EMC DEP-3CR1 - PowerProtect Cyber Recovery Exam
An administrator wants to create a read/write copy of the replicated data in the CR Vault.
Which task will accomplish the requirement?
A Cyber Recovery Administrator encounters a PowerProtect DD system that is offline and unavailable in the CR system.
What are the steps to remove this asset?
What are the possible connection states of the CR Vault?
What is the purpose of Denial of Service attacks?
Which are valid components of a Cyber Recovery policy?
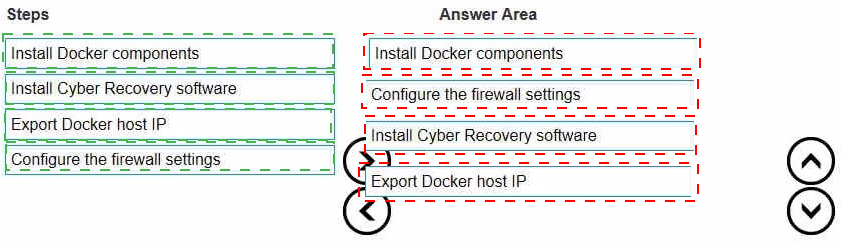
What is the correct sequence to install Cyber Recovery software on a physical host?
How many PIT copies can a sandbox contain?
Which feature can enable additional cyber resiliency measures to the Cyber recovery ecosystem?
A customer plans to have 1 policy which replicates data into the vault daily and takes a PIT copy, which is kept for 7 days and retention locked. The customer also plans to have one copy for the sandbox
environment to use for testing.
How many MTrees exist on the PowerProtect DD in the Vault?
Which appliance is supported as the replication target in the CR Vault?