EMC DES-1423 - Specialist - Implementation Engineer, Isilon Solutions Exam
What is the recommended networking design approach when planning subnets?
A company plans to build two Isilon clusters in an active-active disaster recovery environment. The initial requirement is to have one access zone for their Finance department. Which recommended directory structure meets the requirement?
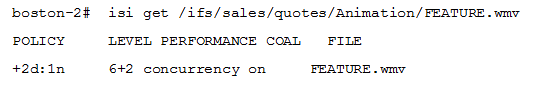
Based on the exhibit, what is the actual protection level of the FEATURE.wmv file?
What defines FEC link aggregation mode?
An Isilon administrator wants to minimize the use of root/admin access to their cluster. In additional, the administrator wants to create specific administrative accounts for specific cluster management activities in different access zones. An administrator of one zone should be able to view or configure objects in a different zone.
Which action will address the administrator’s requirements?
Which OneFS networking option enables Isilon for DNS multitenant functionality?
You have been tasked with designing SyncIQ policies for a systems administrator that requires failover and failback testing. What information should be provided to the administrator?
A user has recently left the company. After two weeks, the Isilon administrator receive a request to provide some files from the user’s directory called \ifs\user\John_Doe\development. The administrator then discovers that the required files have been deleted, but a snapshot of the directory is available.
After restoring the files from the snapshot, which additional step is necessary to access the files?
When reviewing the actual protection output of N+4/2, what does the number “4†represent?
What is the minimum storage space needed on a datastore to hold InsightIQ?



