EMC D-PCR-DY-01 - Dell PowerProtect Cyber Recovery Deploy v2 Exam
Which three statements are true when performing a Dell Avamar Automated Recovery? (Choose three.)
After successfully completing the PoC for the Dell PowerProtect Cyber Recovery solution with Dell APEX Protection Storage All-Flash, the customer decided to purchase a license for the further use in the production environment.
Which information is required to generate the License Authorization Code (LAC) for the Dell APEX Protection Storage instance?
An IT manager needs to rerun a previously generated Dell PowerProtect Cyber Recovery report to verify the job activities for a specific period. They want to ensure that report includes the latest data.
What action should the IT manager take to rerun the report?
What is the purpose of the command crsetup. sh --install in the context of Dell PowerProtect Cyber Recovery software?
DRAG DROP
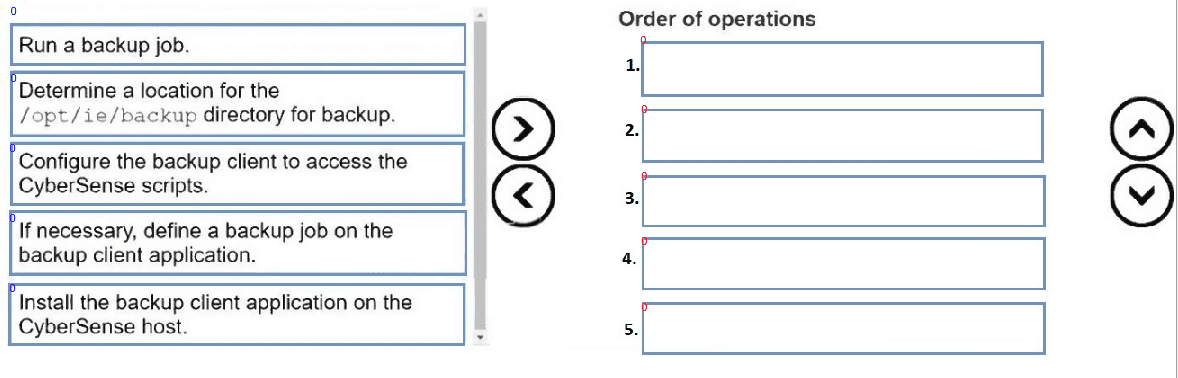
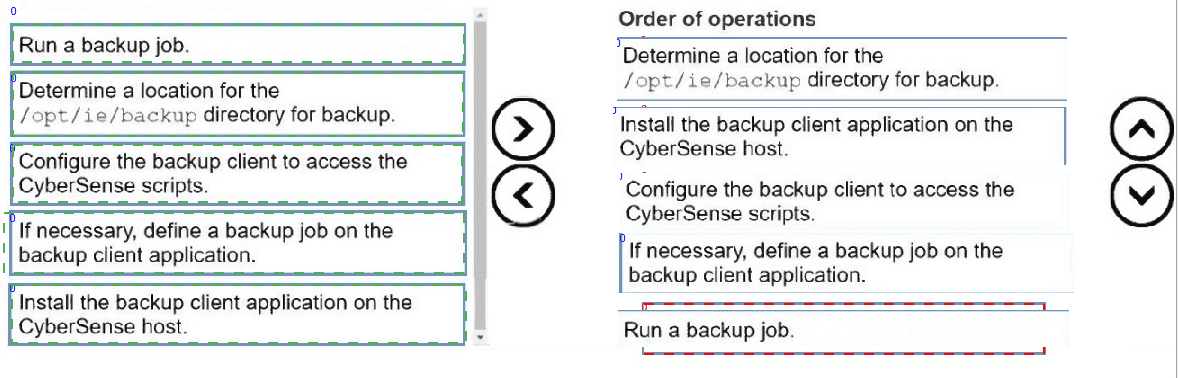
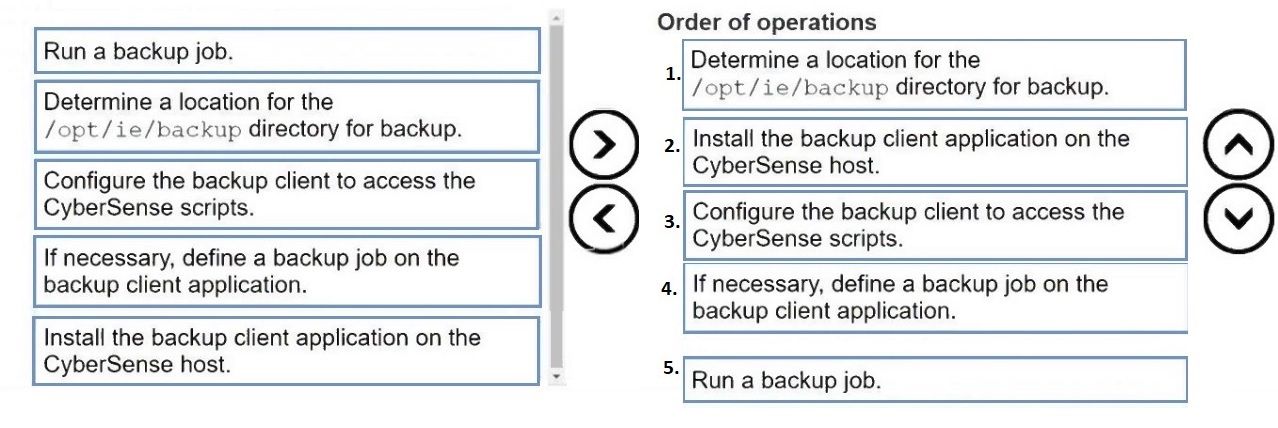
Put the following steps in the correct order to back up the Index Engines CyberSense configuration files:
Which is the best practice when securing PowerProtect Data Domain in Dell PowerProtect Cyber Recovery vault?
What is a pre-requisite for performing Automated Recovery of Dell PowerProtect Data Manager?
What is the minimum configuration required to deploy the Dell PowerProtect Cyber Recovery OVA in a VMware ESXi environment?
Which three checks are included in the upgrade precheck crsetup.sh –upgcheck command? (Choose three.)
What is the maximum number of PowerProtect Data Domains supported by Dell PowerProtect Cyber Recovery?



 C:\Users\Waqas Shahid\Desktop\Mudassir\Untitled.jpg
C:\Users\Waqas Shahid\Desktop\Mudassir\Untitled.jpg