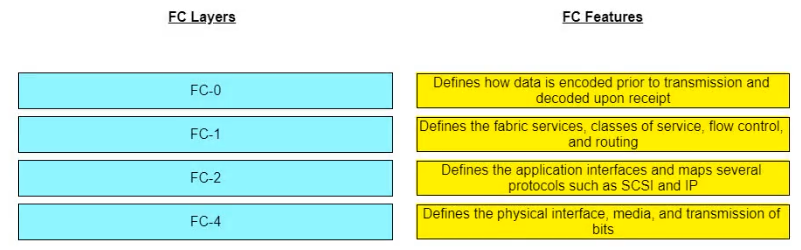
Match the Fibre Channel (FC) layers with their respective features.
What is a purpose of the policy engine in a data archiving environment?
What is the result of increasing the number of FC switches in a full mesh topology?
A company's assets are continuously under attack.
To deploy a security control mechanism to protect these assets, what should be considered?
What occurs during a Shared Technology Vulnerability threat?
Which data deduplication method would a cloud service provider use when storing back up data at their location?
Which management monitoring parameter involves examining the amount of infrastructure resources used?
The Ethernet switch has eight ports and all ports must be operational for 24 hours, from Monday through Friday. However, a failure of Port 4 occurs as follows:
Monday = 8 PM to 11 PM -
Wednesday = 7 PM to 10 PM -
Thursday = 6 AM to 12 PM -
What is the MTTR of Port 4?
A Fibre Channel switch has eight ports and all ports must be operational from 8 AM to 8 PM, Monday through Friday. However, a failure of Port 2 occurs on a particular week as follows:
Monday = 10 AM to 12 PM Wednesday = 4 PM to 9 PM Thursday = 4 PM to 7 PM
Friday = 3 PM to 6 PM Saturday = 9 AM to 1 PM
What is the availability of Port 2 in that week?