EMC DES-2T13 - Specialist – Cloud Architect, Cloud Infrastructure Exam
What is the benefit of Hot Spare disks?
Which authentication and authorization feature is critical for service providers when supporting multi-tenancy?
A cloud architect is evaluating an organization’s need for encryption. Which type of encryption eliminates the requirement for key management?
SPECIAL INSTRUCTIONS REMINDER
The remaining questions are associated with two cases.
Each case has an introductory, descriptive passage (case text) that describes background information and requirements for a specific cloud based design. And each case has a set of six related, randomized questions. You will need to read the case text in order to answer the related questions correctly.
Given that there are two cases with six scored questions each, the total number of case-based scored questions is 12.
When you display each questions you can easily review the related case text in a pop-up window by clicking on the “Case†icon (shown below)
Case 4
Refer to the exhibit.
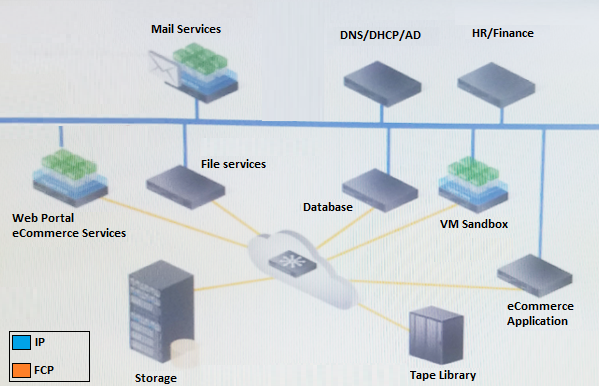
Your company is currently using a traditional SAN storage network. The server infrastructure is partially virtualized. There is a public cloud in place that is used to test development and application migration to cloud.
Business requirements:
Consolidate the network, storage, and compute resources
Simplify network management and storage provisioning
Maintain application performance
Need to share resources to reduce cost and improve efficiency
Other considerations:
Monitoring of protection SLAs
All transactions must be logged for auditing review
Users are validated using internal credentials
Refer to Case 4.
You are designing a private cloud to use VLANs to support compute-to-compute connectivity. The IT team has added a requirement to simplify the configuration management within the infrastructure.
What is a limitation related to VLANs for this requirement?
An organization wants to deploy SaaS applications in their cloud. The SaaS applications will be using
application HA to maintain up-time levels of 99,9%.
What should the cloud architect include in the design to support this up-time requirement?
In a cloud design, an architect has defined a separate trust zone for host management. The hosts will be
running open source hypervisors.
What should be included in the design deliverables to support this separate trust zone?
What would you describe is a key characteristic of cloud platform as a Service (PaaS)?
As a cloud architect, you are designing a CI solution to ensure that you isolate specific workloads for security.
What should you design for?
In which cloud design lifecycle phase is business value analysis performed?
SPECIAL INSTRUCTIONS REMINDER
The remaining questions are associated with two cases.
Each case has an introductory, descriptive passage (case text) that describes background information and requirements for a specific cloud based design. And each case has a set of six related, randomized questions. You will need to read the case text in order to answer the related questions correctly.
Given that there are two cases with six scored questions each, the total number of case-based scored questions is 12.
When you display each questions you can easily review the related case text in a pop-up window by clicking on the “Case†icon (shown below)
Case 4
Refer to the exhibit.
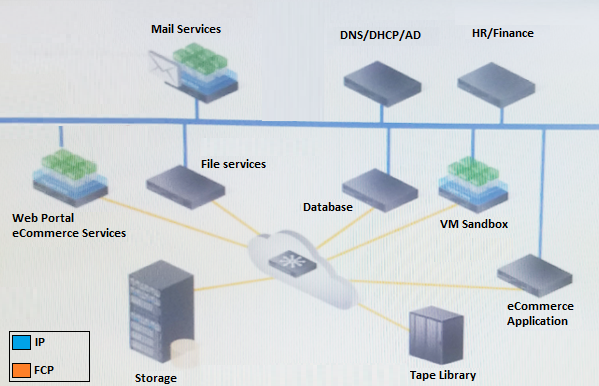
Your company is currently using a traditional SAN storage network. The server infrastructure is partially virtualized. There is a public cloud in place that is used to test development and application migration to cloud.
Business requirements:
Consolidate the network, storage, and compute resources
Simplify network management and storage provisioning
Maintain application performance
Need to share resources to reduce cost and improve efficiency
Other considerations:
Monitoring of protection SLAs
All transactions must be logged for auditing review
Users are validated using internal credentials
Refer to Case 4.
You are designing a brownfield cloud. You review the requirements and must determine the best, low-cost solution.
Which components must you include to meet the business requirements?



